Multivariate identity authentication method and system for power grid data outsourcing calculation
A technology of identity authentication and data outsourcing, which is applied in the field of multiple identity authentication methods and systems, can solve problems such as being vulnerable to viruses, Trojan horses, identity counterfeiting, client platform access to the network, user network threats, etc., to achieve true and effective identities, ease Network security pressure, the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The following descriptions of various embodiments refer to the accompanying drawings to illustrate specific embodiments in which the present invention can be implemented.
[0055] Please also refer to figure 1 and figure 2 As shown, Embodiment 1 of the present invention provides a multi-identity authentication method for power grid data outsourcing calculation, including:
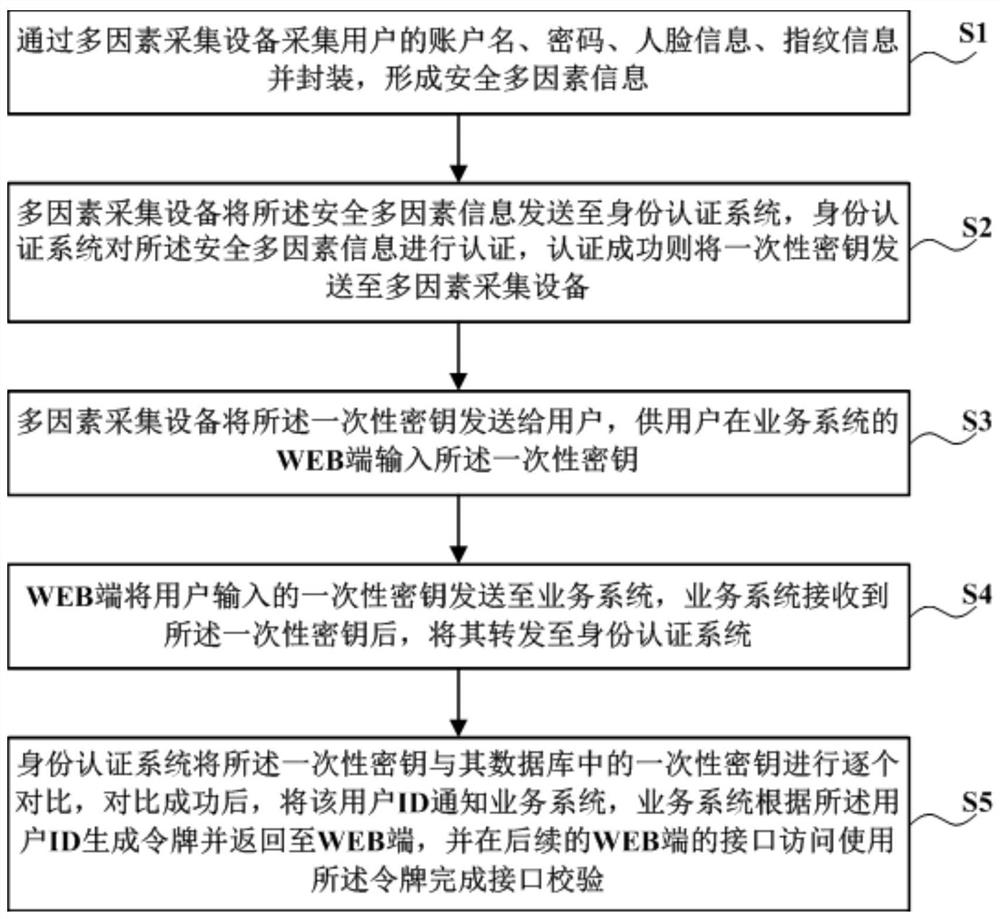
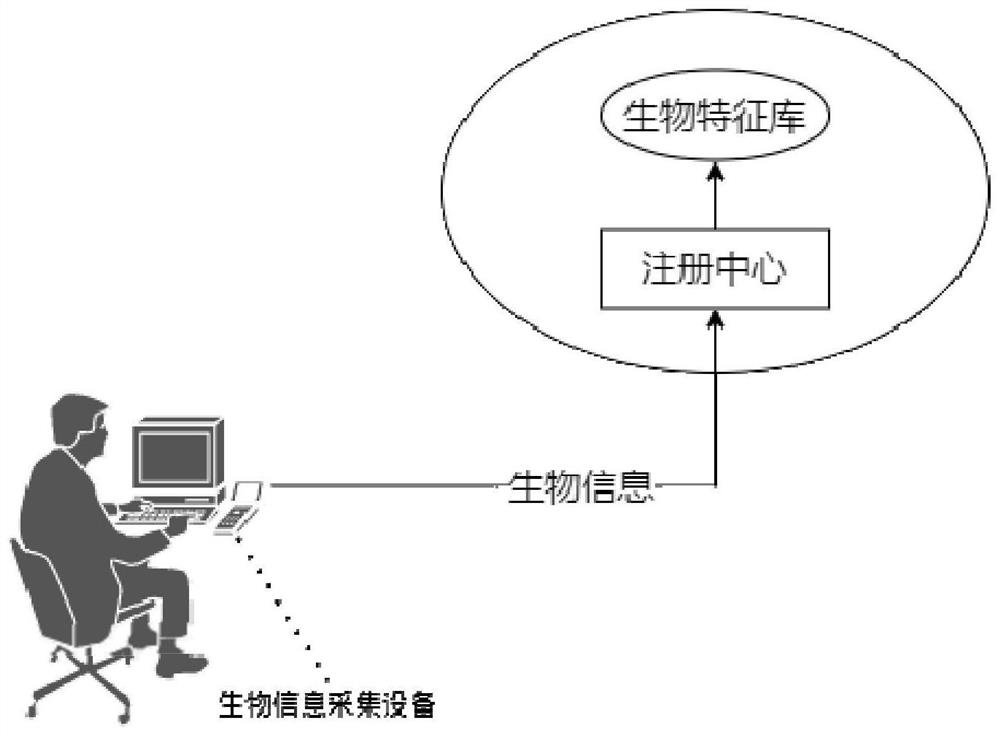
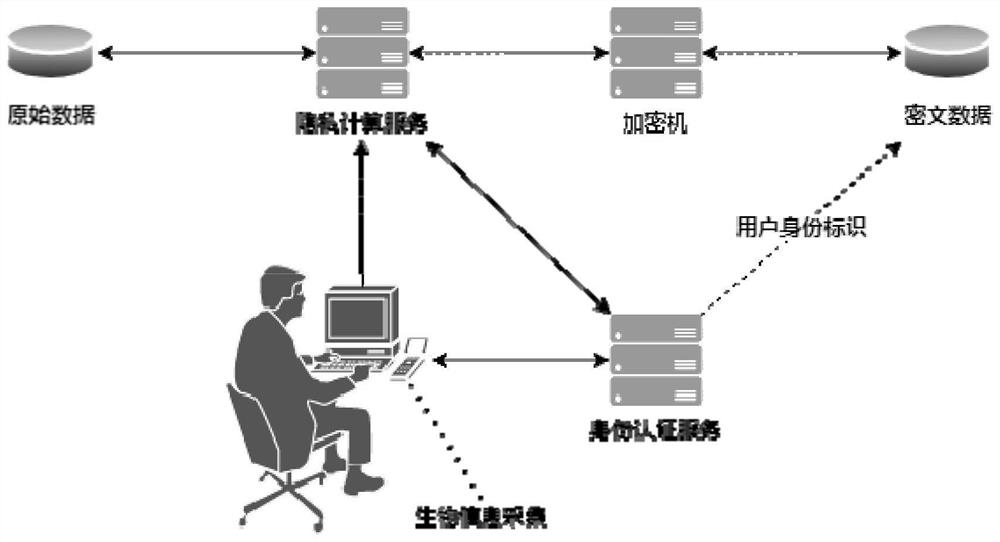
[0056] Step S1, simultaneously collect multiple biometric information of the user through the biometric information collection device and send them to the identity authentication server, and the identity authentication server will verify the biometric information; Verification, if the verification is successful, an application token for the user to access the privacy computing server is generated to complete the identity authentication of the user;
[0057] Step S2, the power grid data computing entrusting party and the computing party generate a session key by continuously exchanging intermediate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com