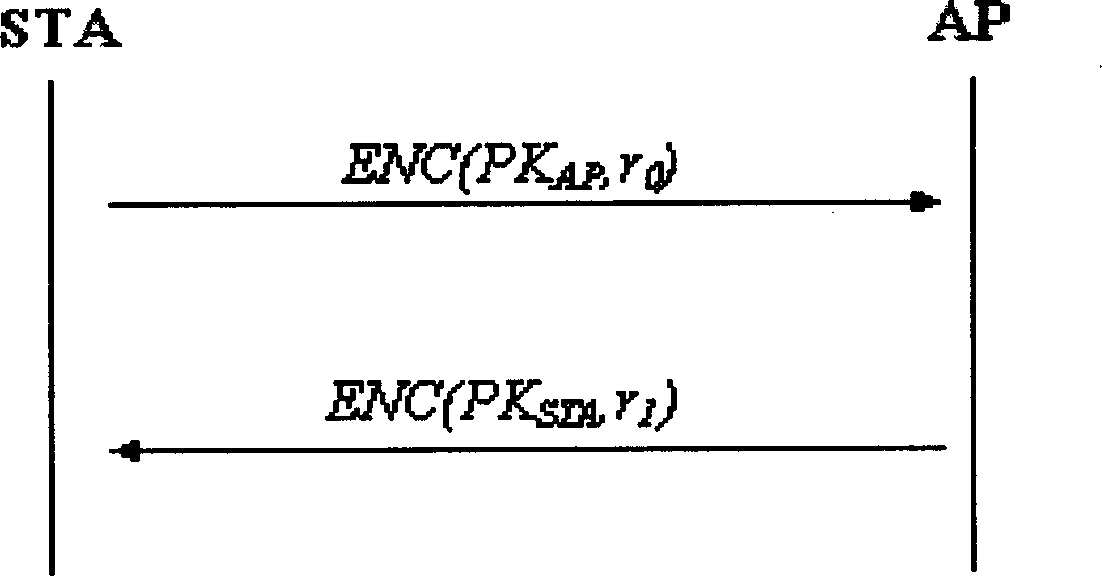Key agreement method in WAPI authentication mechanism
A technology of key negotiation and key, applied in the direction of synchronous sending/receiving of encrypted devices, data exchange through path configuration, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
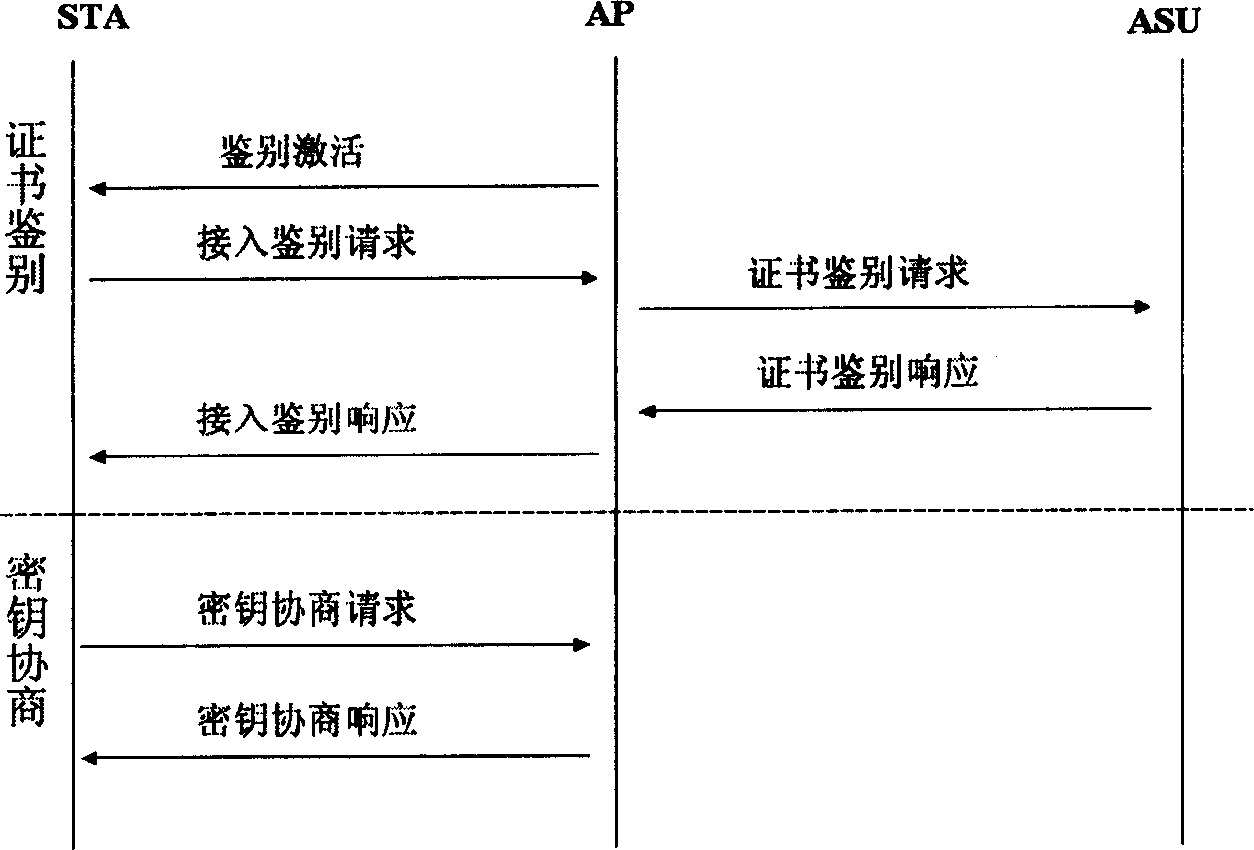
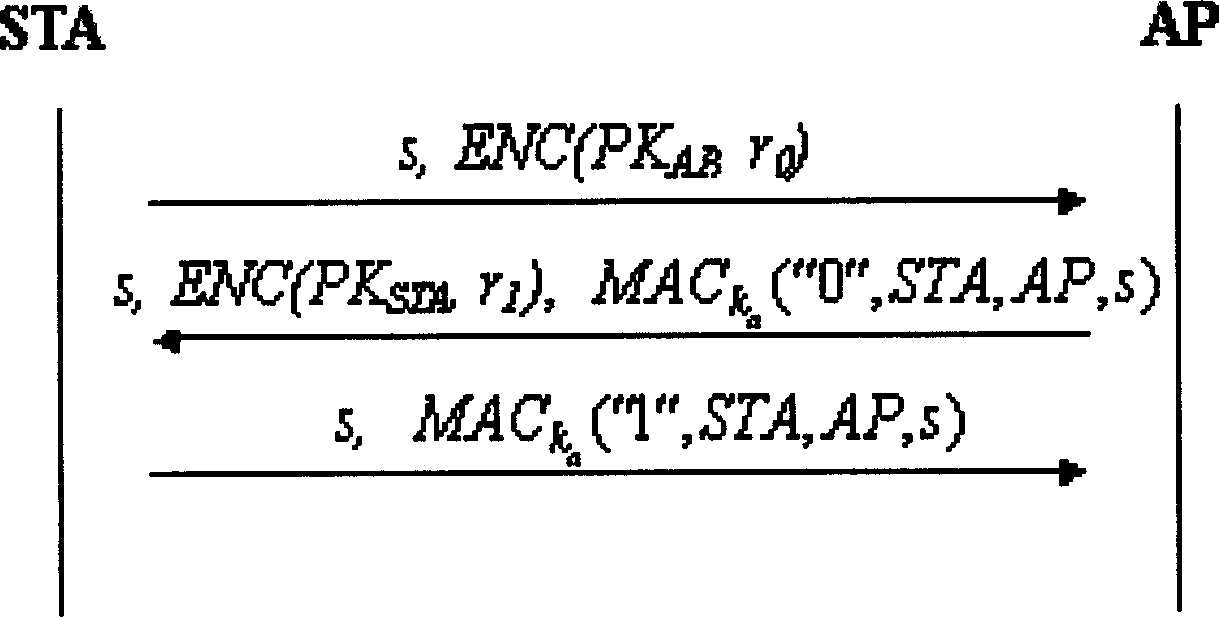
[0064] When implementing the WAPI authentication and security infrastructure of the wireless LAN, firstly, the client STA and the access point AP obtain their respective public-private key pairs through the key generation algorithm, and then apply for their respective public key certificates from the authentication service unit ASU. The certificate can adopt the format stipulated in the national standard GB15629.11 for wireless local area network. Then, start the protocol interaction of the wireless local area network authentication infrastructure WAI, which includes two parts: certificate authentication and key negotiation. Among them, the certificate authentication process adopts the steps specified in the national standard GB15629.11, and the specific interactive process of the key negotiation is as follows: image 3 The three messages shown are carried out.
[0065] 1. The first message is that the client STA sends a key negotiation request to the access point AP. The re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com