Key point differential privacy-driven face image privacy protection method
A face image and differential privacy technology, which is applied in the field of face image privacy protection driven by key point differential privacy, can solve the problems of infringing on the privacy of others, the image is not realistic enough, and the original face image is changed, so as to achieve the high quality of the generated image, Efficient and beautiful privacy protection, good data availability and visual effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] The present invention will be further described below in conjunction with drawings and embodiments.
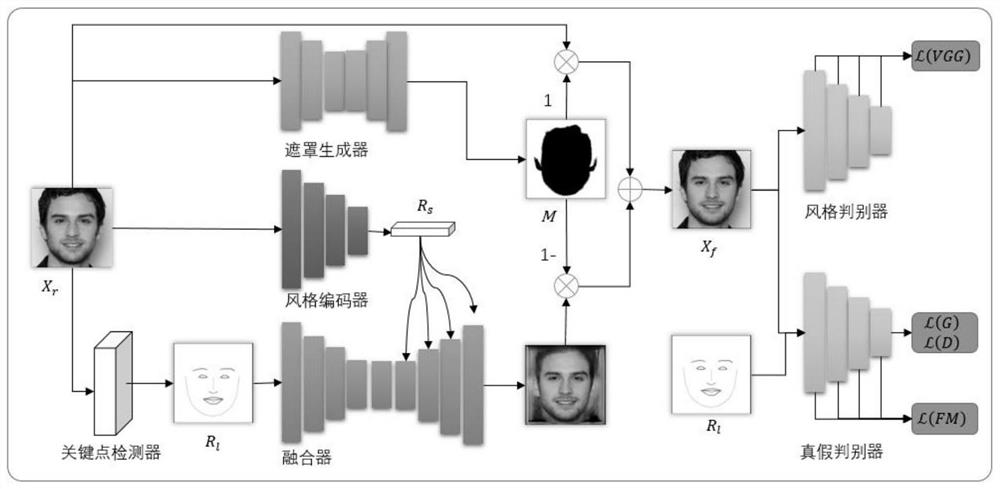
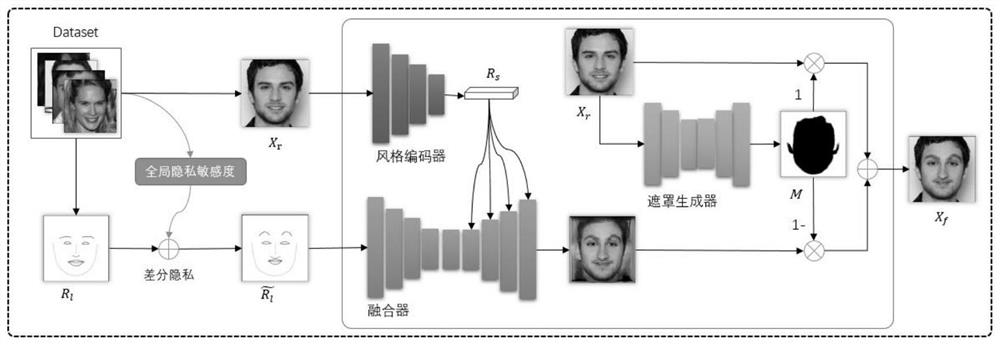
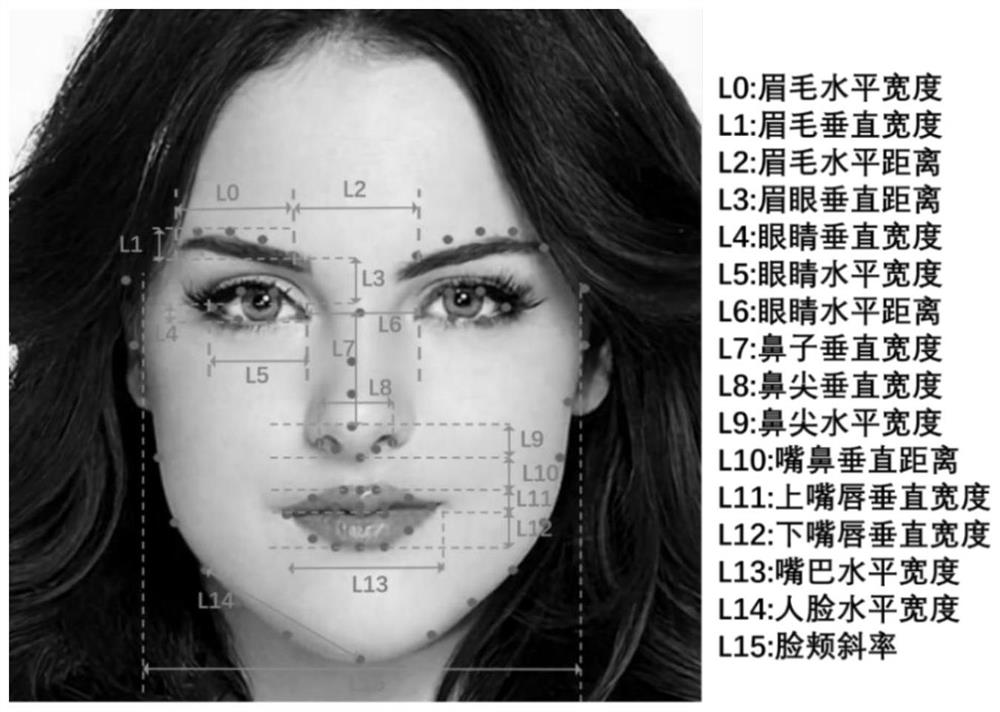
[0072] Face key point identification privacy protection technology based on generative confrontation network. For the specific overall architecture flow chart, please refer to figure 1 As shown in the anonymization flow chart, please refer to figure 2 Shown, define the key point identification of the face refer to image 3 Shown:
[0073] The technical solution adopted by the present invention to solve its technical problems comprises the following steps:
[0074] Step 1: Data preprocessing;
[0075] 1-1. Data preparation.
[0076] Select the face data sets CelebA-HQ and VGGFACE2, and use the face key point detector (such as facealignment, dlib) to detect the face data set images to obtain the face key points.
[0077] 1-2. Construct key point identification anonymous space.
[0078] Analyze the key points to get 16 identity-related components that may contain id...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com