Network security information sharing system and method based on expert joint evaluation, electronic equipment and storage medium
A technology of network security and information sharing, applied in the network security information sharing system, the network security information sharing system field based on the joint evaluation of experts, can solve the problems of low accuracy of risk research and judgment and the gap of members' analysis ability, so as to enhance the members' analysis ability. , the effect of improving the accuracy of risk research and judgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
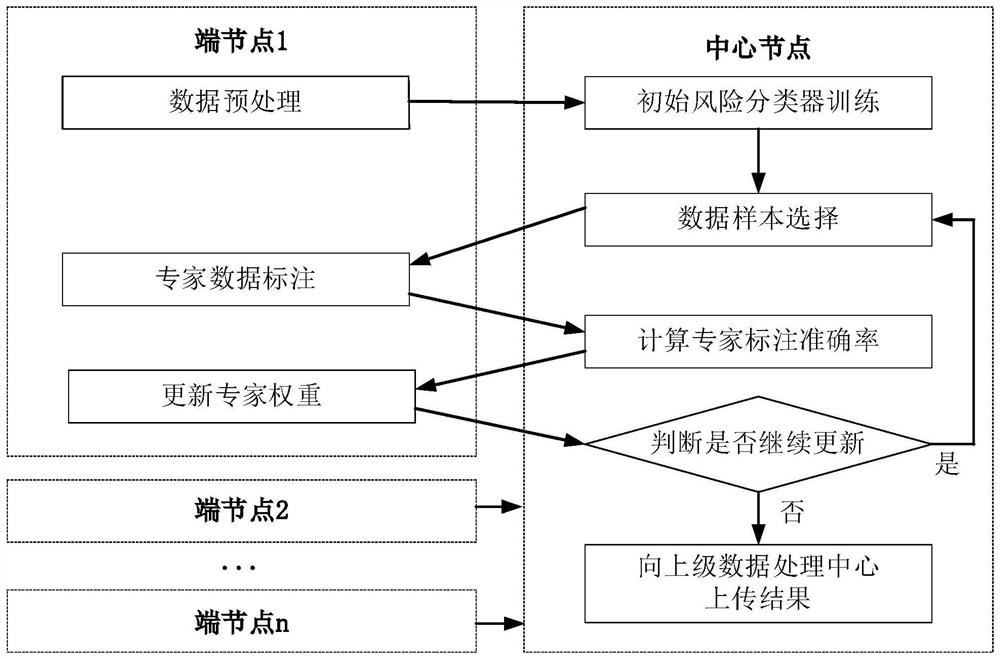
[0063] figure 1 A block diagram of a network security information sharing system based on expert joint evaluation according to Embodiment 1 of the present application is shown.
[0064] A network security information sharing system based on expert joint evaluation, including: n end nodes and a central node; each end node includes a data preprocessing module, an expert data labeling module, and an expert weight update module; the central node includes an initial risk classifier A training module, an expert labeling accuracy calculation module, an update judgment module, and a data upload module; the data preprocessing module is used for data cleaning and processing, and initially marks the risk categories of network security information content; the initial risk classifier The training module is used to receive network security data from each end node, summarize and organize them, select a small number of samples with risk label information for training, obtain an initial risk ...
Embodiment 2
[0066] Embodiment 2 of the present application provides a network security information sharing method based on expert joint evaluation (see figure 2 ), in order to better illustrate the purpose and advantages of this embodiment, further details will be given below. The application carries out the simulation experiment in the computer according to the following steps:
[0067] S1: Each endpoint preprocesses the network security information to be uploaded.
[0068] This application conducts simulation experiments on database transaction security risk assessment data from a scientific research institution. Among them, there are more than 170 pieces of initial training data and more than 2300 pieces of test data. The input feature of each piece of data is the specific factors that affect the risk assessment, a total of 12; the output result is the risk assessment level, which is divided into two levels of low risk and high risk. The training data labels are evaluated by securi...
Embodiment 3
[0098] Embodiment 3 of the present application provides an electronic device, see image 3 , an electronic device in the form of a general-purpose computing device. Components of an electronic device may include, but are not limited to: one or more processors or processing units, memory for storing computer programs that can run on the processors, connections to different system components (including memory, one or more processors or processing unit) bus.
[0099] Wherein, when the one or more processors or processing units are used to run the computer program, execute the steps of the method described in the second embodiment. The types of processors used include central processing units, general purpose processors, digital signal processors, application specific integrated circuits, field programmable gate arrays or other programmable logic devices, transistor logic devices, hardware components or any combination thereof.
[0100] Wherein, the bus refers to one or more of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com