Secure communication method based on intelligent vehicle
A technology for secure communication and smart cars, applied in the field of secure communication of smart cars, can solve problems such as hidden safety hazards, inability to verify the integrity of messages, and theft of smart cars, to prevent camouflage, prevent tampering with communication content, and ensure identity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
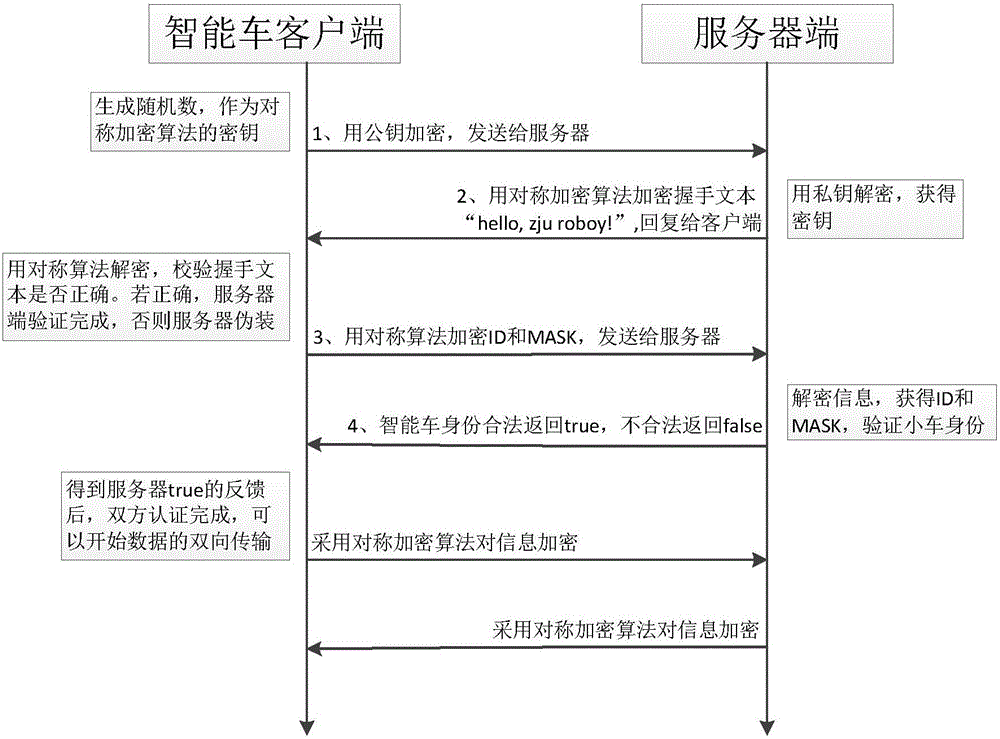
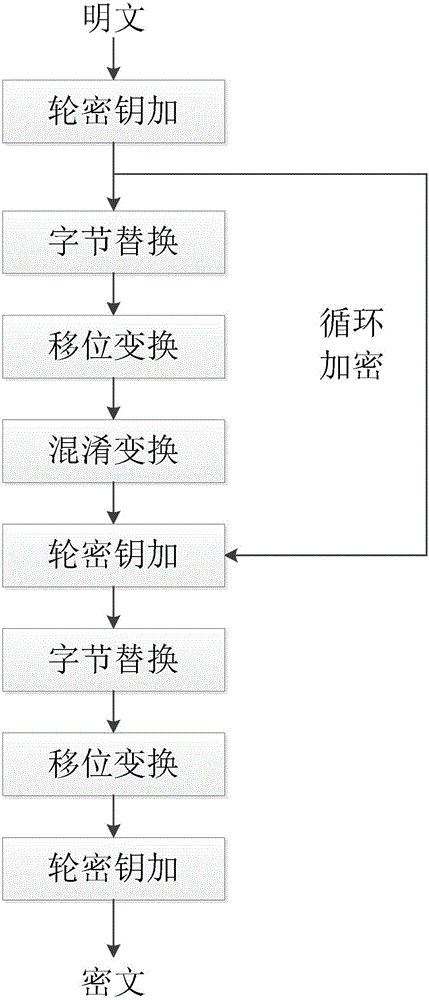
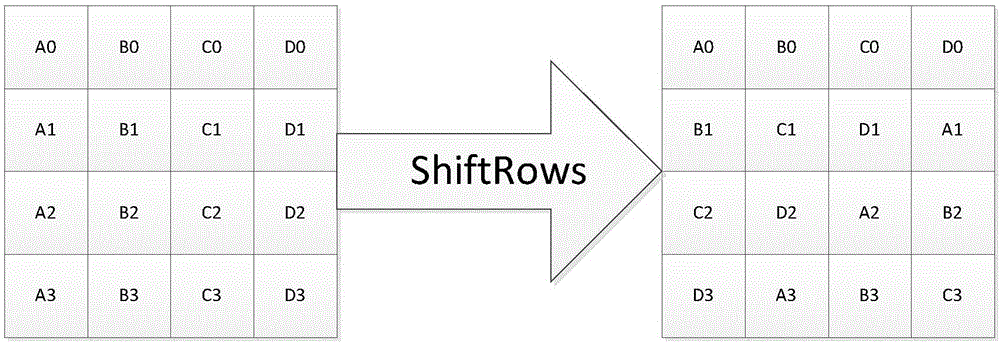
[0030] In order to make the technical solution of the present invention clearer, the following in conjunction with the attached Figures 1 to 3 , the present invention will be described in detail. It should be understood that the specific implementations described in this specification are only for explaining the present invention, and are not intended to limit the protection scope of the present invention.
[0031] Each smart car will be assigned a globally unique smart car number when it leaves the factory, and there is also a MASK value corresponding to the number one by one, which is equivalent to the password of the smart car. The server is assigned a pair of public key and private key, and the public key of the server is built in when the smart car leaves the factory. The safe communication method of smart car of the present invention is realized through the following steps:
[0032] Step 1: The smart car client randomly generates a number, which is used as the key of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com