System and method for host volume mapping for shared storage volumes in multi-host computing environment
A main computer, computer technology, used in memory systems, various digital computer combinations, computer security devices, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
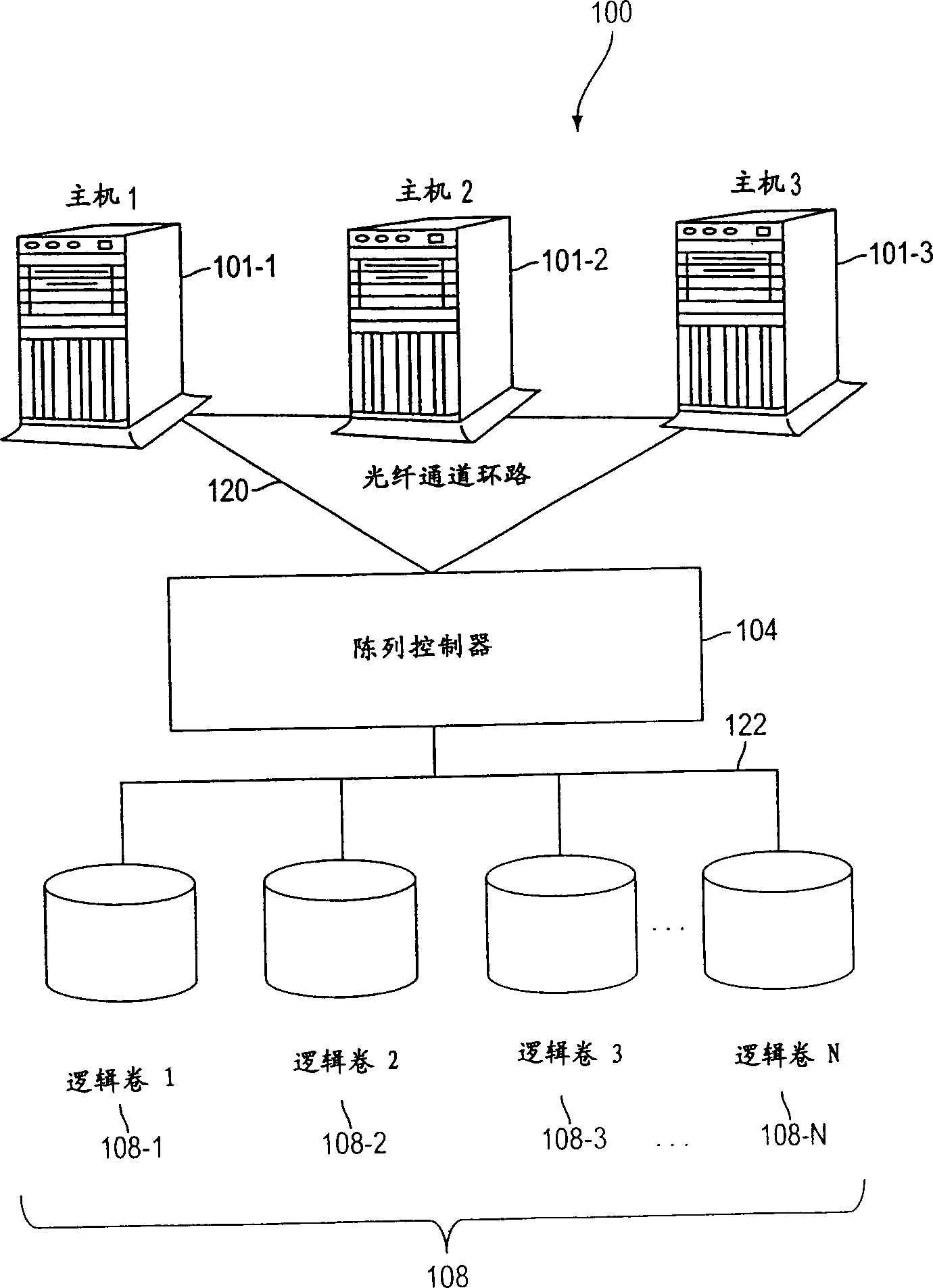
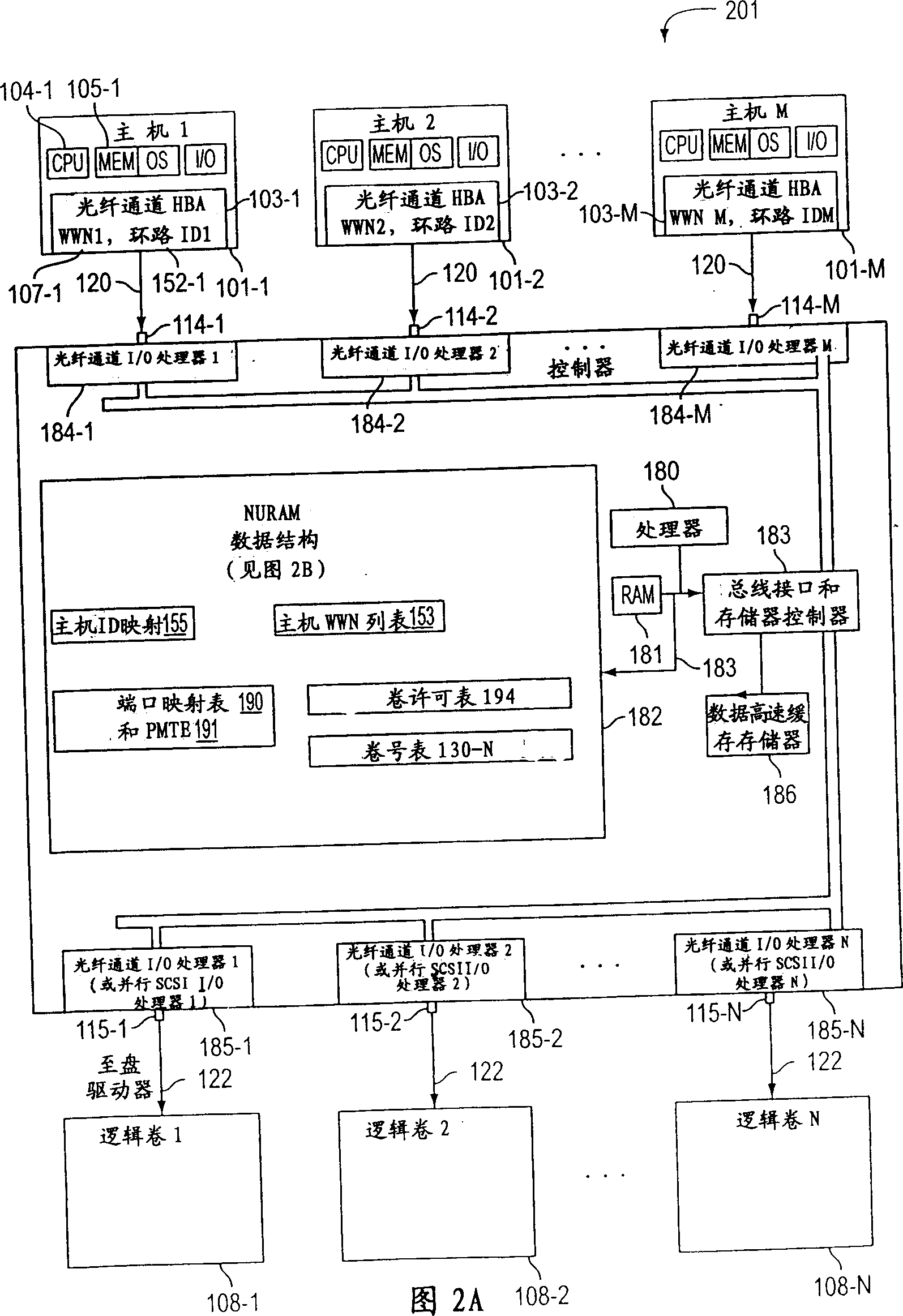
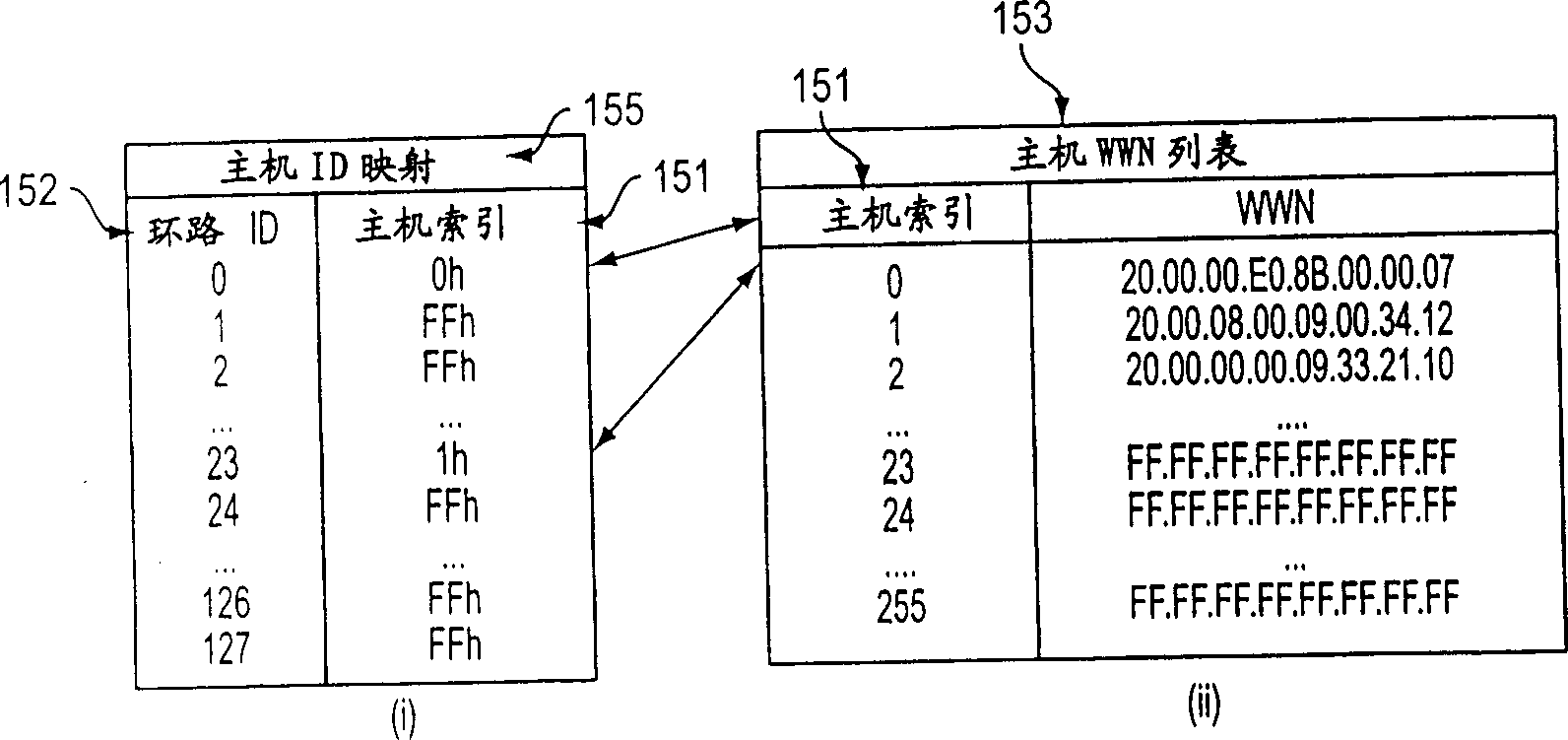
[0021]The present invention includes methods, apparatus, systems and computer program products for providing controlled access to storage volumes on an inventive storage system controller (eg, hard disk drive array controller 106). The structure, method and computer program product of the present invention, including the controller 106 and the memory subsystem 108 with access control, further solve the access and security problems existing in the traditional system and method, and its practice is to put the array controller on the Access to storage volumes 108, or controlled by the array controller, is restricted to a specific set of host computers identified by a unique identifier, such as a World Wide Name (WWN) 107, identified by the host The network interface of the computer 101 is associated with the host computer 101, or uses other identification means, as long as the identification means is unique among these interconnected devices. The present invention also provides l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com