Private network security risk processing method and device, equipment and storage medium
A security risk and processing method technology, applied in the field of private network security risk processing methods, devices, equipment, and storage media, can solve problems such as inability to process security risk situations and risk equipment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
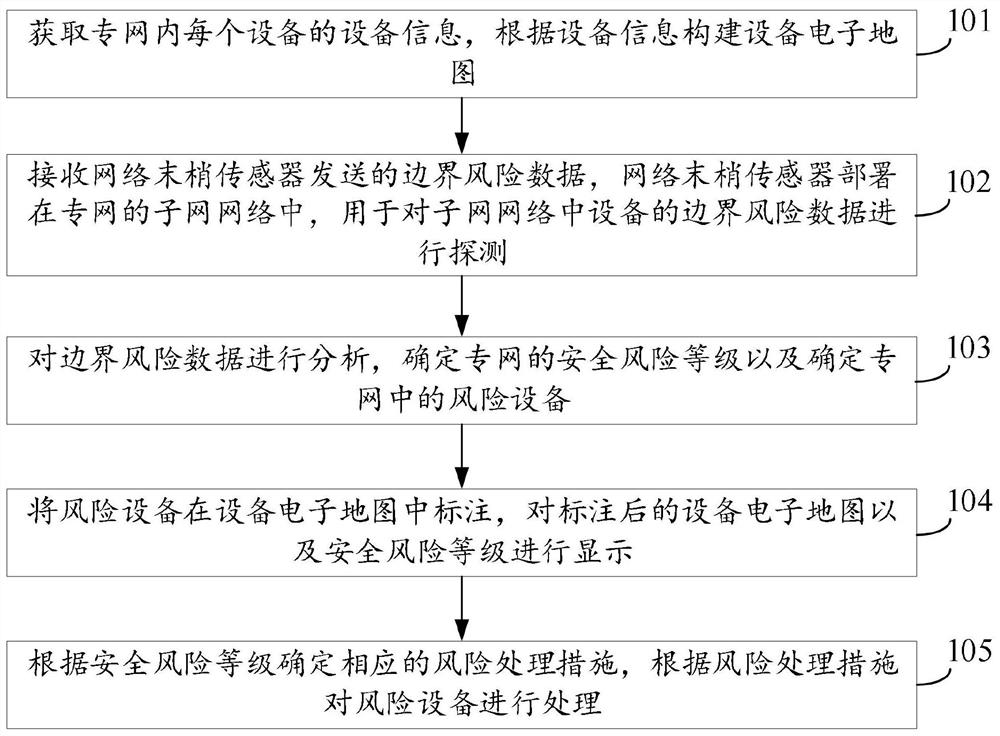
[0056] Such as figure 1 as shown, figure 1 It is a flowchart of a private network security risk processing method provided by an embodiment of the present invention. The private network security risk processing method provided by the embodiment of the present invention can be executed by a private network security risk processing device, which can be implemented by software and / or hardware, and the private network security risk processing device can be two One or more physical entities can also be composed of one physical entity. For example, private network security risk processing equipment can be computers, host computers, servers, tablets and other equipment. The method includes the following steps:
[0057] Step 101. Obtain the device information of each device in the private network, and construct an electronic map of the device according to the device information.
[0058] In this embodiment, it is first necessary to obtain the device information of each device in t...
Embodiment 2
[0069] figure 2 A flow chart of another private network security risk processing method provided by the embodiment of the present invention, as shown in figure 2 shown, including the following steps:
[0070] Step 201 , formulating a list of risk treatment measures, which includes safety risk levels and risk treatment measures corresponding to the safety risk levels.
[0071] In this embodiment, it is first necessary to formulate a list of risk treatment measures. In the process of formulating the list of risk treatment measures, it is necessary to determine the security risk level of the private network, and formulate corresponding risk treatment measures for each security risk level.
[0072] In one embodiment, the security risk level includes a first security risk level, a second security risk level and a third security risk level.
[0073] In this embodiment, in the process of formulating the list of risk treatment measures, three security risk levels are set, which ar...
Embodiment 3
[0094] Such as Figure 4 as shown, Figure 4 A schematic structural diagram of a private network security risk processing device provided in an embodiment of the present invention, including:
[0095] The electronic map construction module 301 is used to obtain the device information of each device in the private network, and construct the device electronic map according to the device information.
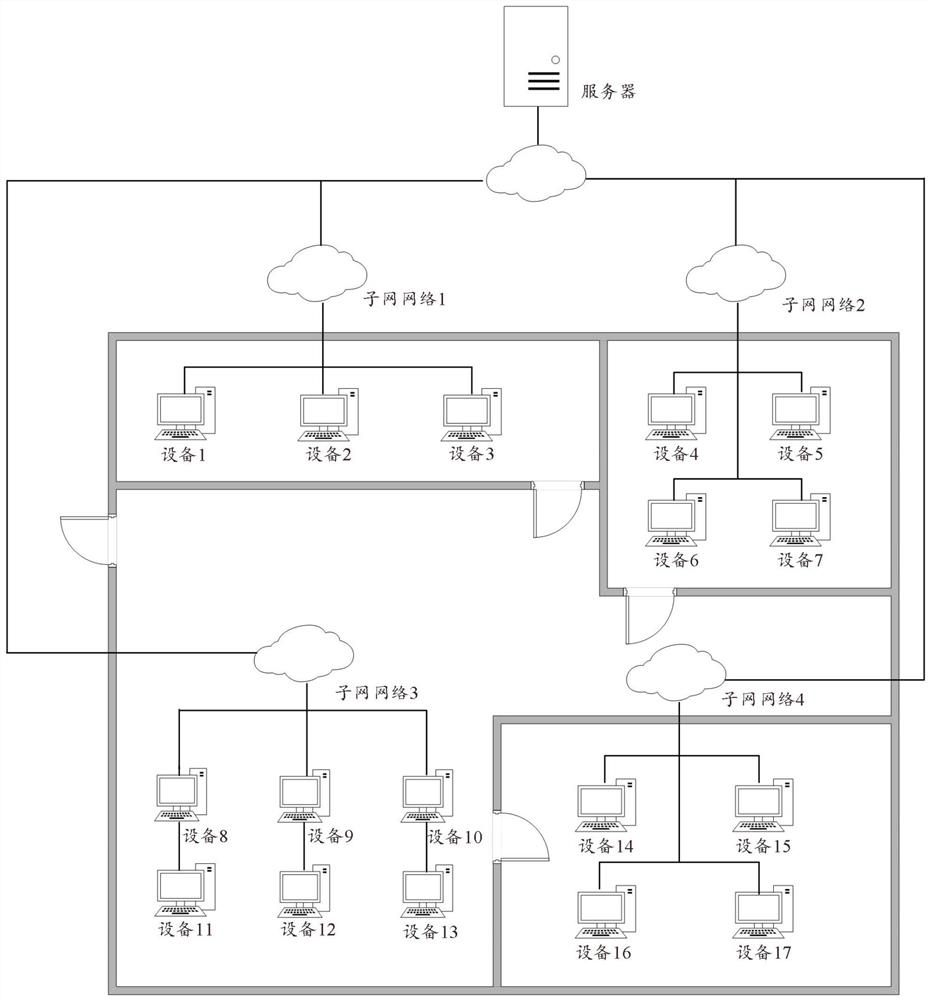
[0096] The data receiving module 302 is configured to receive border risk data sent by network peripheral sensors. The network peripheral sensors are deployed in the sub-network of the private network, and are used to detect border risk data of devices in the sub-network.
[0097] The data analysis module 303 is used to analyze the boundary risk data, determine the security risk level of the private network and determine the risky equipment in the private network.
[0098] The display module 304 is configured to mark risky devices in the electronic device map, and display the mar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com