Anti-quantum-attack electronic signature method and anti-quantum-attack electronic signature system
An anti-quantum attack, electronic signature technology, applied in the field of electronic signature methods and systems, can solve problems affecting the amount and efficiency of communication data, insecure cryptography, high security risks, etc., to eliminate security based on computing security. Defects, low computational complexity, the effect of fewer encryption times
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
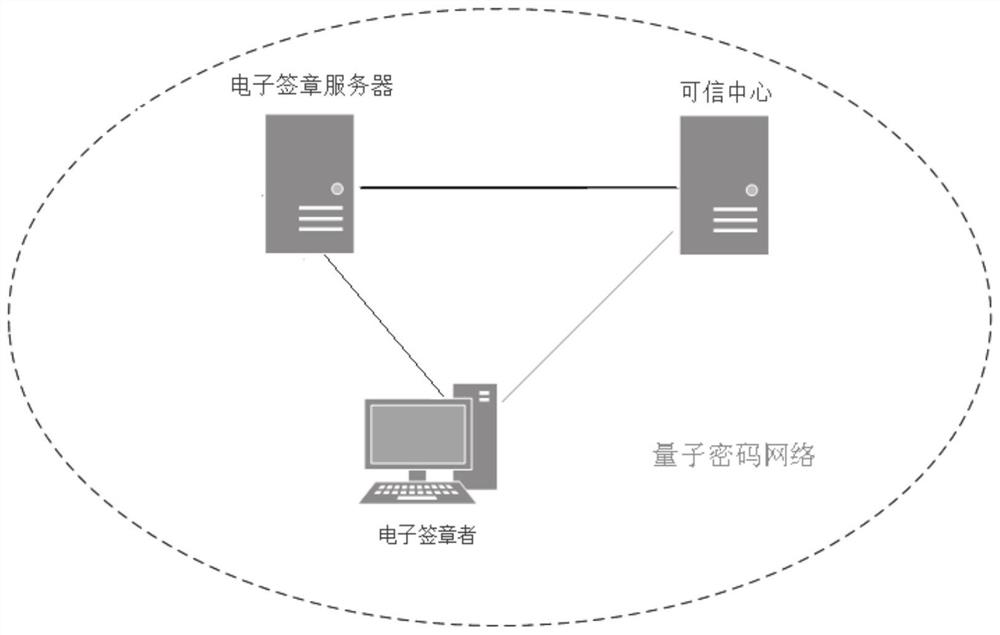
[0042] This embodiment provides an electronic signature system that is resistant to quantum attacks, relying on the abundant symmetric key resources of the quantum cryptography network, specifically as follows figure 1 shown.
[0043] The whole system includes a trusted center, an electronic signature server, and an applicant for signature (terminal equipment). The functions of each component of the system are detailed as follows:
[0044] The trusted center is a trusted third-party organization, located at the terminal of the quantum cryptography network. The trusted center has a true random number signature key store (hereinafter referred to as the signature key store), which is used for digital signature of electronic signature data. Divide the keys of the keystore according to the length used for each digital signature, and sequentially number the divided keys. The trusted center keeps each key used for signing and its number until the validity period of the key's signature...
Embodiment 2
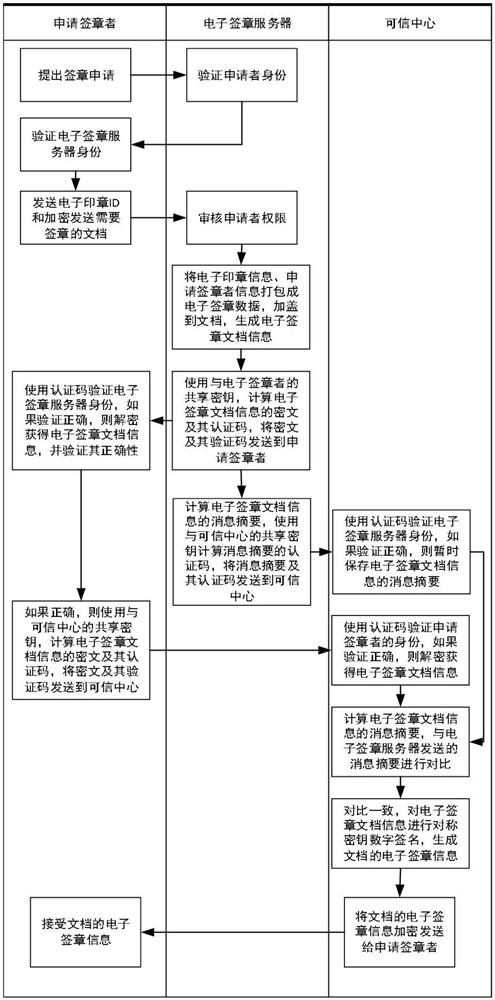
[0054] Based on the system of Embodiment 1, it provides such as figure 2 The signature process shown is detailed below:
[0055] The signature applicant uses the registration ID to initiate a signature application to the electronic signature server, and the electronic signature server and the signature applicant use the shared key for authentication.
[0056] The authentication process is as follows:
[0057] After the electronic signature server receives the signature application request, it sends the random number r1 to the signature applicant;
[0058] The applicant for signature receives r1, and uses the unused shared key K with serial number n to calculate HMAC(r1||SID||n; K), where SID is the ID of the applicant for signature, and || represents the data connection operation;
[0059] The signature applicant selects a random number r2, and sends r2, n and HMAC (r1||SID||n; K) to the electronic signature server;
[0060] The electronic signature server reads the shared...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap