Multi-node authentication method for trusted execution environment
An authentication method and execution environment technology, which is applied in secure communication devices, user identity/authority verification, digital transmission systems, etc., can solve problems such as low algorithm efficiency and inability to provide high-performance and practical solutions, and achieve high execution efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
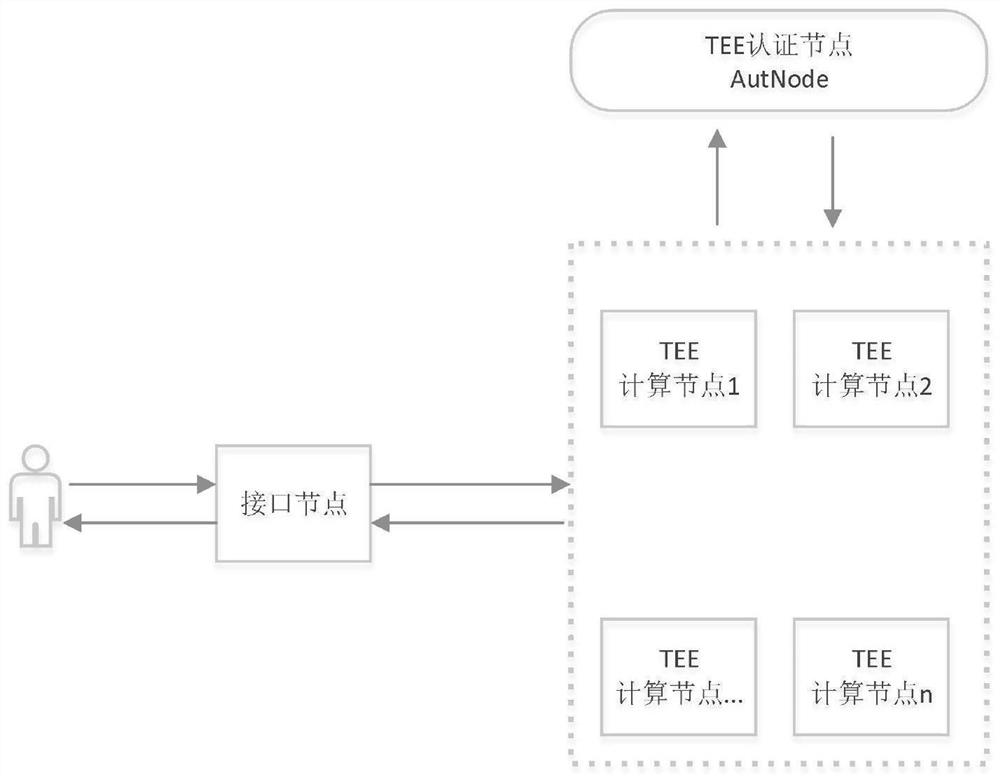
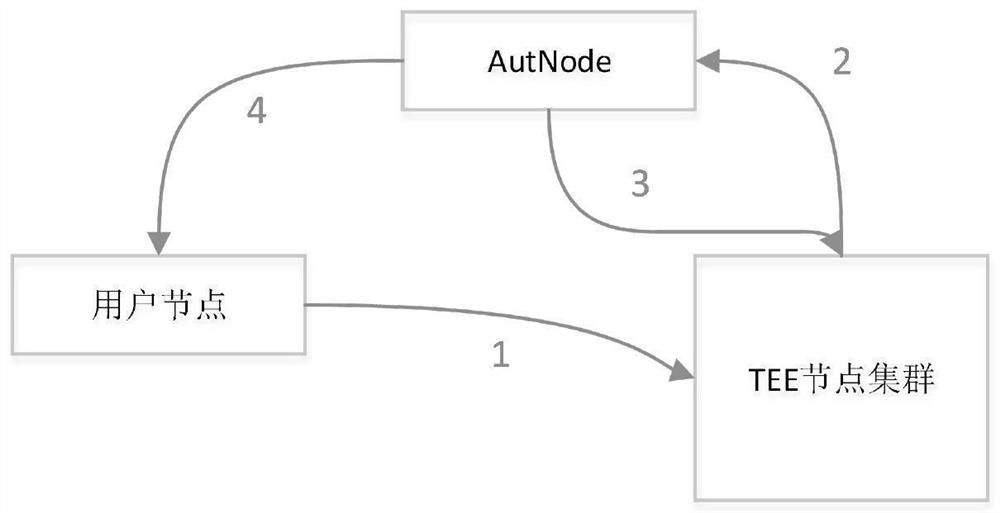
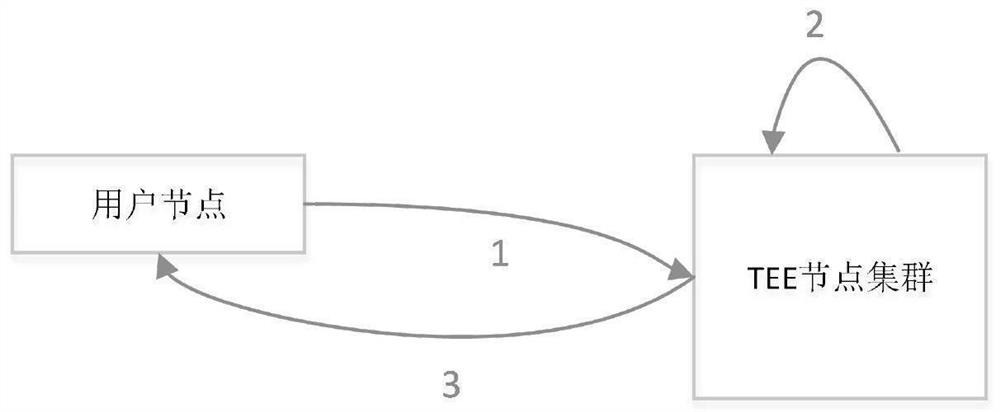
[0032] The present invention as Figure 1-3 As shown, the present invention provides a trusted execution environment multi-node authentication method, assuming that multiple TEE computing nodes form a computing resource pool, and the computing resource management system uniformly allocates computing resources; the resource pool sets a unified access and authentication node (AuthNode), this node assists users to complete the remote authentication process for all allocated TEE computing nodes. The scheme includes two links: user program security deployment and user data security calculation; the main process is described as follows:
[0033] (1). User program security deployment
[0034] The user uploads the computing program to the TEE cloud computing environment and applies for the required computing resources. The computing resource pool allocates TEE computing resources for the user and deploys the user program in the secure computing environment TEE; AutNode starts the remo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com