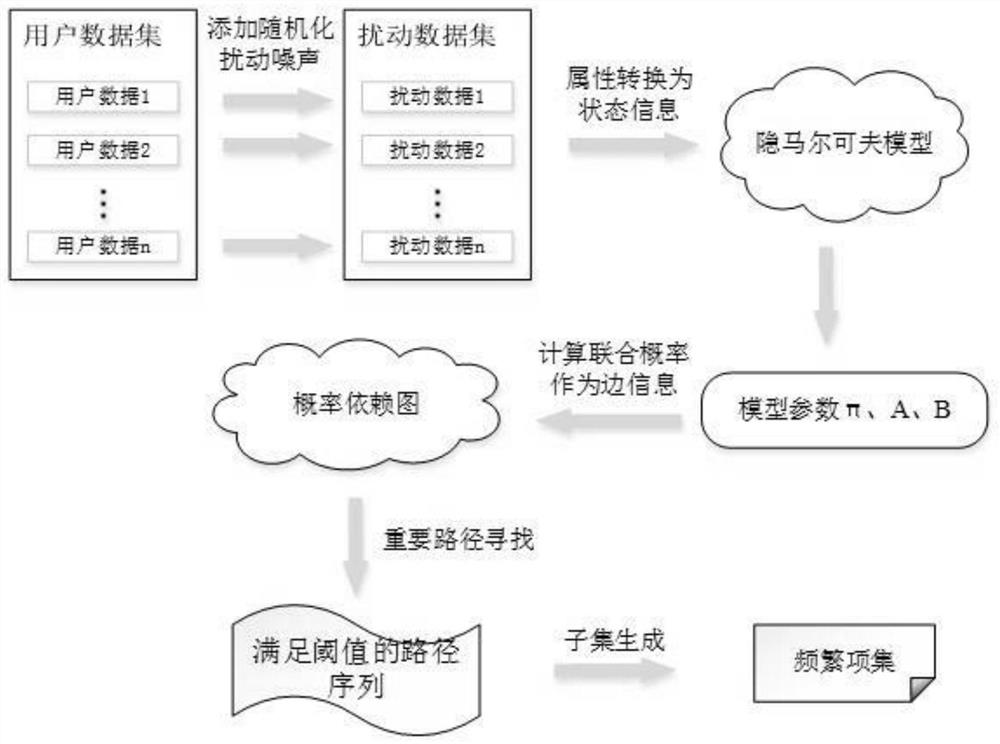
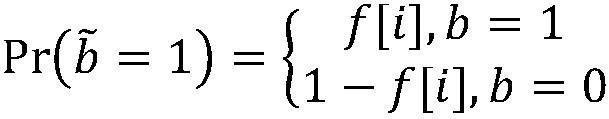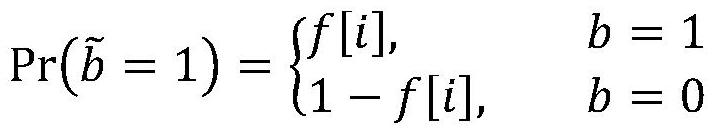Frequent item set mining method based on localized differential privacy
A technology of frequent itemset mining and differential privacy, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problems of reduced quality of mining results, reduced privacy protection intensity, high communication costs, etc., to reduce privacy budget Consumption and communication costs, reducing the privacy budget segmentation problem, and improving the effect of data accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0020] Example 1: The number of users is N=10, and the data sets it owns are as follows. For the convenience of description, all attribute values are replaced by numbers:
[0021]
[0022] Step 1: As can be seen from the above table, the user has 4 attributes, and each attribute has 2 attribute values, so the value range of the data set Ω 1 ={0,1},Ω 2 ={2,3},Ω 3 ={4,5},Ω 4 ={6,7}, m=8. For convenience, the support threshold δ=0.015 is defined, and all attribute values are directly converted to their corresponding binary forms, for example, 5=101 2 , substituting the f array calculation function to get the parameter array of the perturbation function:
[0023] f=[0.5,0.5,0.5,0.5]
[0024] Substituting the disturbance function into the calculation can obtain the form of the corresponding disturbance function:
[0025]
[0026] Step 2: Use random responses to perturb the user data set to obtain the perturbed data set As follows:
[0027]
[0028]
[002...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com