Camouflage communication method based on voice identification
A technology of speech recognition and communication methods, applied in speech recognition, speech analysis, secure communication devices, etc., to achieve the effect of strong security and high practical value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
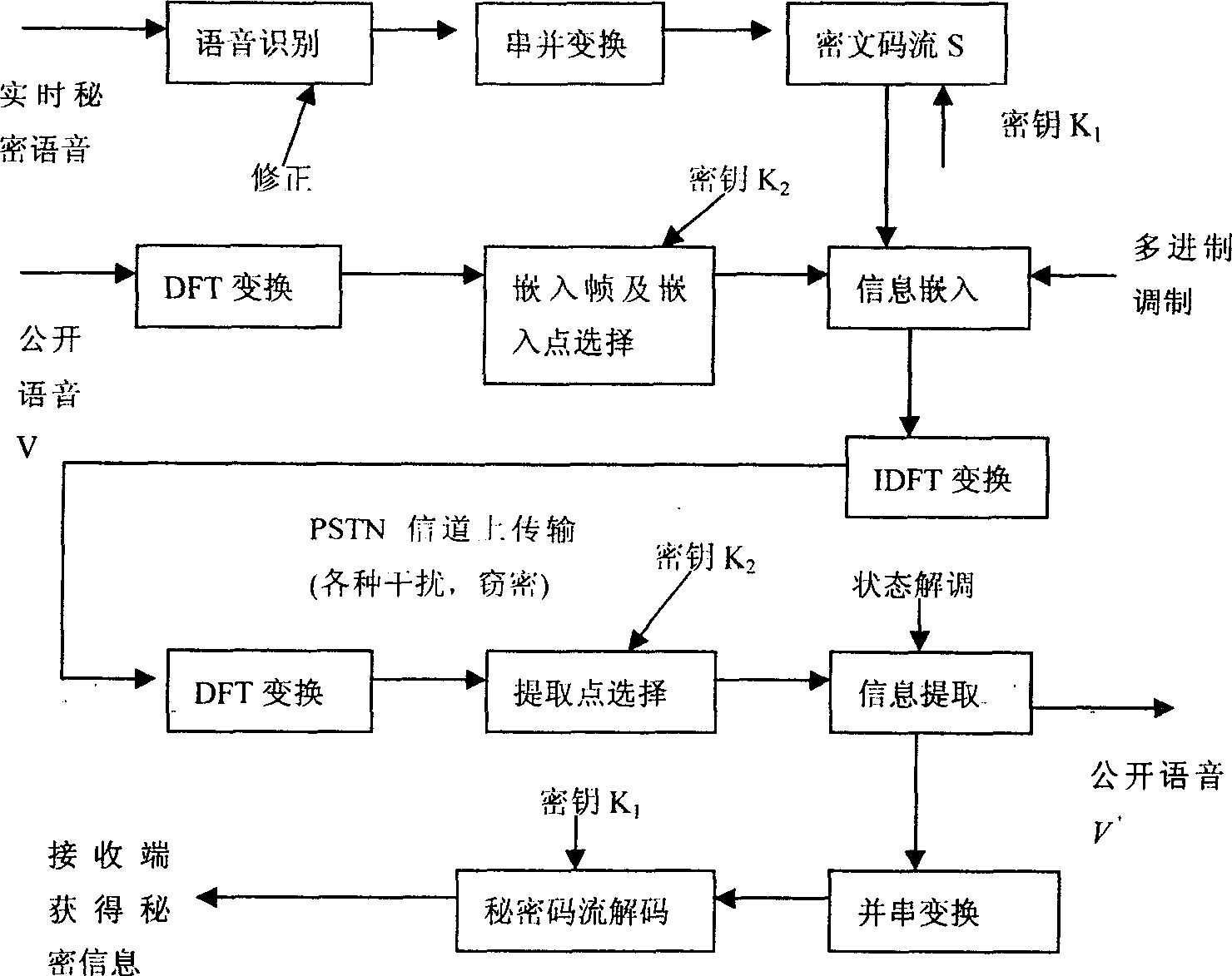
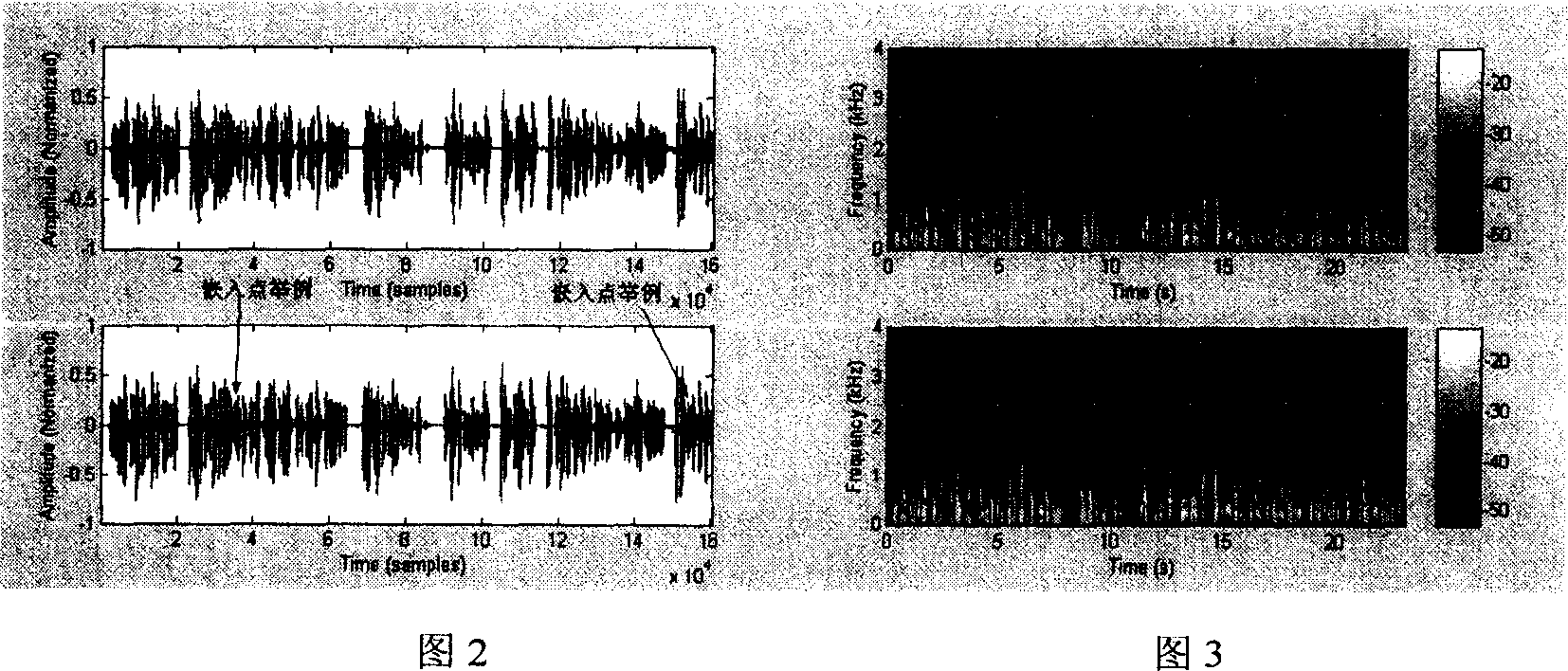
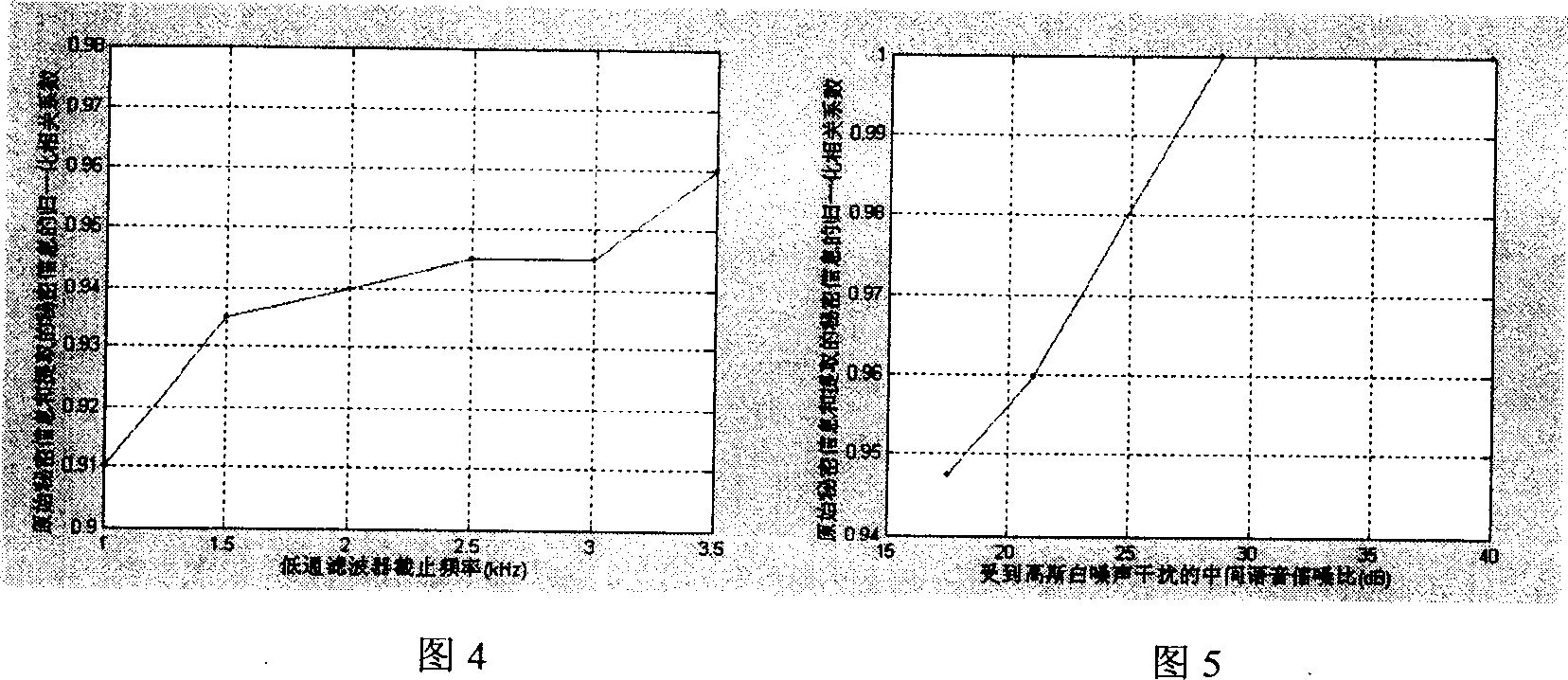
[0046]For systems that communicate securely, it is critical that secret information be delivered to its destination without error, and the form in which the information is delivered is secondary. This scheme proposes to use the method of speech recognition to process the secret voice, which greatly reduces the code rate of the secret voice, provides an embedding scheme with the highest transparency and robustness as possible, and realizes real-time confidential communication. From the perspective of information theory, the reason why speech recognition can compress the bit rate is that the speech contains not only semantic information, but also characteristic information such as the speaker's tone, intonation, and emotion; Features are "redundant" compared to semantic commands. Using speech recognition to convert secret speech into command text and then encode and transmit can greatly reduce the code rate of secret information. According to calculations, after using this schem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com