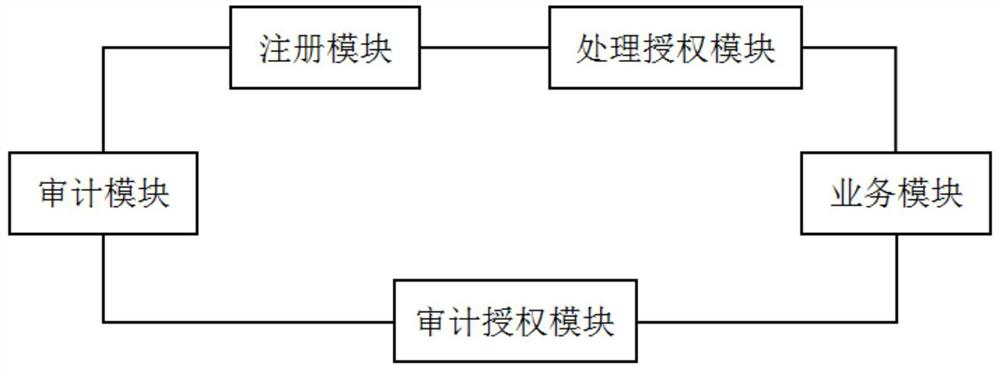
TEE-based privacy protection distributed account book auditing method and system
A privacy-preserving and distributed technology, applied in the field of privacy-preserving distributed ledger auditing methods and systems, can solve problems such as the inability of auditing efficiency to adapt to the magnitude of big data, low auditing efficiency, and lack of universal value, achieving efficient and Generalized audit function, ideal efficiency, effect of enhancing robustness and completeness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
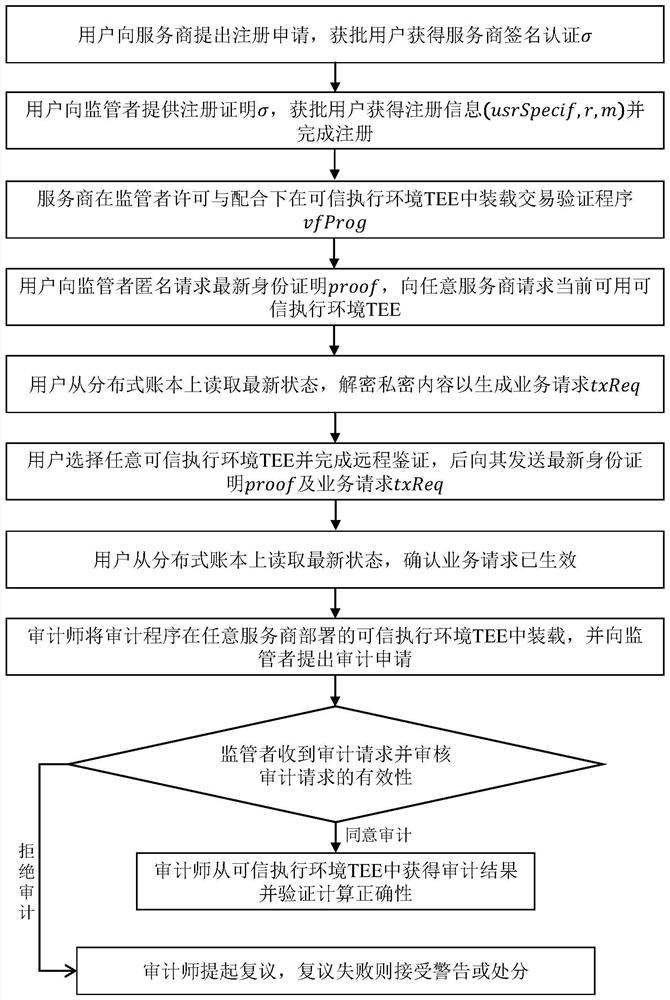
[0067] like figure 1 As shown, the TEE-based privacy-preserving distributed ledger auditing method includes the following steps:
[0068] Step S1: The user submits a registration application to the service provider, and the approved user obtains the service provider's signature certification σ.
[0069] In this embodiment, the user presents the service provider with personal identity information and relevant certification materials, including but not limited to pictures, text (WORD, PDF, etc.), and the service provider will identify the user's unique identifier U after the application materials are approved. Make a digital signature σ=∑.Sig(ssk P , U), if a user can register multiple different accounts with a single service provider, a timestamp or other identification can be added to the signature content to distinguish it. After the user receives the signature, verify ∑.Vf(spk P , U, σ) = 1;
[0070] Among them, ∑ is the signature scheme used by P, Sig is the signature a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com