Interactive method for re-selecting operating network to wireless local network
A wireless local area network and user terminal technology, applied in the field of selective access to the operating network, can solve problems such as the reason for accessing the business scope, no one has raised the specifics, and the reason for the tariff
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
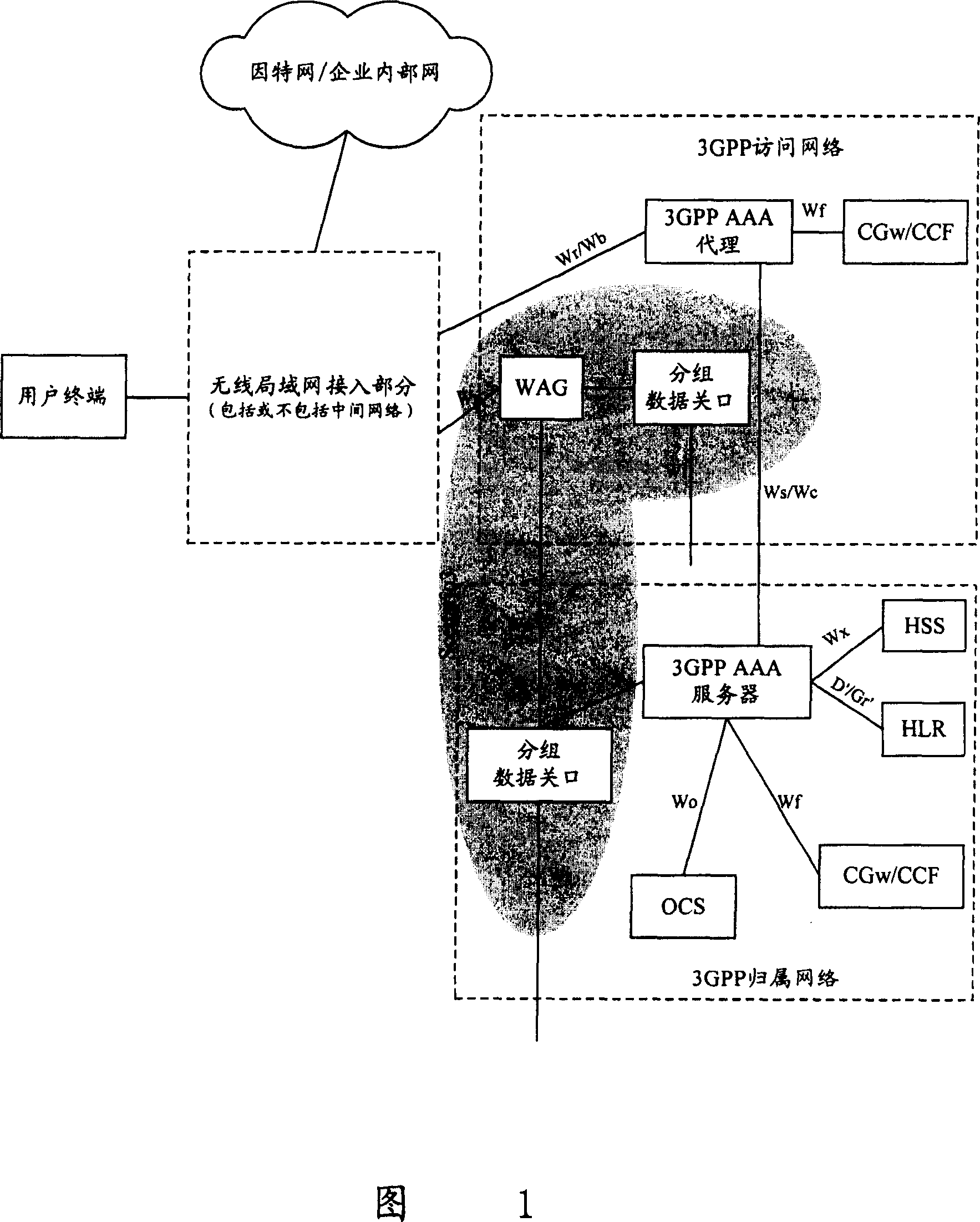
[0101] In this embodiment, after the home network receives the authentication request from VPLMN2, it directly performs the authentication operation, and the authentication is successful; and, after the authentication is successful, the home network first sends an access permission message to VPLMN2, and then sends the VPLMN1 sends a disconnection message; correspondingly, the WLAN access network first receives an access permission message. In addition, in this embodiment, only the current user is allowed to access one connection at the same time. Then, in this embodiment, the process for the WLAN user terminal to reselect the mobile communication operator network includes the following steps:
[0102] Step 11: The current WLAN user terminal determines that it needs to access the VPLMN2, and confirms the domain name or identifier of the VPLMN2.
[0103] Step 12: The WLAN user terminal sends an access authentication request to the WLAN access network without affecting the exis...
Embodiment 2
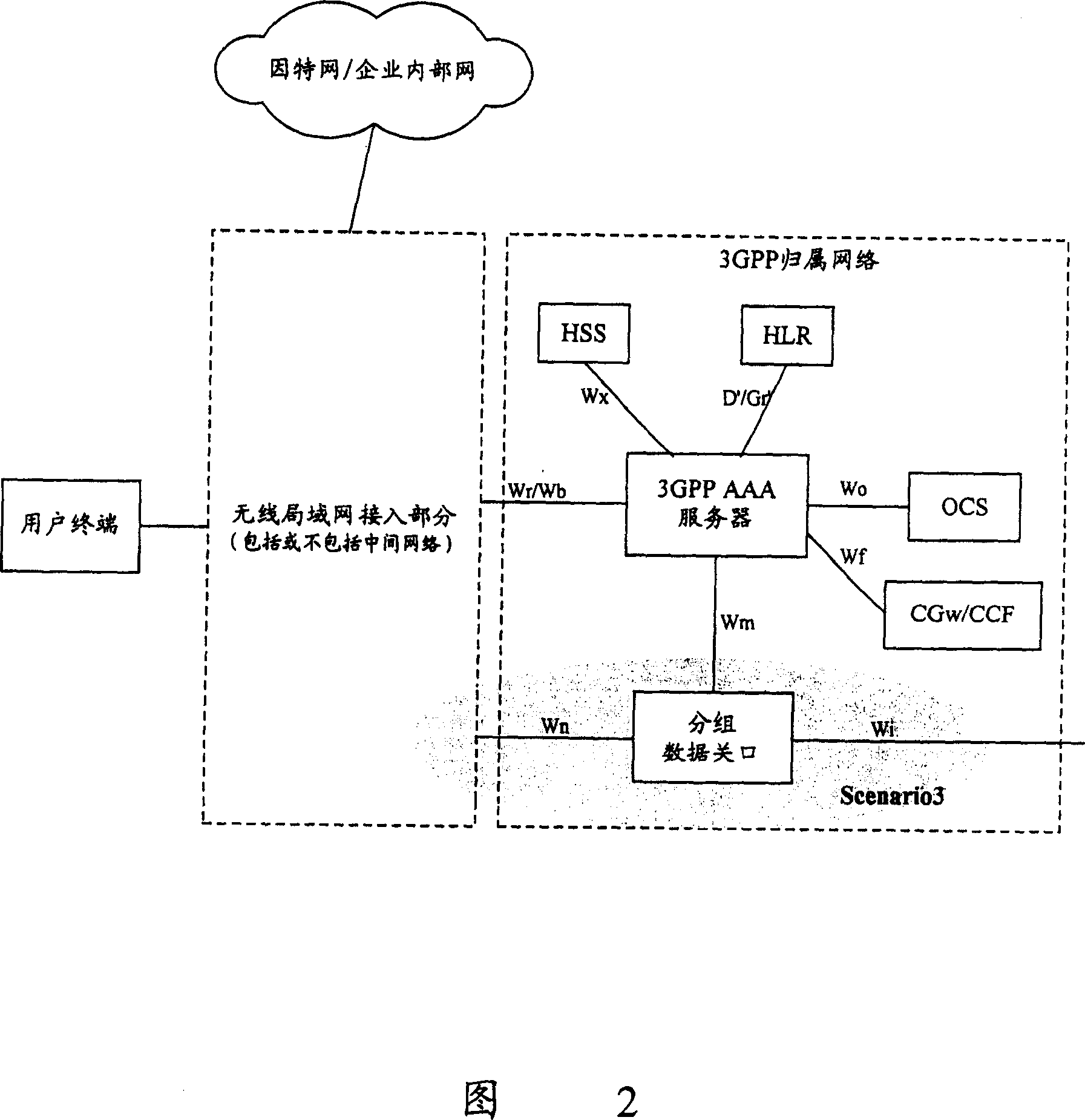
[0114] In this embodiment, after the home network receives the authentication request from VPLMN2, it directly performs the authentication operation and the authentication is successful; after the authentication is successful, the home network simultaneously sends an access permission message to VPLMN2, and sends a disconnect message to VPLMN1. connection message; and, the WLAN access network first receives the access permission message. In this embodiment, only the current user is allowed to access one connection or the user indicates to switch from an existing connection to a new connection. Then, the process for the WLAN user terminal to reselect the mobile communication operator network in this embodiment is basically the same as that in the first embodiment, except that step 28 is different from step 18 in the first embodiment.
[0115] Steps 21-27: are exactly the same as all descriptions of steps 11-17 in the first embodiment.
[0116] Step 28: The home network sends a...
Embodiment 3
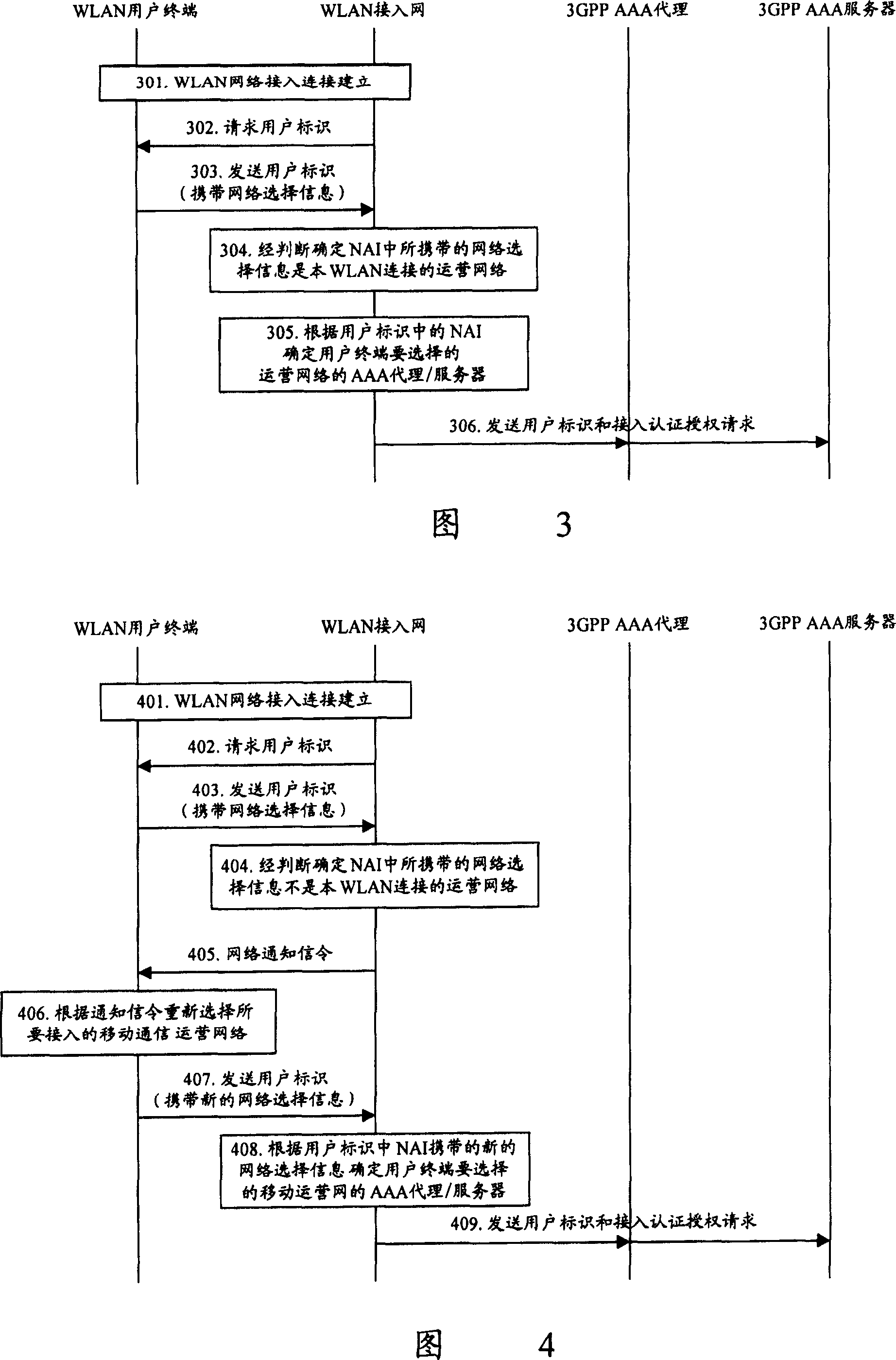
[0118] In this embodiment, after the home network receives the authentication request from VPLMN2, it directly performs the authentication operation and the authentication is successful; after the authentication is successful, the home network simultaneously sends an access permission message to VPLMN2, and sends a disconnect message to VPLMN1. connection message; and, the WLAN access network first receives the disconnection message. In this embodiment, only the current user is allowed to access one connection or the user indicates to switch from an existing connection to a new connection. Then, the process for the WLAN user terminal to reselect a mobile communication operator network in this embodiment is basically the same as that in Embodiment 1, except that Step 38 and Step 39 are different from Steps 18 and 19 in Embodiment 1.
[0119] Steps 31-37: are exactly the same as all descriptions of steps 11-17 in Embodiment 1.
[0120] Step 38: The home network sends an access ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com