Convolutional neural network-based side channel attack method and system
A convolutional neural network and side-channel attack technology, applied to biological neural network models, transmission systems, neural architectures, etc., can solve the problems of difficult template matching and low universality, and achieve increased attack efficiency and high universality , the effect of improving the attack success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
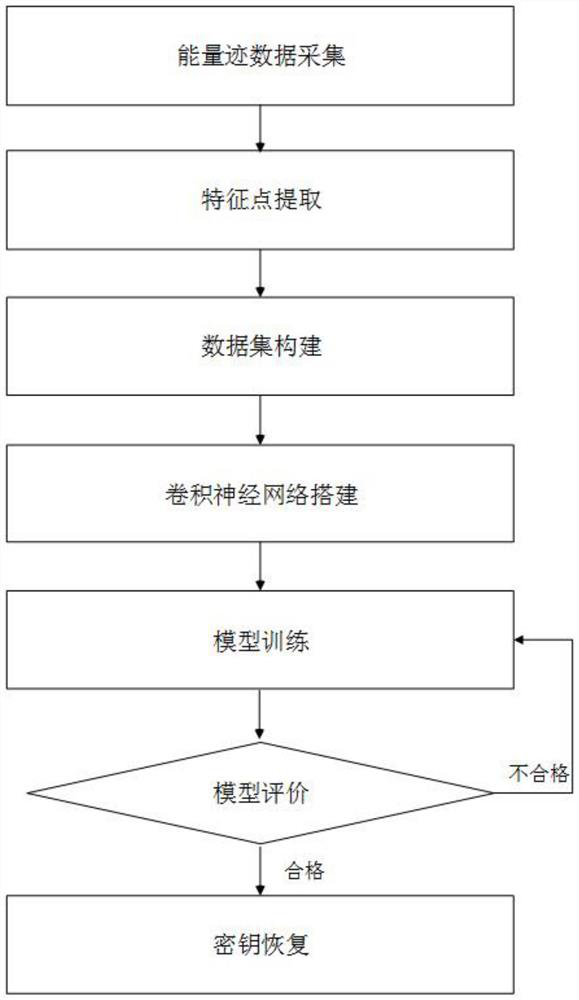
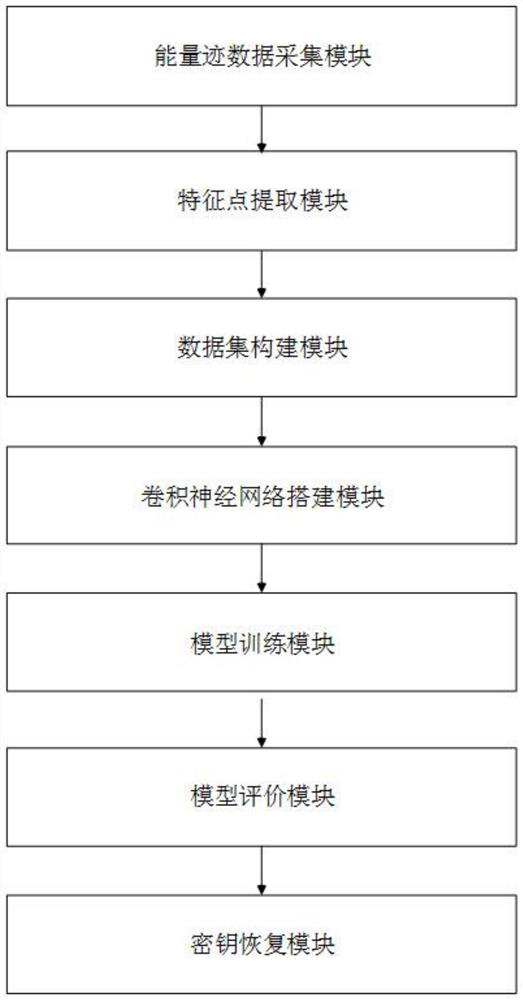
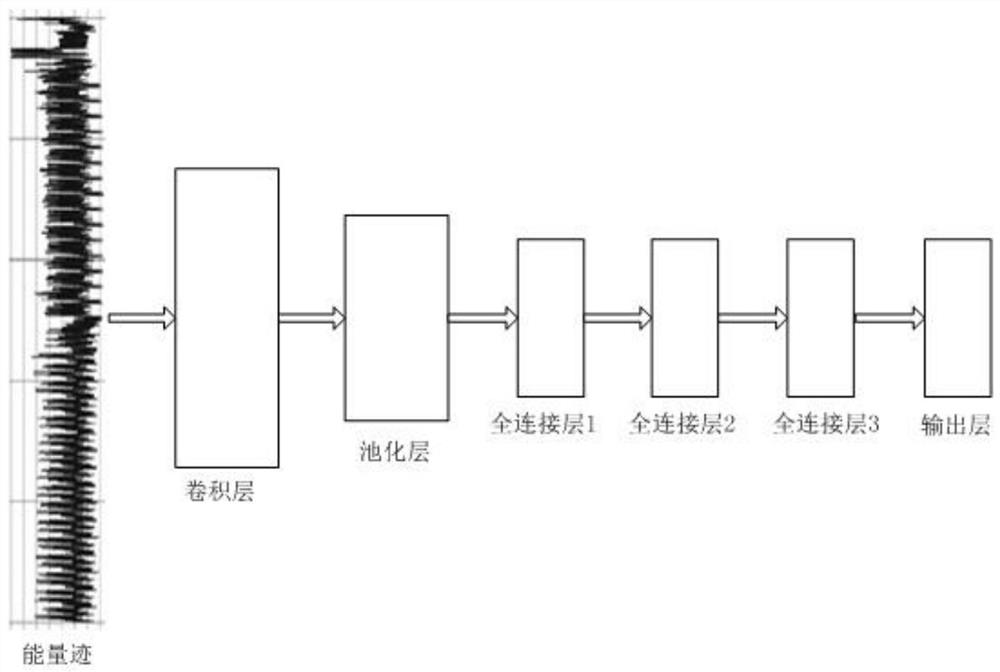
[0040] Such as Figure 1 to Figure 4 As shown, the purpose of the present invention is to overcome the inaccurate template construction in the prior art, and to propose a convolutional neural network-based lateral Channel attack method, the convolutional neural network in this method can be adapted according to different energy models to improve the attack success rate.
[0041] In order to achieve the purpose of the above invention, the present invention is based on the side channel attack method of deep learning convolutional neural network, comprising the following steps:
[0042] (1) Energy trace data acquisition;
[0043] The cryptographic algorithm is run on the cryptographic device, the key is unchanged, the plaintext is random, and energy traces are collected at the same time. T sample points are collected for each energy trace, and a total of N energy traces are collected.
[0044] (2) feature point extraction;
[0045] Use normalized inter-class variance (Normaliz...
Embodiment 2
[0065] In this embodiment, the following steps are included:
[0066] Step S1: Acquisition of energy trace data;
[0067] Download the cryptographic algorithm firmware (such as AES) to the cryptographic device. The upper computer sends the fixed key and random plaintext to the encryption device, and the encryption device starts to run the encryption algorithm after receiving the key and plaintext, and returns the ciphertext to the upper computer after one encryption is completed. At the same time, the oscilloscope collects the energy signal generated when the encryption device is encrypted, and transmits the energy signal back to the host computer through the network cable. The host computer packs the received ciphertext, energy signal and previously issued plaintext into an energy trace file. Repeatedly collect 100,000 sets of energy traces, and sample 1200 sample points for each energy trace.
[0068] Step S2: feature point extraction;
[0069] Use Normalized Inter-Class...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com