Novel arbitration quantum signature method based on XOR encryption and GHZ state
A new type of quantum technology, applied in the field of quantum communication, can solve the problems of technical realization and application difficulties, and achieve the effect of simple operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
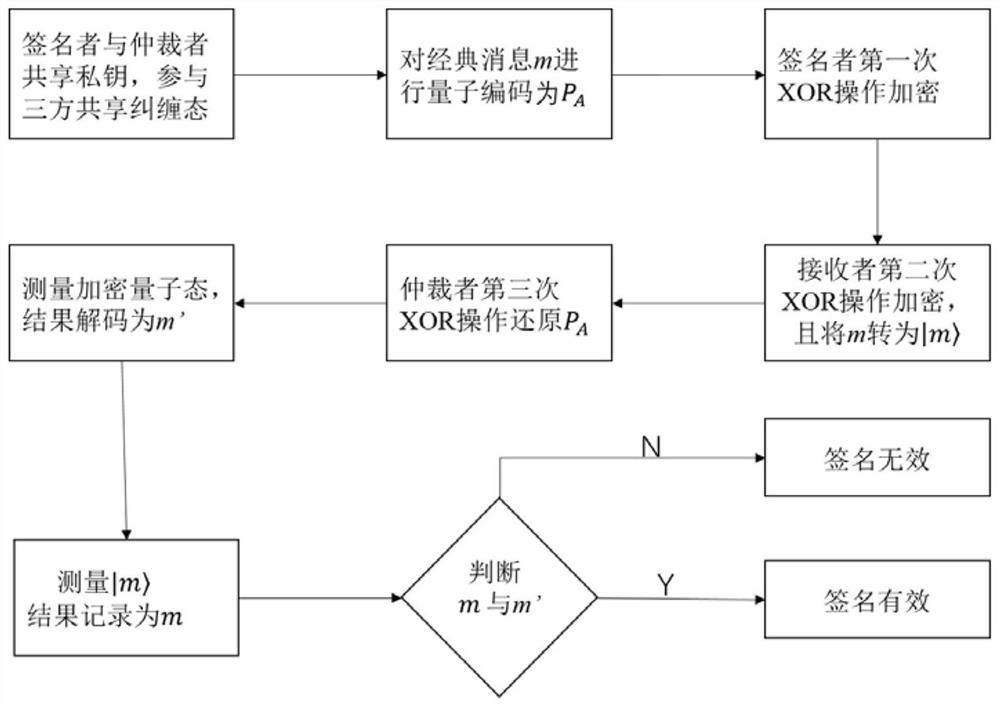
example 1
[0061] Example 1: m={011} is a 3-bit message. Suppose that by using the hash function and the key k A Calculated to get t A1 =G 1 (m||k A ) = {010} and t A2 =G 2 (m||k A )={101}. According to the coding rules shown in Table 1, we can get in
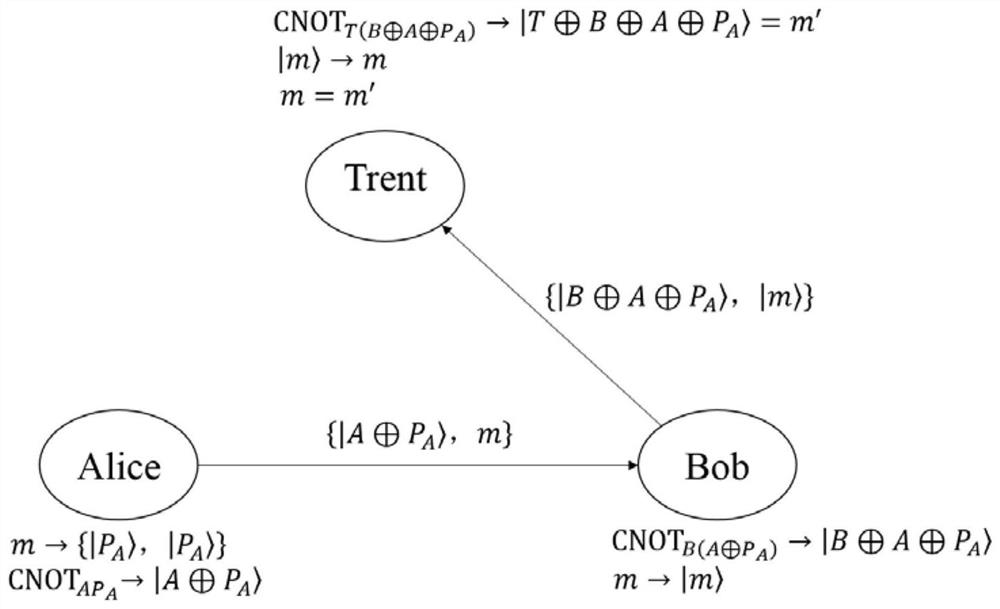
[0062] Step 2Alice uses sequence A as a control bit, sequence P A As a target, the CNOT operation is performed to obtain
[0063]
example 2
[0064] Example 2: Let all data be as described in Example 1. Then according to example 1 and step 2, we can get
[0065]
[0066]
[0067]
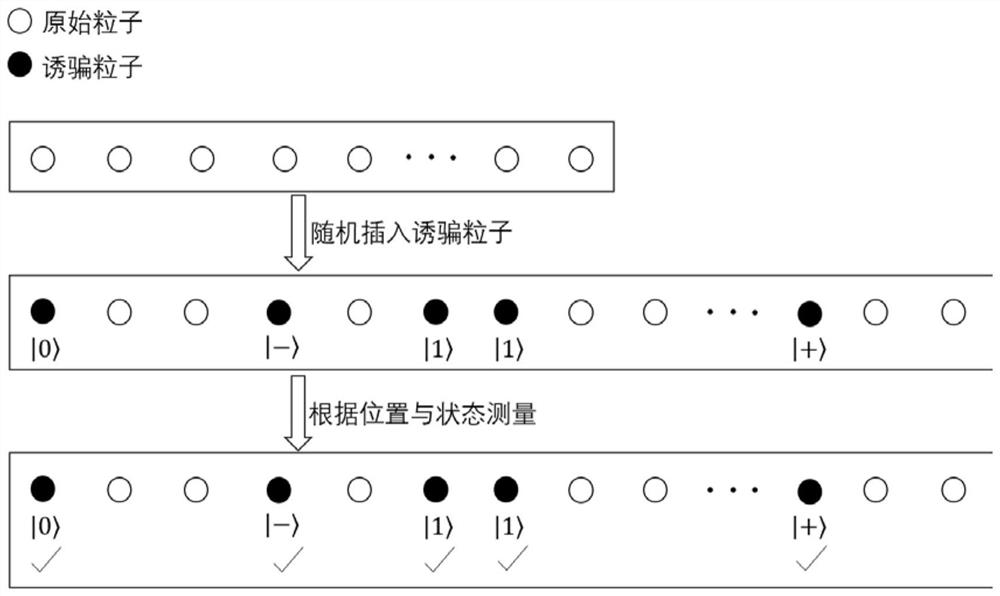
[0068] Step 3 Through eavesdropping detection technology, Alice safely Send to Bob. Alice, on the other hand, sends message m to Bob over the classical channel.
[0069] Step 4 Through wiretap detection technology, Bob securely receives Bob, on the other hand, receives message m over the classical channel. Finally, Bob will as Alice's signature.
[0070] The signature verification steps mainly include four steps:
[0071] Bob checks the signature with the following verification steps Validity of:
[0072]Step 5Bob uses sequence B as the control bit, and the sequence As the target position, the control NOT gate operation CNOT is performed. This operation can be expressed as
example 3
[0073] Example 3: Let all data be as described in Example 2. Then according to example 2 and verification step 5, we can get
[0074]
[0075]
[0076]
[0077] Step 6Bob sends a message to Trent through eavesdropping detection technology where |m>=|m 1 m 2 ...m n >.
[0078] Example 4: Let all data be as described in Example 1. It can be known from example 1 that |m>=|011>.
[0079] Step 7 Through eavesdropping detection technology, Trent is safely obtained Trent then uses the sequence T as a control bit, while the sequence As the target position, the control NOT gate CNOT operation is performed. The operation can be expressed as:
[0080]
[0081] Example 5: Let all data be as described in Examples 3 and 4. Then according to the verification step 7, we can get
[0082]
[0083]
[0084]
[0085] easy to prove Here, for simplicity, use express Bob, on the other hand, can easily derive m from |m> by measuring each |m with an orthonormal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com