Unified authentication and authorization method based on OAuth2 protocol
An authentication authorization and protocol technology, applied in the computer field, can solve the problems of low security of access system resources, reduced authentication accuracy, and difficulty for system users to use third-party applications, so as to improve system service capabilities, access security, and ensure security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
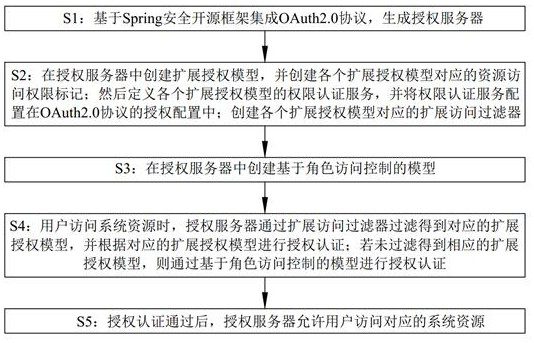
[0030] This embodiment discloses a unified authentication and authorization method based on the OAuth2 protocol.
[0031] Such as figure 1 As shown, the unified authentication and authorization method based on the OAuth2 protocol includes the following steps:
[0032] S1: Integrate the OAuth2.0 protocol based on the Spring security open source framework to generate an authorization server; specifically, the generated authorization server supports the existing authorization code mode, password mode and client mode.
[0033] S2: Create an extended authorization model in the authorization server, and create resource access rights tags corresponding to each extended authorization model; then define the authorization authentication service of each extended authorization model, and configure the authorization authentication service in the authorization configuration of the OAuth2.0 protocol ; Finally, create an extended access filter corresponding to each extended authorization mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com