Block chain verification method for realizing tamper-proofing of block chain, storage medium and device
A verification method and blockchain technology, which are applied to storage media and devices to realize blockchain verification methods for tamper-proofing of blockchains, can solve problems such as unfavorable research and development efficiency and system stability, low verification efficiency, and regional problems. Block and transaction verification performance loss is huge and other problems, to achieve the effect of facilitating verification efficiency, reducing redundant steps, and improving verification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
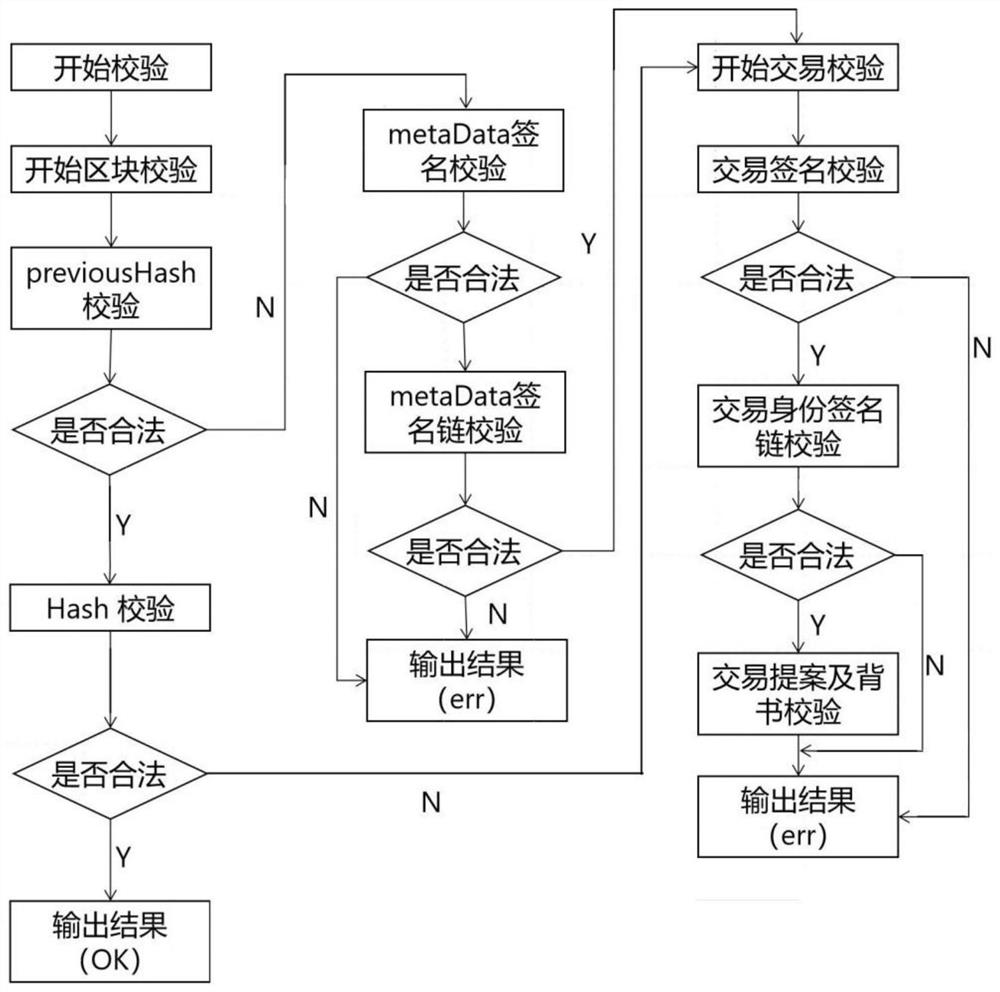
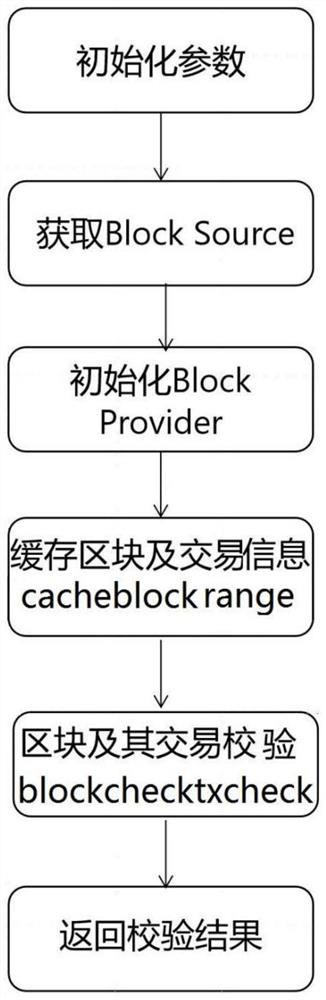
[0035] The technology of the present invention will be described in detail below with reference to the accompanying drawings and specific embodiments. Such as figure 1 As shown, the present invention proposes a block chain verification method that realizes block chain tamper-proof, and the specific implementation steps include:
[0036] Step1: Configure different national secret algorithm verification directory configurations through the national secret adapter and its components to read the specified block ledger file, perform preliminary verification on the ledger file, and obtain the corresponding blockchain information. The blockchain information Including block information, transaction information and signature information on the chain, the signature information includes the signature of the block file and the certificate issuance chain associated with the block file;
[0037] Wherein, the verification method also supports the National Secret Algorithm, which is a series...
Embodiment 2
[0057] The block verification includes:
[0058] 1) previousHash check, verify that the previousHash of the current block is equal to the hash value calculated from the previous block;
[0059] 2) Hash verification, verify that the hash of the current block is equal to the hash value calculated by the current block;
[0060] 3) Check the latest configuration block, verify that the blockNumber value of the latest configuration block of the current block is less than or equal to the blockNumber value of the current block;
[0061] 4) metaData (metadata) verification, verify each signature of metaData[0] under the current block, and verify its certificate signature chain;
[0062] The transaction verification includes:
[0063] 1) Transaction certificate signature chain verification, verifying the certificate signature chain of each transaction;
[0064] 2) Transaction signature chain, verifying the signature of each transaction;
[0065] 3) Transaction proposal and multiplie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com