Buffer overflow attack defense method and device based on RISC-V and Canny mechanisms
A RISC-V, buffer overflow technology, applied in the computer field, can solve problems such as limited scope of application, difficulty in landing, lack of protection, etc., and achieve the effect of small system performance and good defense effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] Below in conjunction with accompanying drawing, the present invention will be further described.
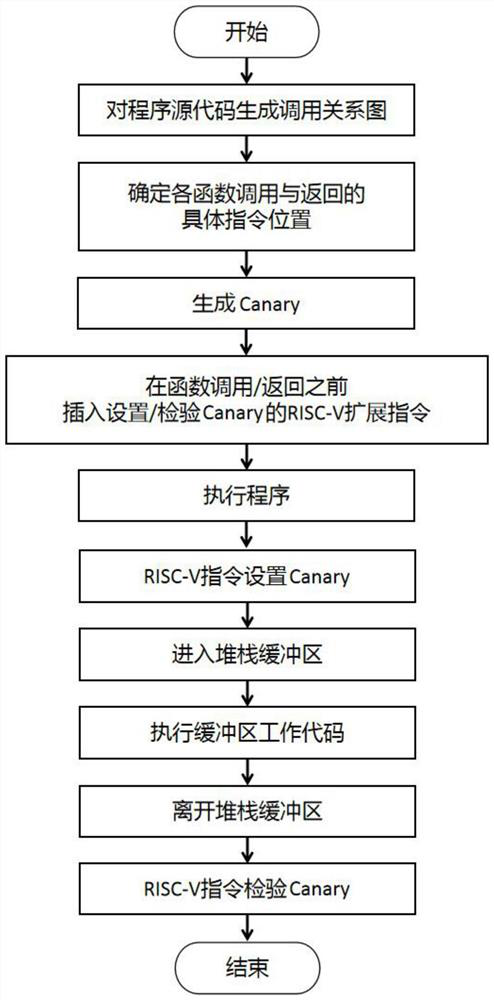
[0065] This embodiment is based on the buffer attack defense method of the Canary mechanism, wherein the overall process is as follows figure 1 As shown, it mainly includes the following steps:
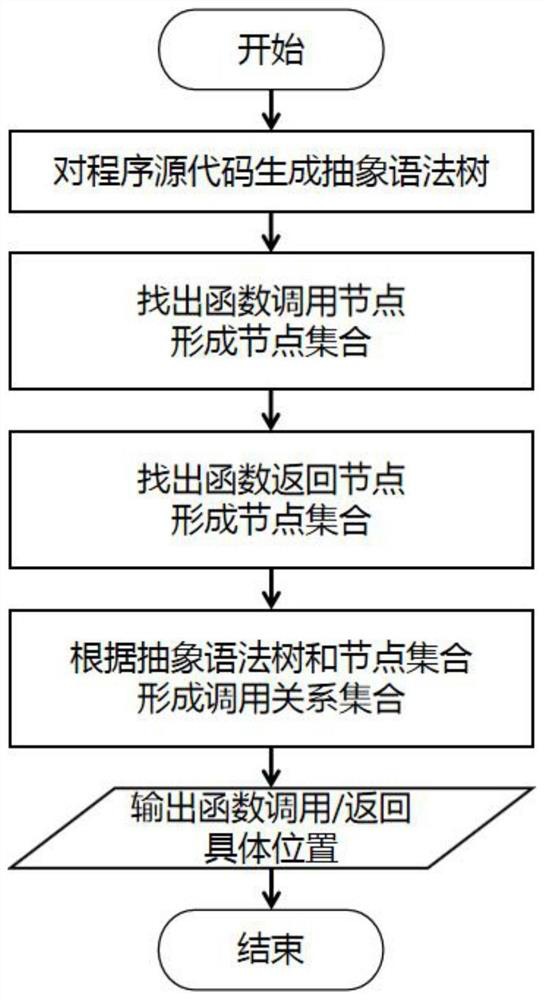
[0066] 1) Analyze the source code of the program, generate a node call relationship diagram, and determine the specific instruction positions of each function call and return, wherein the function call will be recognized as a call instruction, and the function return will be recognized as a ret instruction. The node call relationship graph is a joint data structure that combines various node sets and node relationship sets. Its structure G=(V C , V R , R, nentry), where V C is the set of function call nodes, V R is a collection of function return nodes, R is a collection of corresponding relationships between function calls and return nodes, and nentry is the entry node of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com