Vulnerability type guiding fuzzy testing method and system based on byte sensitive energy distribution
A technology of fuzzing and energy distribution, applied in software testing/debugging, platform integrity maintenance, etc., can solve problems such as customized energy distribution algorithm, and achieve the effect of improving mining efficiency, low computational cost, and low instrumentation cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention will be further described in detail below with reference to the accompanying drawings and embodiments. It should be noted that the following embodiments are intended to facilitate the understanding of the present invention, but do not have any limiting effect on it.
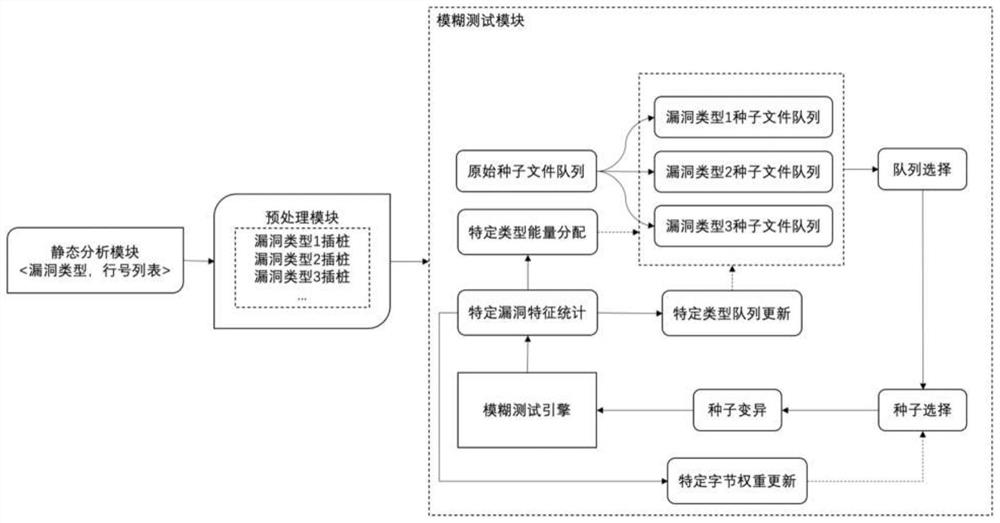
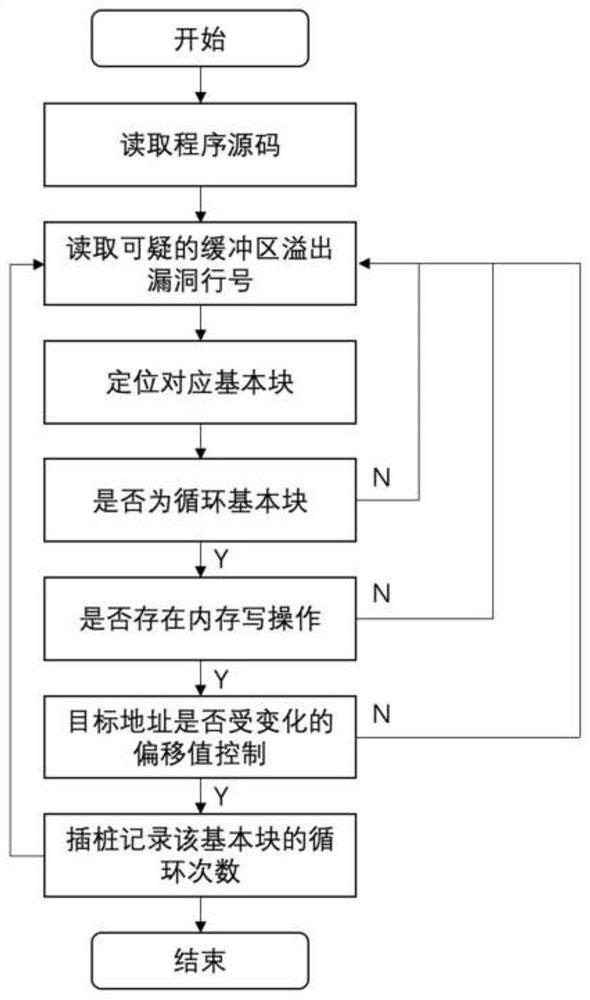
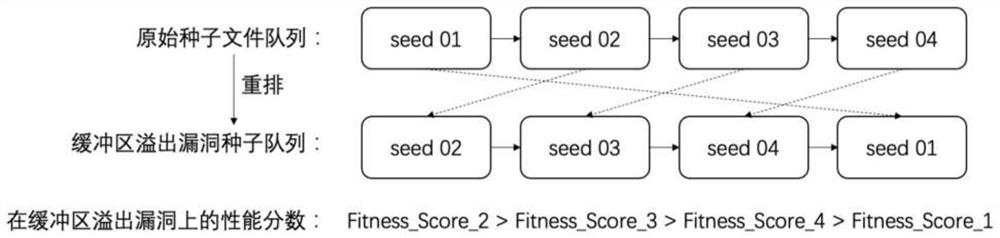
[0052] According to different vulnerability types, the present invention constructs a sample queue dedicated to the vulnerability type, and designs a byte-accurate energy distribution method matching the vulnerability characteristics, thereby realizing faster and more efficient vulnerability exploration on each vulnerability type. with digging. For the sake of brevity, the basic idea of the present invention is described by taking the buffer overflow vulnerability as an example: figure 1 As shown, the static analysis module can select any specified static analysis tool for analyzing buffer overflow vulnerabilities, and the analysis result obtained is a series of line number position...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com