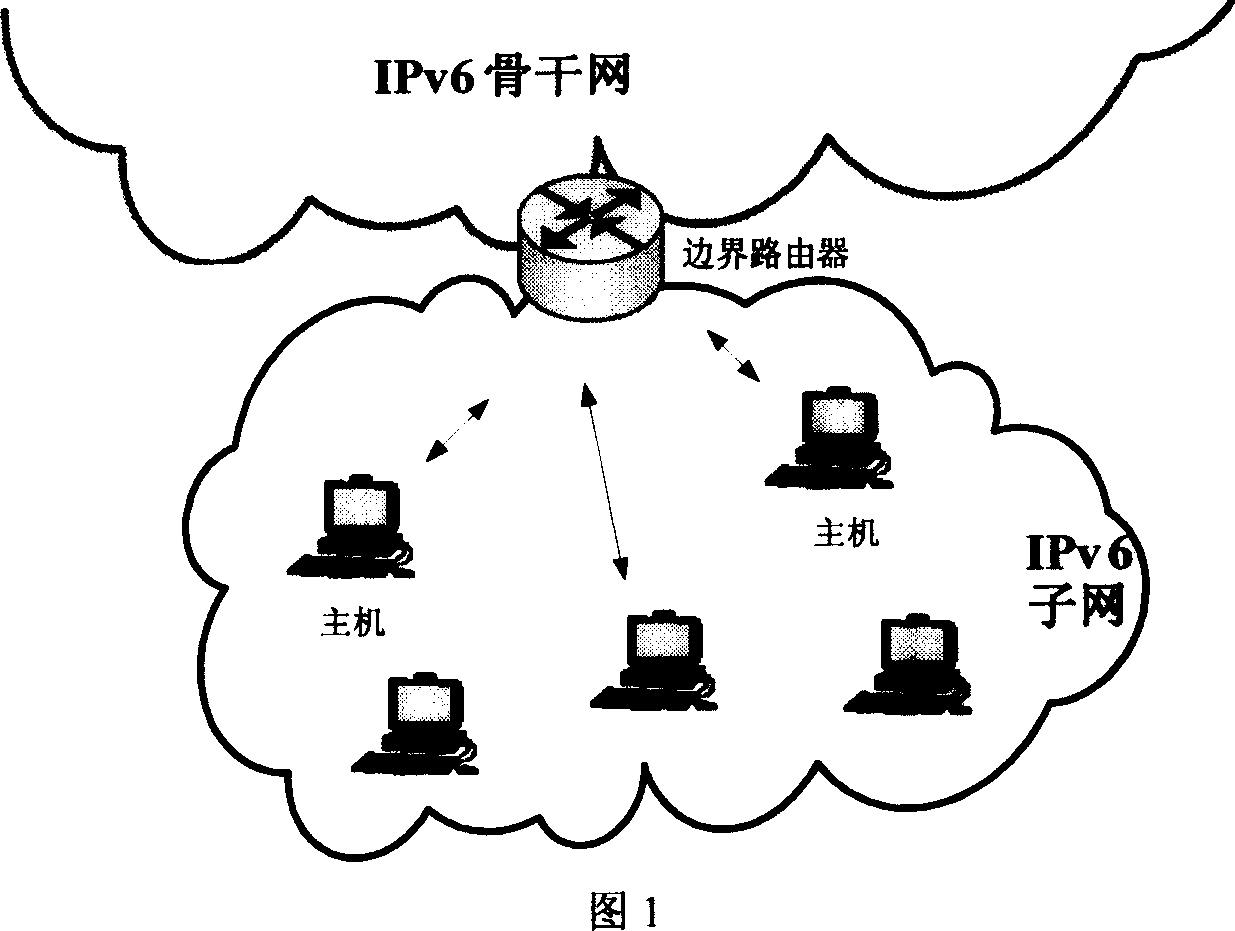
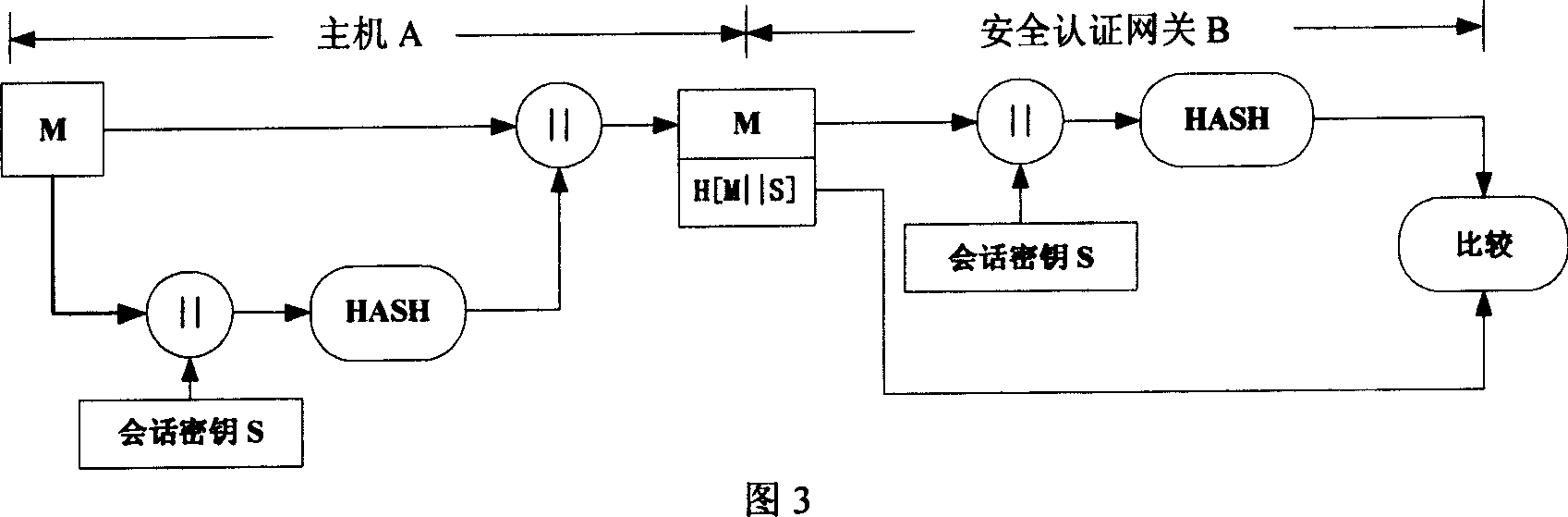
Method for preventing forgery of source address based on signature authentication inside IPv6 sub network
A signature authentication and source address technology, applied in the Internet field, can solve the problems of high implementation cost, coarse filtering granularity, coarse granularity, etc., and achieve the effects of preventing source address forgery, improving security, and high algorithm efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0066] In Figure 6, A is the victim, B forges the source address of A and sends a message to the external network, and C monitors and replays the message sent by A. When the source address authenticity authentication mechanism and anti-replay attack mechanism on the security authentication gateway are disabled, all forged and replayed packets can be sent to the external network smoothly. Once the function on the security authentication gateway is enabled, all the forged messages sent by B and the replayed messages sent by C are 100% filtered out by the security authentication gateway (10,000,000 messages are sent for testing). C's replay attack process is relatively simple, just monitor A's message and send it to the security authentication gateway. At this time, because the serial number of the replayed message has not been incremented, the security authentication gateway will recognize the message as a replayed message and discard it. The counterfeiting process of B can be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com