Method for back-up protection of CMOS data
A data and backup technology, applied in the direction of preventing unauthorized use of memory, etc., can solve problems such as trouble for network administrators, locked computers, and unusable machines, so as to reduce the possibility of CMOS being invaded, easily crack passwords, and improve security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
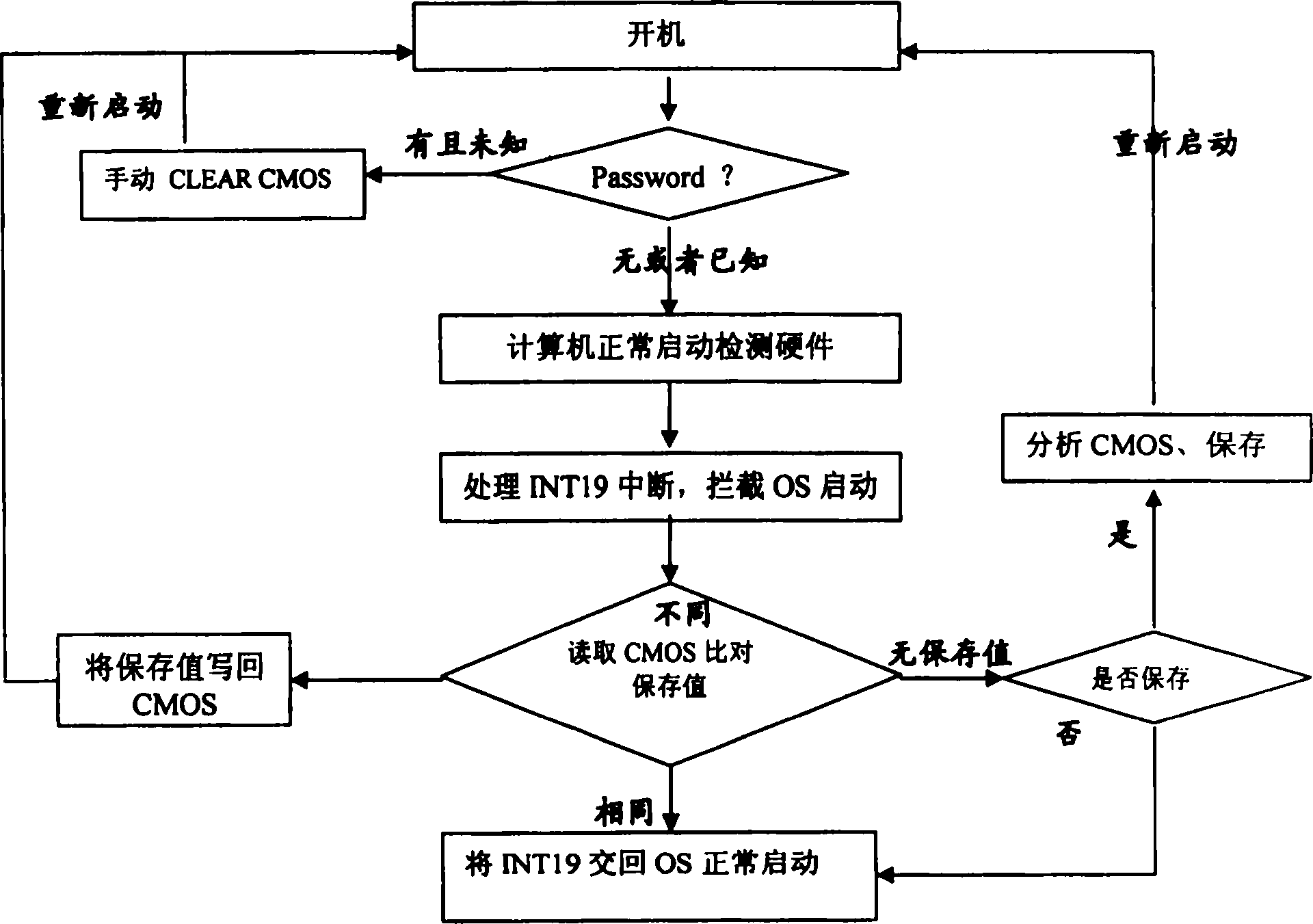
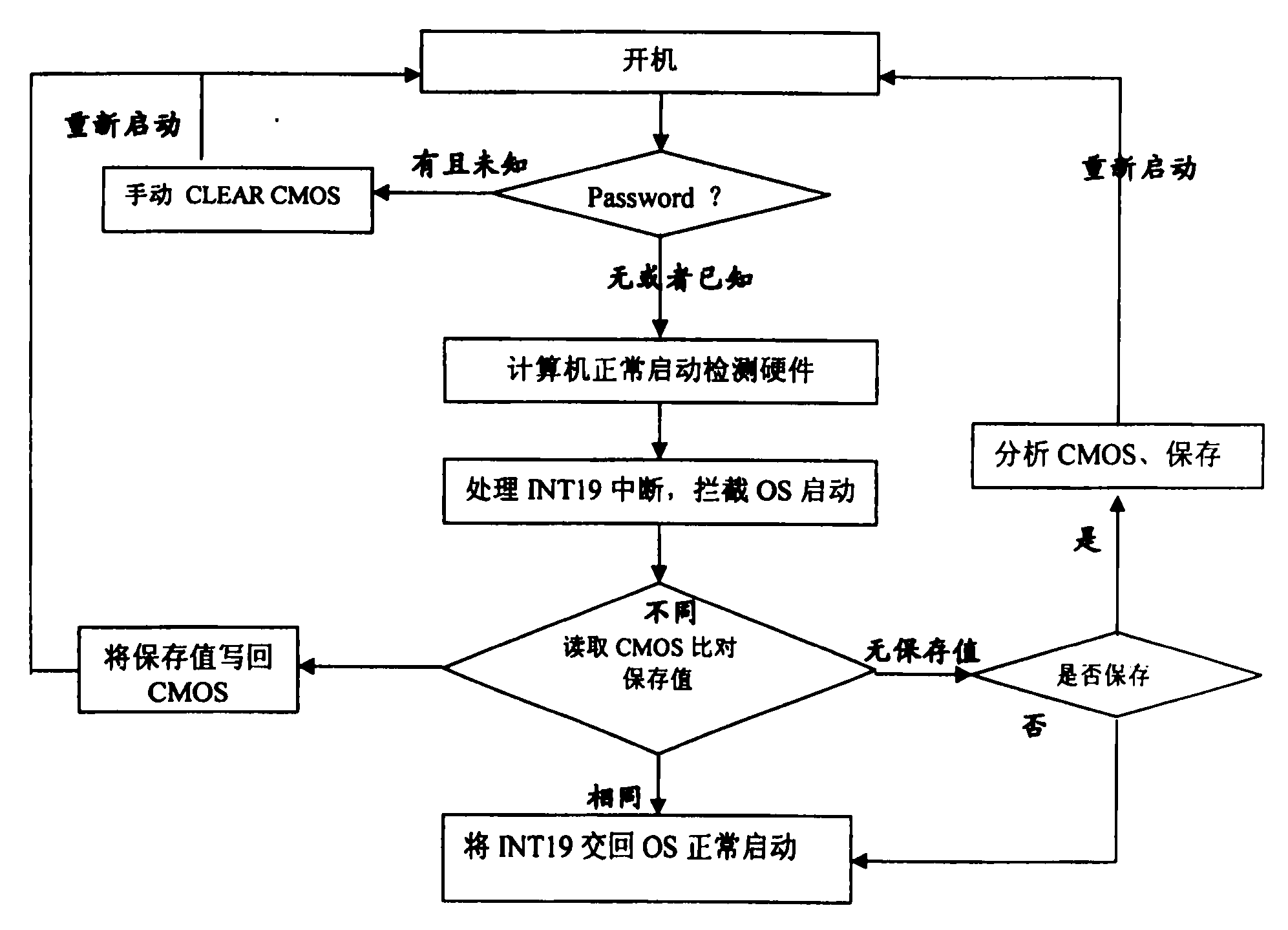
[0019] Such as figure 1 As shown in the flowchart, the method for backup protection of CMOS data according to the present invention comprises the steps:
[0020] The computer starts up;
[0021] Enter the password to make the computer start to detect the hardware normally;
[0022] Handle interrupt events and intercept the startup of the operating system;
[0023] Read the BIOS setting data stored on the hard disk and compare it with the BIOS data in the CMOS; the comparison results can be divided into the following situations:
[0024] (1) If there is no BIOS setting data on the hard disk, then save the BIOS data in the CMOS on the hard disk;
[0025] (2) If the BIOS setting data on the hard disk is inconsistent with the BIOS data in the CMOS, write the data on the hard disk to the CMOS BANK, then restart and turn on the computer.
[0026] (3) If the BIOS setting data on the hard disk is consistent with the BIOS data in the CMOS, then the interrupt event is returned to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com