USB Key safety control method and device
A technology of security control and duration, applied in the field of identity authentication, can solve the problems of not fully guaranteeing the security of user funds, too long content, unable to display the transfer object and transfer amount, etc., so as to reduce the risk of fraud and improve the effect of security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The embodiments of the present application will be described in detail below with reference to the accompanying drawings and examples, so as to fully understand and implement the implementation process of how to apply technical means to solve technical problems and achieve technical effects in the present application. It should be noted that, as long as there is no conflict, the various embodiments in this application and various features in each embodiment can be combined with each other, and the formed technical solutions are all within the protection scope of this application.
[0028] Additionally, the steps shown in the flowcharts of the figures may be performed in a computer system, such as a set of computer-executable instructions, and, although shown in a logical order in the flowcharts, in some cases, may be executed differently The steps shown or described are performed in the order shown herein.
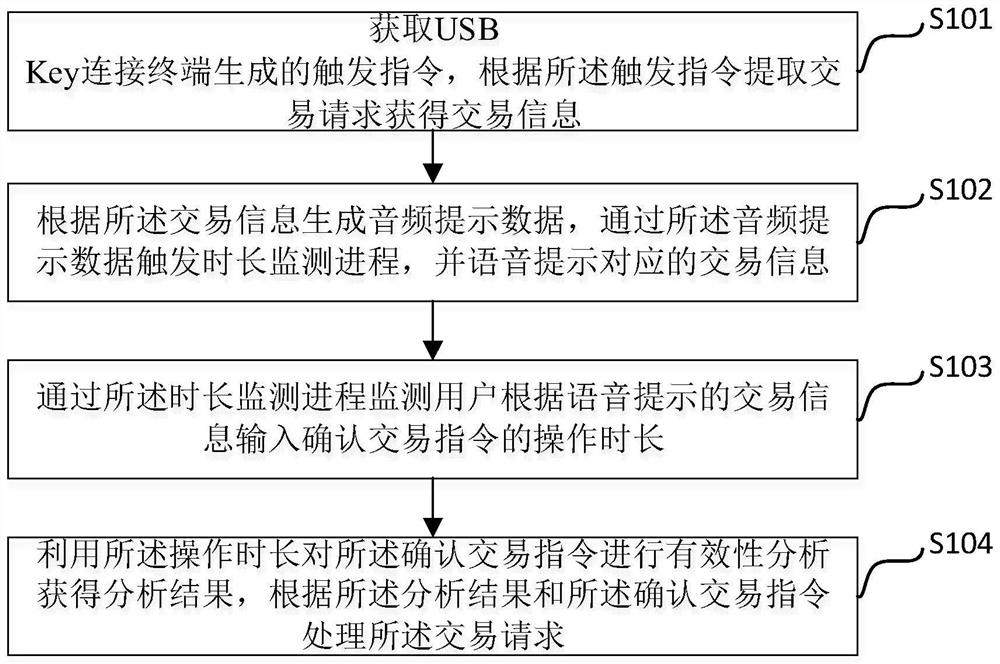
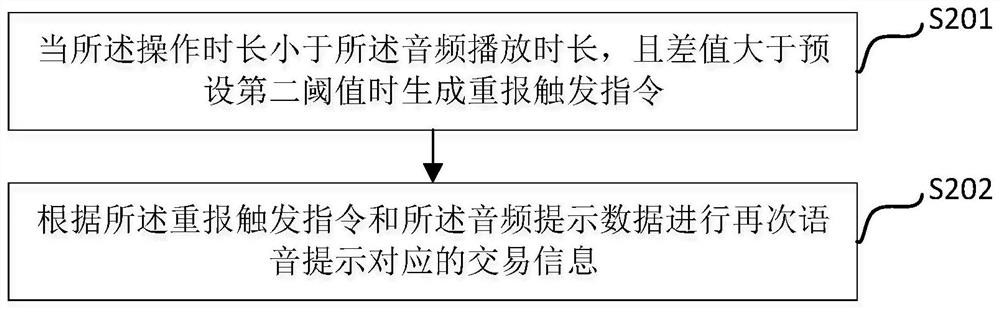
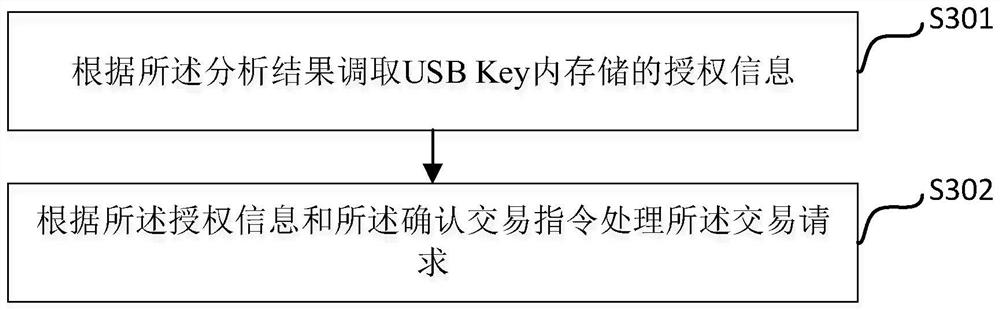
[0029] Please refer to figure 1 As shown, a USB Key security ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com