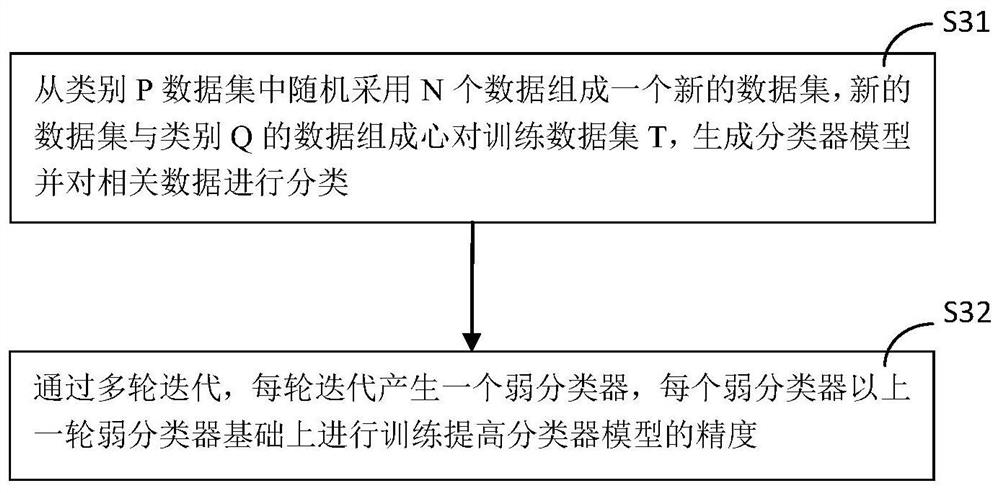
SQL injection attack identification method based on machine learning
A technology of injection attack and machine learning, which is applied in character and pattern recognition, instruments, computer parts, etc., can solve problems such as inability to prevent SQL injection attacks in a timely and effective manner, and achieve flexible and diverse identification methods, reduce dependence, and reduce complexity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
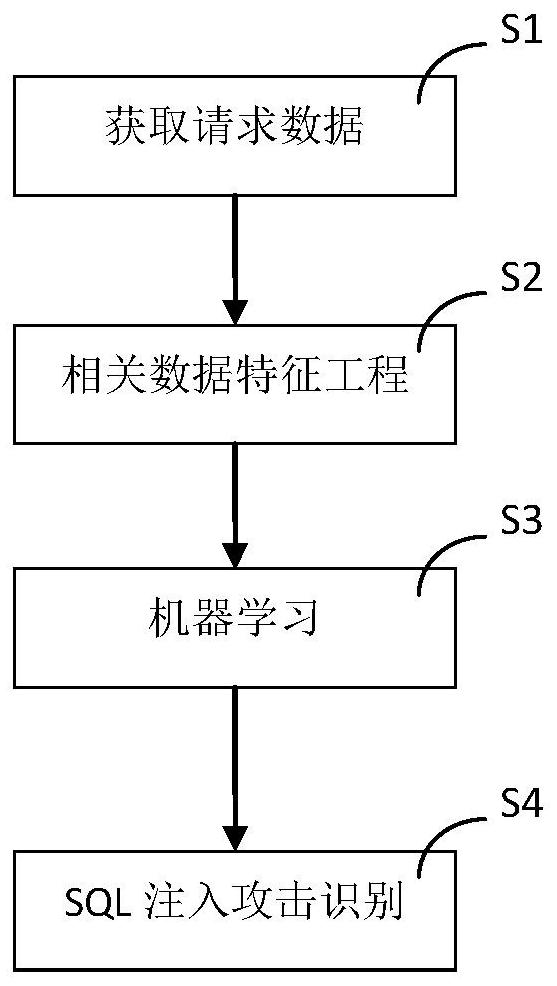
[0043] like figure 1 As shown, a method for identifying SQL injection attacks based on machine learning includes the following steps:
[0044] S1. Obtain request data: build a shooting range with SQL injection target holes, use SQLMAP and manual penetration to collect relevant data containing SQL injection, and classify and label relevant data; relevant data include request parameters, request methods, response content, responses Status; classification and labeling include SQL injection attacks and non-SQL injection attacks;
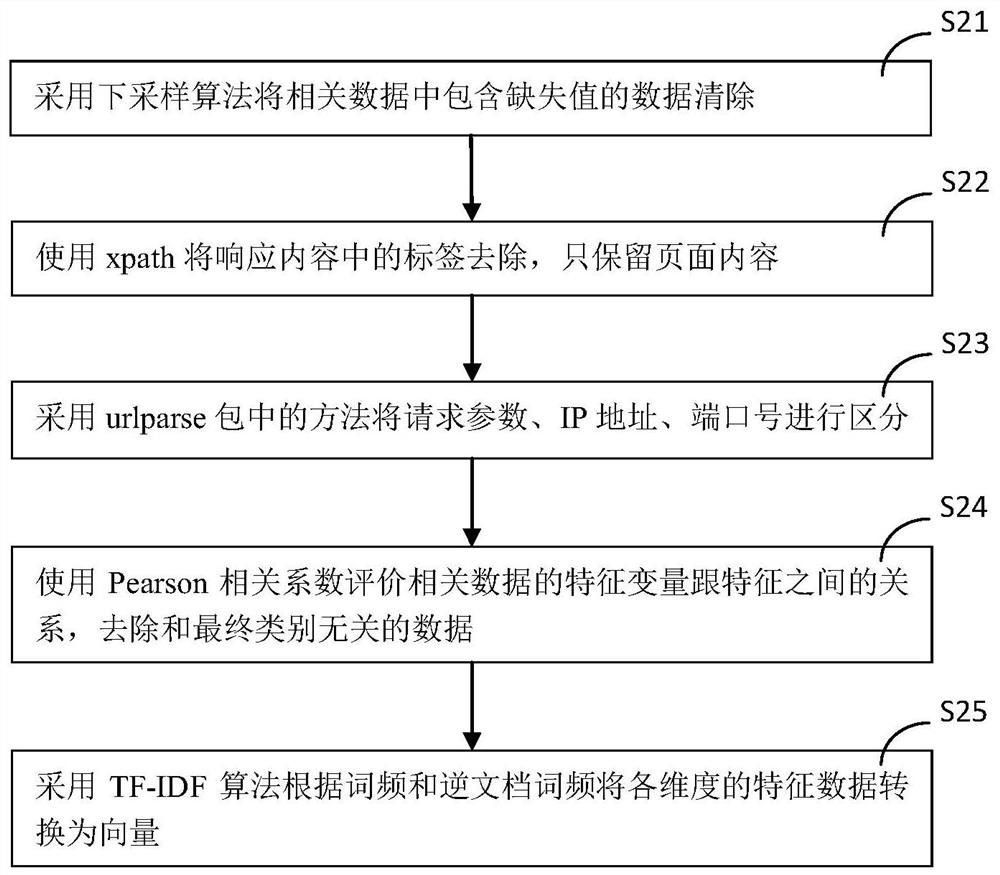
[0045] S2. Relevant data feature engineering: perform data cleaning on relevant data, extract feature data and convert it into a vector; for example figure 2 shown, including the following steps:
[0046] S21. Use a downsampling algorithm to clear data containing missing values in the relevant data;
[0047] S22. Use xpath to remove the tags in the response content, and only keep the page content;
[0048] S23, using the method in the urlparse pac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com