Enhanced inter-satellite networking authentication method based on location key
A technology of inter-satellite networking and authentication method, which is applied in the field of satellite communication, can solve the problems of high exposure of satellite network links, inability to guarantee the security of inter-satellite session keys, and low protocol efficiency, and achieve an efficient inter-satellite authentication mechanism, Realize the effect of fast networking between satellites and reduce communication delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
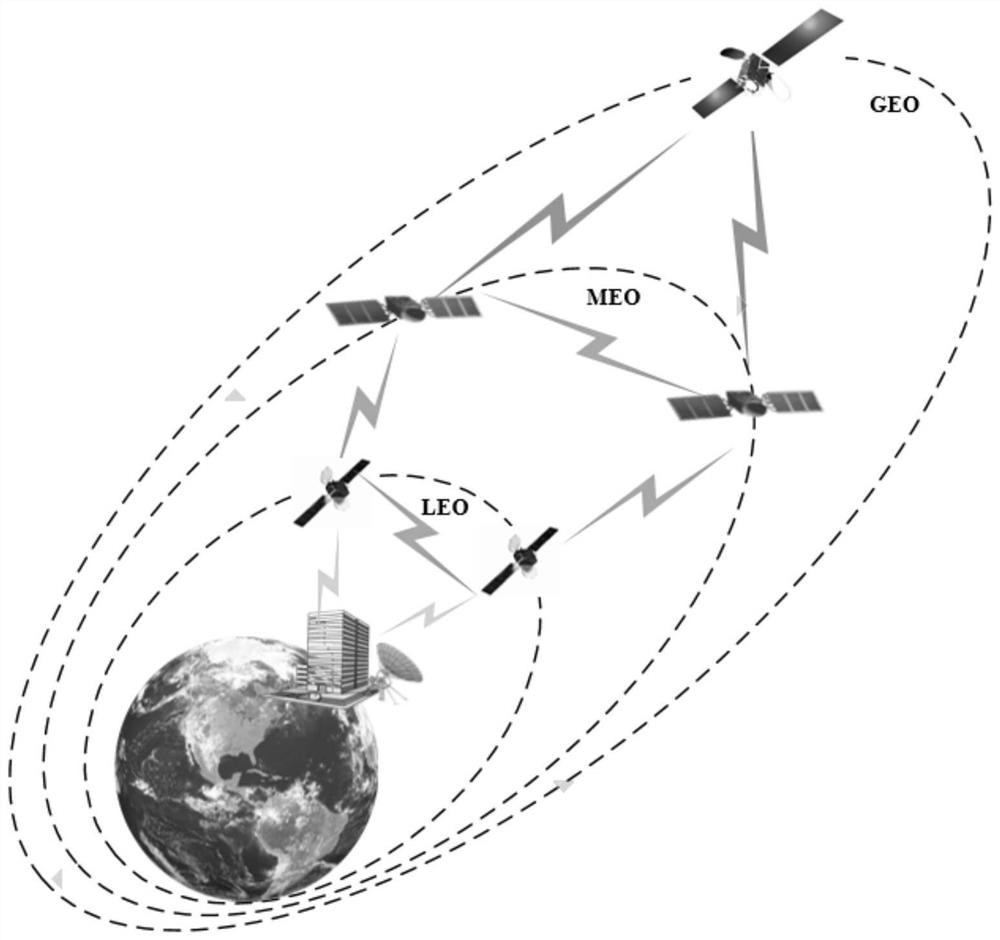
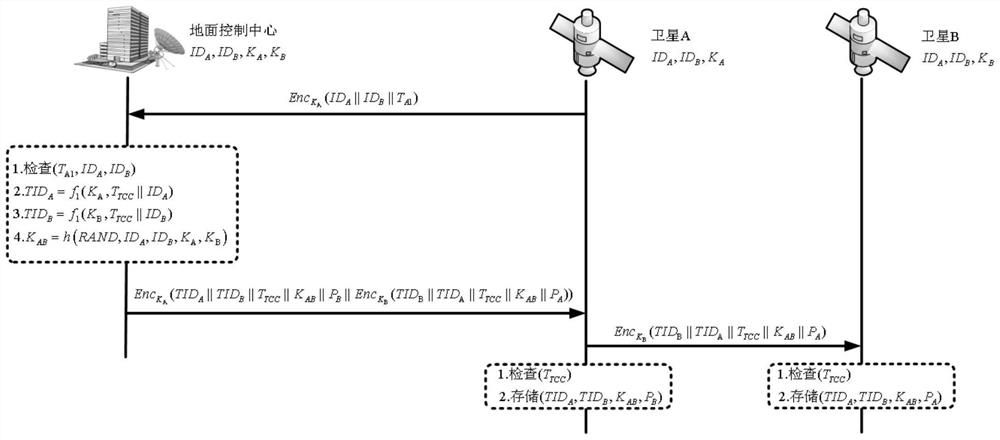
[0060] See figure 1 and figure 2 , figure 1 A schematic flowchart of an enhanced inter-satellite networking authentication method based on a location key provided by an embodiment of the present invention, figure 2 This is an architecture diagram of an enhanced satellite security networking authentication method based on a location key under a sky-earth integrated network provided by an embodiment of the present invention.
[0061] The method of this embodiment implements identity authentication and key negotiation based on the location key, and almost all satellites can meet the needs of the inter-satellite networking method. Specifically, the method in this embodiment can be applied to various types of satellites, including any two satellites among the low-orbit satellite LEO, the medium-orbit satellite MEO, and the high-orbit satellite GEO, such as figure 2 shown, and satellites launched by different organizations; in the case where the two networked satellites do not...
Embodiment 2
[0114] On the basis of Embodiment 1, this embodiment provides an inter-satellite networking authentication method in which the orbital parameters of the satellites do not change after the initial inter-satellite networking authentication stage, and the inter-satellite networking is disconnected and reconnected. In this embodiment, the fact that the orbital parameters of the satellites have not changed means that the orbital parameters of the first satellite and the second satellite have not changed.
[0115] Specifically, the method includes the steps:
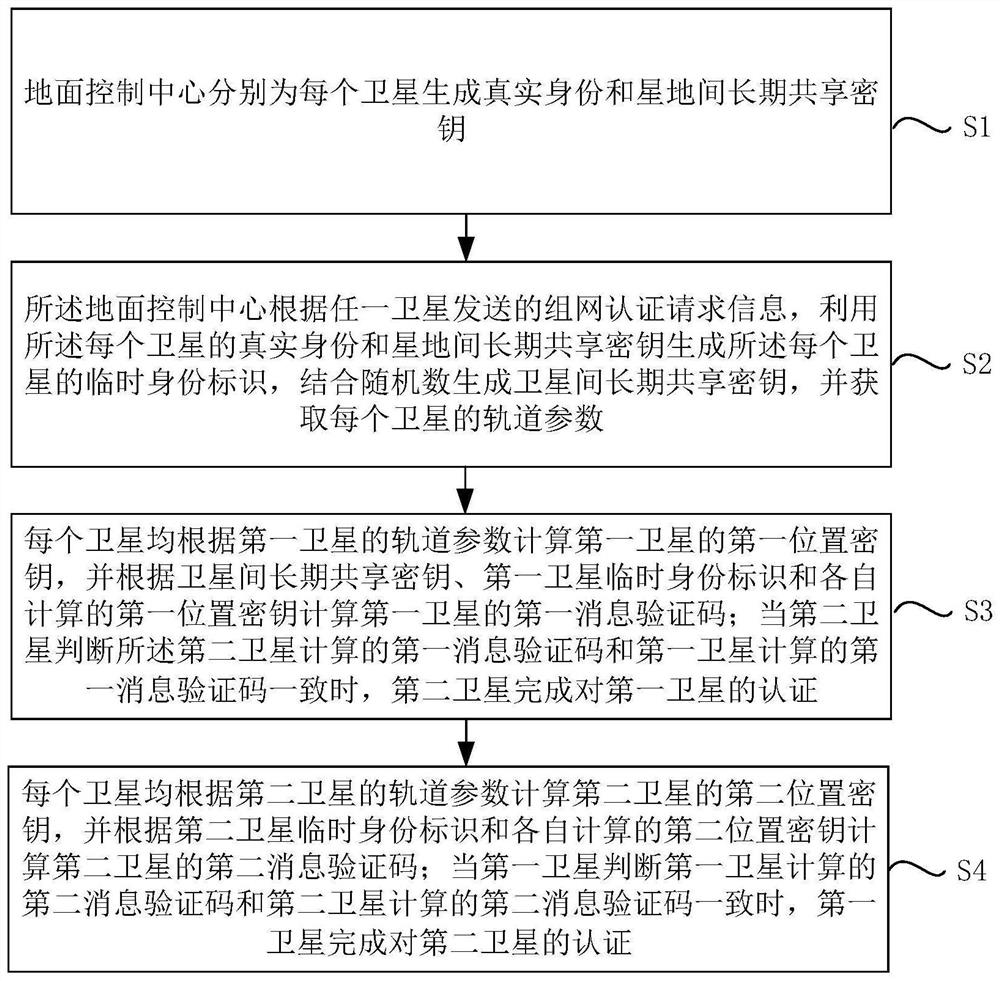
[0116] S1. The ground control center generates a real identity and a long-term shared key between the satellite and the ground for each satellite.
[0117] S2. According to the networking authentication request information sent by any satellite, the ground control center uses the real identity of each satellite and the long-term shared key between satellites to generate the temporary identity of each satellite, and generates t...
Embodiment 3
[0148] On the basis of Embodiment 1 and Embodiment 2, this embodiment provides an inter-satellite networking authentication method in which the orbital parameters of the satellites change after the initial inter-satellite networking authentication stage, and the inter-satellite networking is disconnected and reconnected . In this embodiment, the change in the orbit parameter of the satellite means that the orbit parameter of any one of the first satellite and the second satellite changes.
[0149] Specifically, the method includes the steps:
[0150] S1. The ground control center generates a real identity and a long-term shared key between the satellite and the ground for each satellite.
[0151] S2. According to the networking authentication request information sent by any satellite, the ground control center uses the real identity of each satellite and the long-term shared key between satellites to generate the temporary identity of each satellite, and generates the long-te...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com