Information supervision detection method based on software function, performance and data security
A technology of data security and software function, applied in the direction of electrical digital data processing, neural learning method, computer security device, etc. Small possibility of data leakage, easy and fast processing, and the effect of improving the efficiency of information supervision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
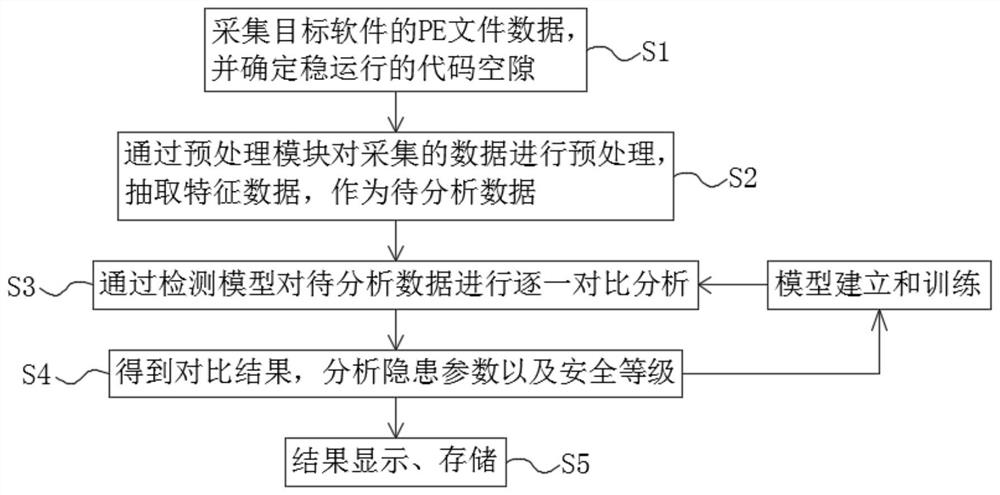
[0031] Example: such as Figure 1 to Figure 2 As shown, the present invention provides a method for information supervision and detection based on software functions, performance, and data security, comprising the following steps:
[0032] S1. Obtain the PE file of the target software, locate the code gaps of the unoperated software codes and unused bytes or byte segments in the PE file, and extract the code gaps;
[0033] S2. Classify and process the collected data through the preprocessing module, and extract characteristic data, and further use it as data to be detected;
[0034] S3. Input the data to be detected into the pre-trained detection model for comparative analysis one by one;
[0035] S4. Determine the security level of information data according to the comparative analysis results, classify and grade the parameters with hidden safety hazards, and feed back the software feature data and results with hidden dangers to the detection model for training and improveme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com