Link encryption processing method and device, link decryption processing method and device and computer equipment
A technology of encryption processing and processing methods, which is applied in the field of Internet security, can solve problems such as easy cracking, and achieve the effects of improving security, avoiding strings that are too short, and preventing false registration behaviors or leakage of private information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] Below, reference will be figure 1 with figure 2 An embodiment of a link encryption processing method of the present invention is described.
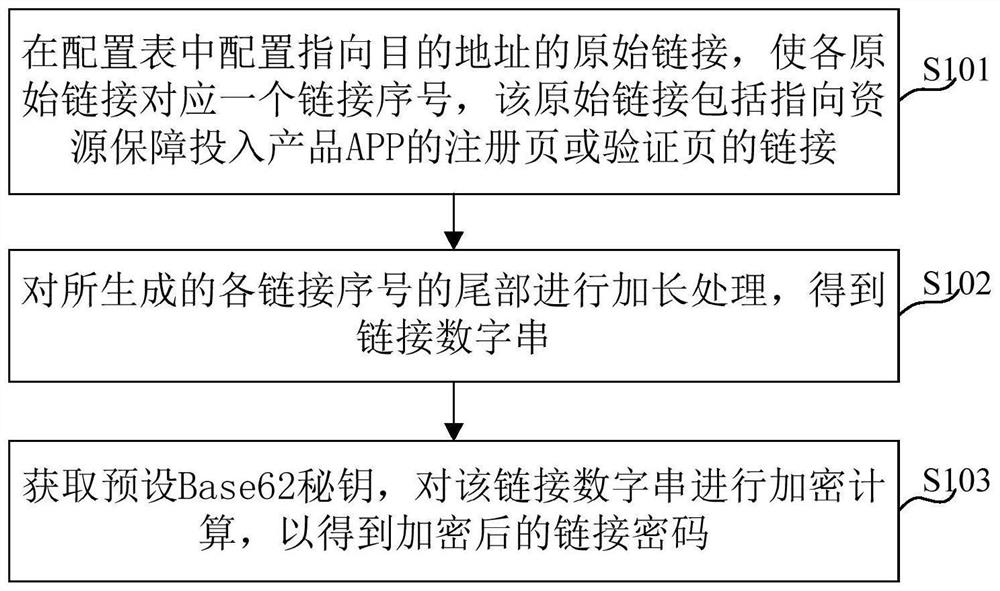
[0040] figure 1 A flowchart of a link encryption processing method of the present invention. like figure 1 As shown, the method includes the following steps.
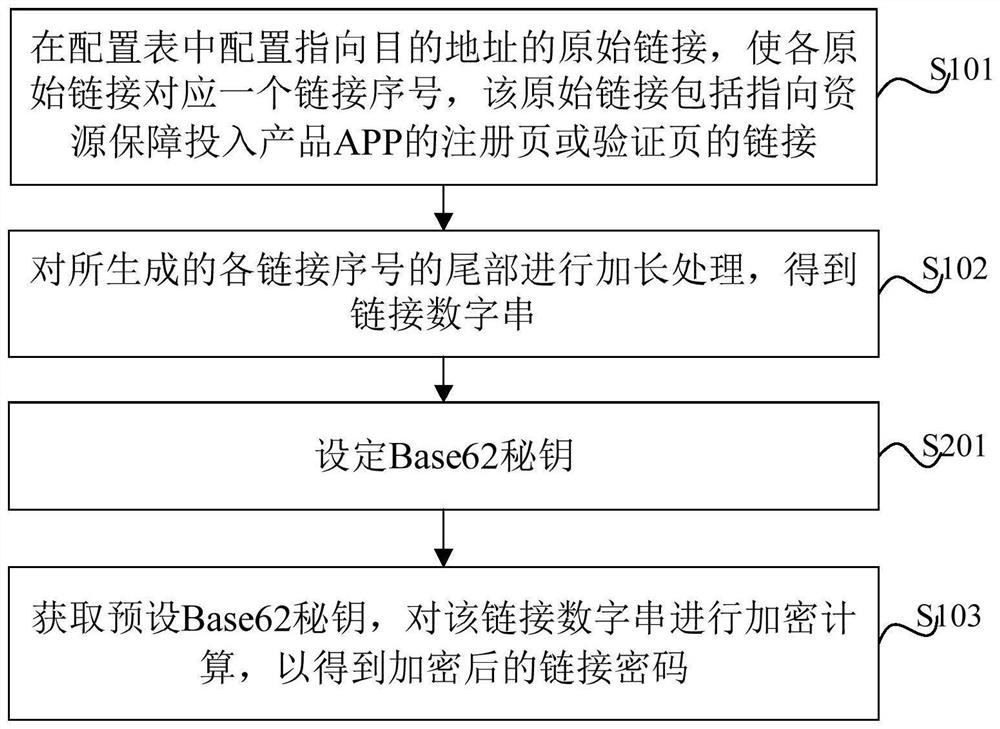
[0041] Step S101, configure the original link to the destination address in the configuration table, so that each original link corresponds to a link sequence number, which includes a link to a registration page or a verification page for a resource support to enter the product APP.
[0042] Step S102, the length of the generated link sequence number is processed to obtain a link number string.
[0043] Step S103, acquire the preset base62 secret, encrypt the link number string to obtain the encrypted link password.
[0044] In the present invention, the link encryption processing method is used to encrypt the link associated with the resource security input. For example, the ...
Embodiment 2
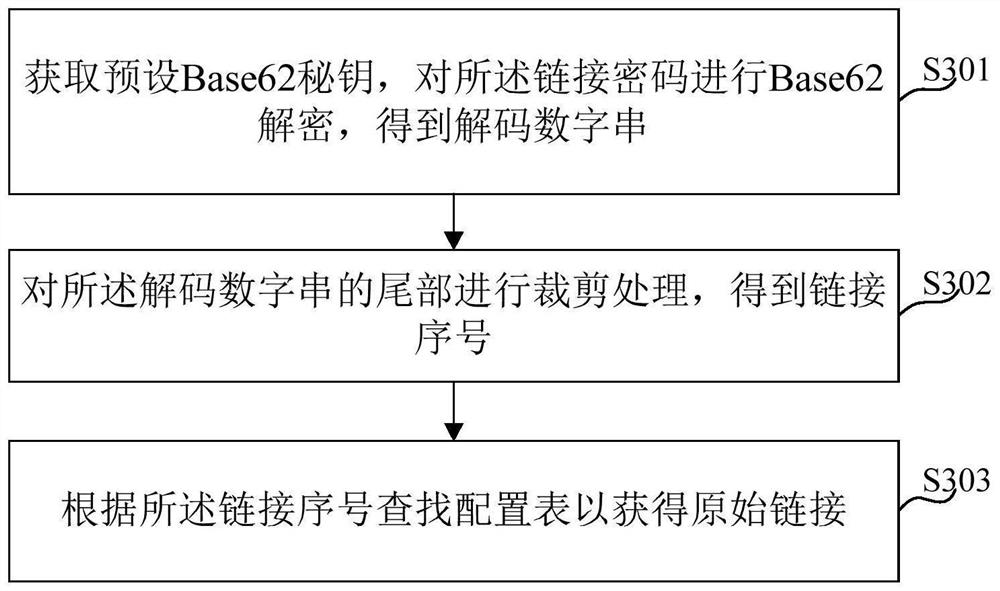
[0076] Refer image 3 with Figure 4 The present invention also provides a link decryption processing method for decrypting a link password for encrypting the link encryption processing method described in Example 1, comprising the steps of:
[0077] In step S301, obtain the preset base62 secret key, and the Base 62 is decrypted to obtain a decoded number string.
[0078] In step S302, the tail of the decoded number string is cropped to obtain a link sequence number.
[0079] Step S303 lookup the configuration table according to the link sequence number to obtain the original link.
[0080] In the present embodiment, the link decryption processing method is particularly suitable for decrypting the link password obtained in Example 1.
[0081] like Figure 4 As shown, the link decryption processing method includes step S401 that acquires the link password to be decrypted.
[0082] In step S401, the link password to be decrypted is acquired to decrypt the decryption process.
[0083] P...
Embodiment 3
[0094] The apparatus embodiment of the present invention is described below, which can be used to perform the method embodiment of the present invention. For the details described in the embodiment of the present invention, it is considered to be supplemented with the above method embodiments; for details not disclosed in the embodiment of the present invention, it is achieved in accordance with the above method embodiment.
[0095] Refer Figure 5 with Image 6 The present invention also provides a link processing device 500 for encrypting or decrypting a link associated with resource security input, which includes: configuring module 501 for configuring the destination address in the configuration table. The original link enables each original link to correspond to a link sequence number, which includes links to the registration page or verification page of the resource to support the product APP; the long processing module 502 is used to extend the end of the generated link seque...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com