Resource request monitoring method and device, computer equipment and storage medium
A resource request and computer program technology, applied in the field of data processing, can solve problems such as life safety monitoring and consumer behavior difficult to monitor, and achieve the effect of reducing the risk of fraud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
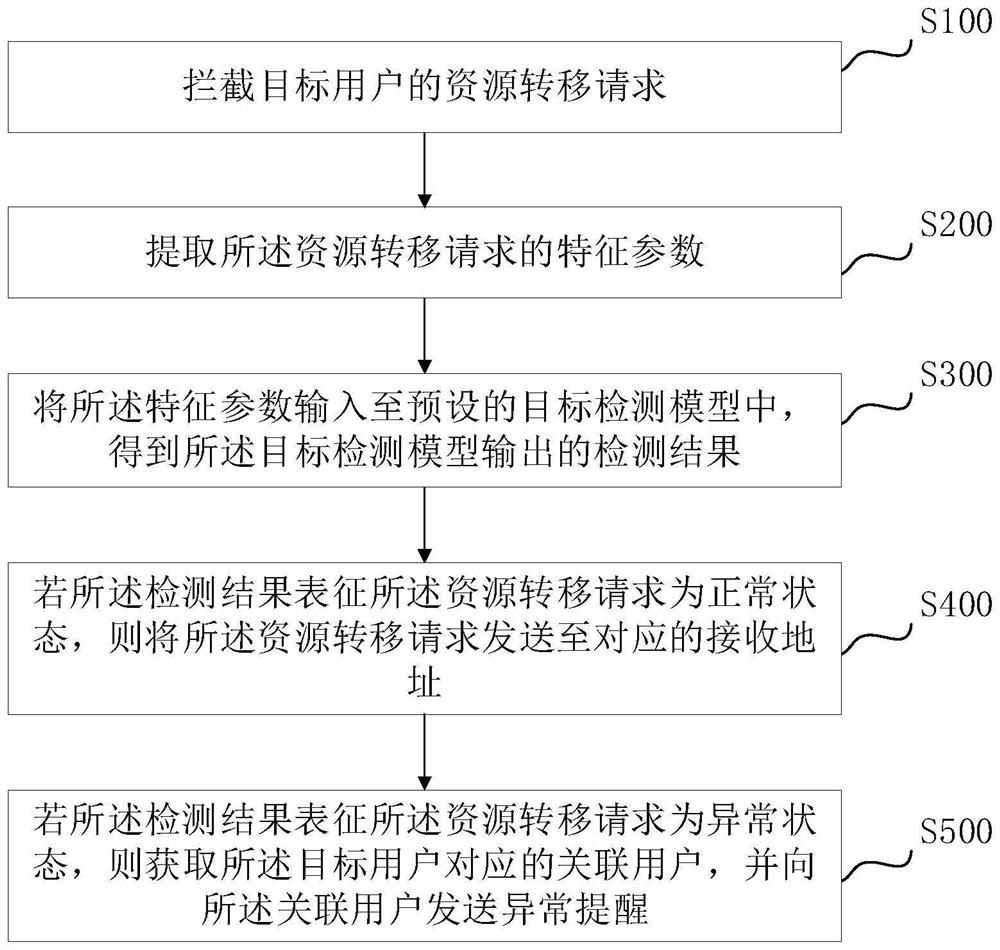
[0056] like figure 1 As shown, it is a schematic flow chart of a method for monitoring resource requests in the first embodiment. It can be seen from the figure that it includes steps S100-500, and the details are as follows:
[0057] S100: Intercept the resource transfer request of the target user.
[0058] In an exemplary embodiment, the target user is used to represent a group of people who are customized according to the monitoring requirements. For example, adults can set parents or minor children as target users, and the resource transfer request is used to represent a request for resource changes. Such as payment, transfer, etc. After the target user is set, when the target user initiates a resource transfer request, the resource transfer request is intercepted, and the resource transfer request is identified to prevent the target user from generating fraudulent transactions. Preferably, in this embodiment, a monitoring platform can be optionally established to monito...
Embodiment 2
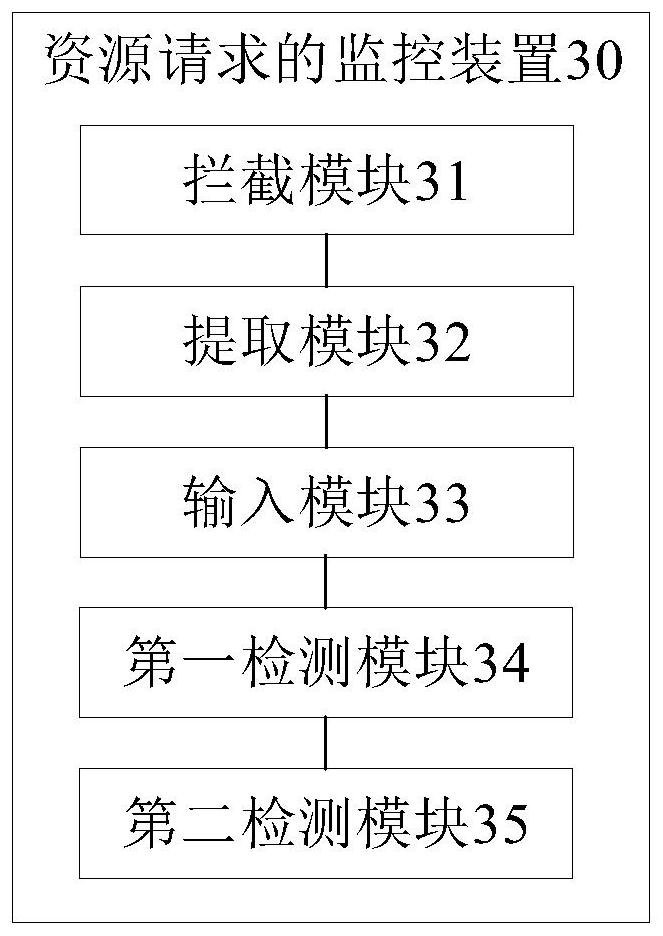
[0084] like image 3As shown, it is a functional block diagram of the apparatus for monitoring resource requests according to the second embodiment.
[0085] The resource request monitoring device 3 includes an interception module 31 , an extraction module 32 , an input module 33 , a first detection module 34 and a second detection module 35 . A module referred to in the present invention refers to a series of computer program segments that can be executed by a processor and can perform fixed functions, and are stored in a memory. In this embodiment, the functions of each module will be described in detail in subsequent embodiments.
[0086] The interception module 31 is used to intercept the resource transfer request of the target user.
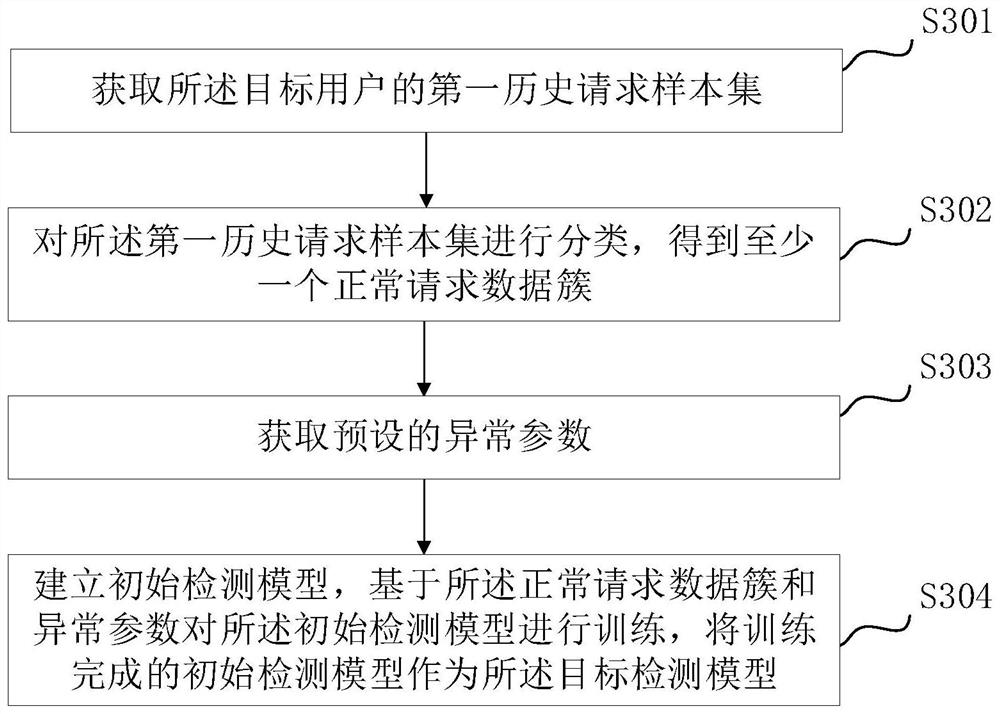
[0087] In an exemplary embodiment, before intercepting the resource transfer request of the target user, obtain the historical target request of the target user; extract the generation time of the historical target request; obtain a preset...
Embodiment 3
[0096] like Figure 4 As shown, it is a schematic structural diagram of a computer device according to the third embodiment of the method for monitoring a resource request.
[0097] In an exemplary embodiment, the computer device 4 includes, but is not limited to, a memory 41, a processor 42, and a computer program stored in the memory 41 and executable on the processor, such as monitoring of resource requests program. Those skilled in the art can understand that the schematic diagram is only an example of a computer device, and does not constitute a limitation to the computer device, and may include more or less components than the one shown, or combine some components, or For example, the computer device may also include input and output devices, network access devices, buses, and the like.
[0098] The memory 41 includes at least one type of computer-readable storage medium, and the readable storage medium includes flash memory, hard disk, multimedia card, card-type memor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com