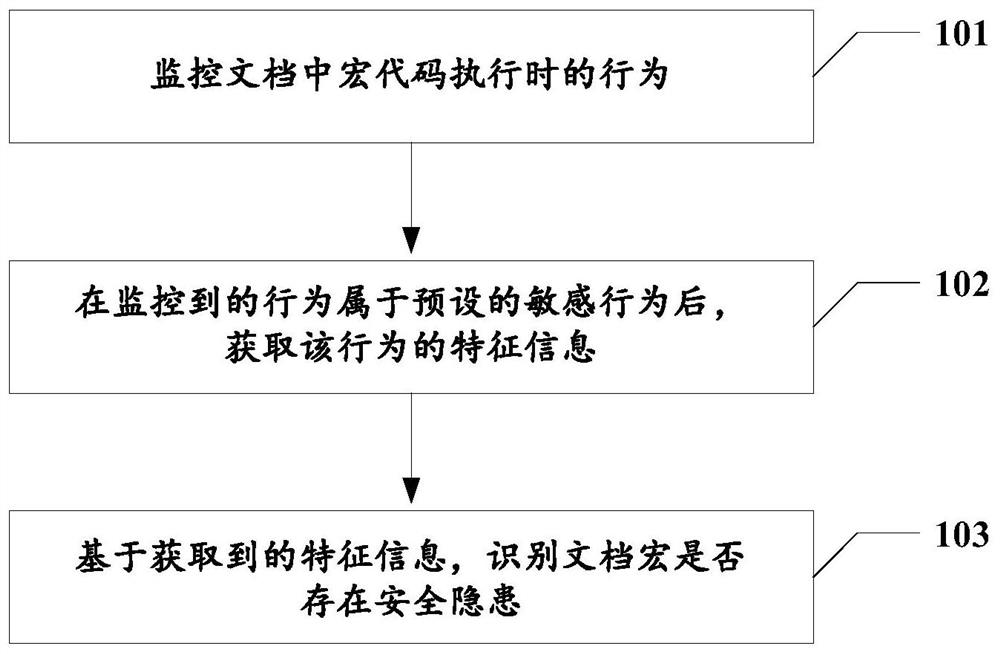
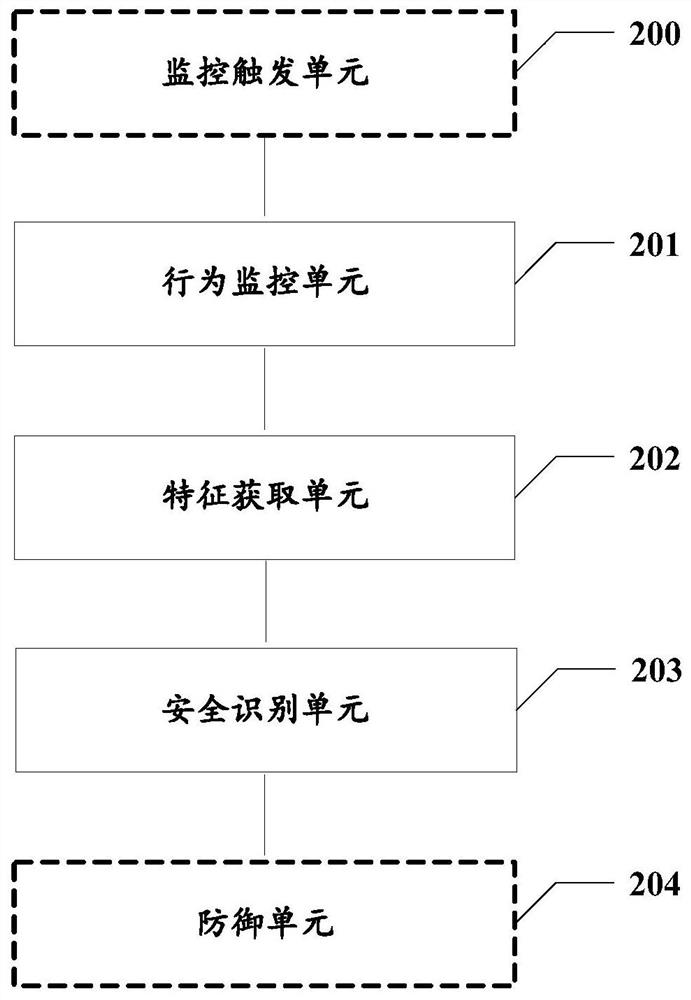
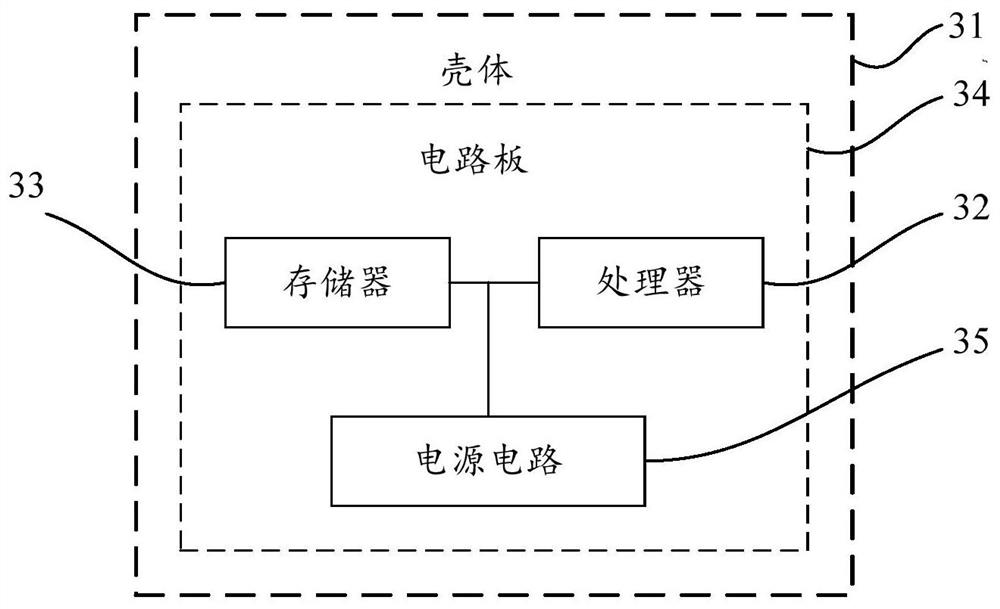
Document macro security detection method and device, electronic equipment and storage medium
A technology of security detection and documentation, applied in the field of computer security, can solve the problems of low user threshold, low detection rate, simple code confusion, etc., and achieve the effect of good anti-attack measures and reduced losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0069] Example 1. Xiao Wang received the XXX Daily.xlsx from his colleague Xiao Li (this document has been infected with an infectious virus). The company purchased the data statistics plug-in integrated in the document, and macros have been enabled by default.
[0070] Step 1: Xiao Wang double-clicks to open the daily newspaper, and the malicious macro code in the infected document starts to execute immediately.
[0071] Step 2: After the malicious macro code is executed, it starts to traverse other documents under the system to infect, which must involve the writing of files. At this time, the protection module will pop up a window to remind the user that the document is writing to other documents. Whether to intercept. (If yes, skip directly to step 4)
[0072] Step 3: The malicious behavior is not terminated, the file is written successfully, and the written data contains known infection-type file characteristics, which can be warned by the protection module later.
[00...
example 2
[0074] Example 2. The user opens the phishing document (XXXXXXX).
[0075] Step 1: There are words in the document that lure users to enable macros, and the user clicks to enable macros.
[0076] Step 2: The malicious macro code starts to execute automatically. When the process starts, it will execute the protection module initialization monitoring logic, and start monitoring the access interface that the preset malicious behavior depends on.
[0077] Step 3: The document starts to access the malicious IP (91.240.118.172), and during the process of downloading the core file to the local execution, the protection module will detect the malicious IP, block its access interface calling process and return an error.
[0078] Step 4: An error occurs in the initialization logic of the malicious macro code, the core file cannot be downloaded, and subsequent malicious behavior cannot be generated.
[0079] Correspondingly, the embodiment of the present invention also provides a docume...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap