A poisoning attack method for electromagnetic signal modulation type identification based on a pure label
An electromagnetic signal, modulation type technology, applied in neural learning methods, character and pattern recognition, biological neural network models, etc., can solve problems such as poisoning, classifier performance impact, and difficulty in implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be further described below with reference to the accompanying drawings.
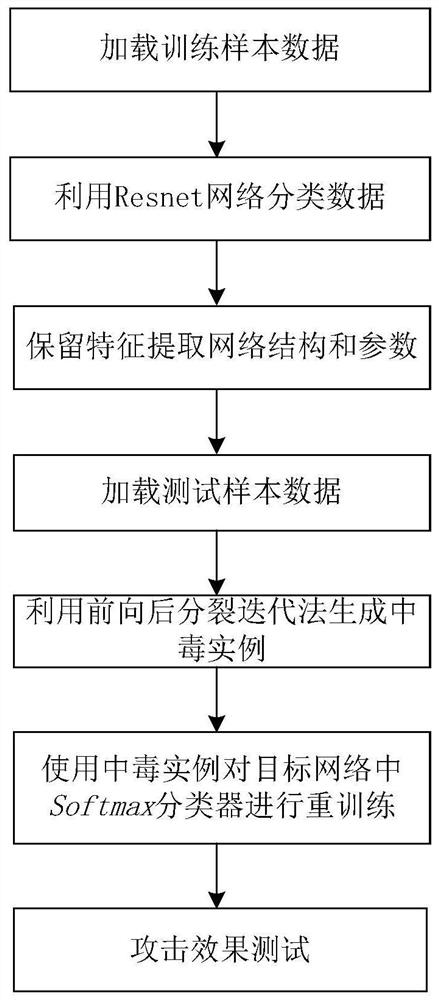
[0019] Refer Figure 1 ~ 3 An electromagnetic signal modulation identification of pure poisoning attacks based label, comprising the steps of:
[0020] 1) for electromagnetic data signal preprocessing
[0021] The signal is divided into a training data set and test set, and the data signal is normalized, the normalized data signal with its modulation type tag samples by X and Z, respectively, X = {x 1 , X 2 , ..., x n }, The following normalized equation:
[0022]
[0023] Where X i The normalized signal sample representation, Represents the original signal samples, n-represents the total number of signal samples, signal i is the i-th data set samples, It represents the minimum value of the signal samples, It represents the maximum value of the signal samples.
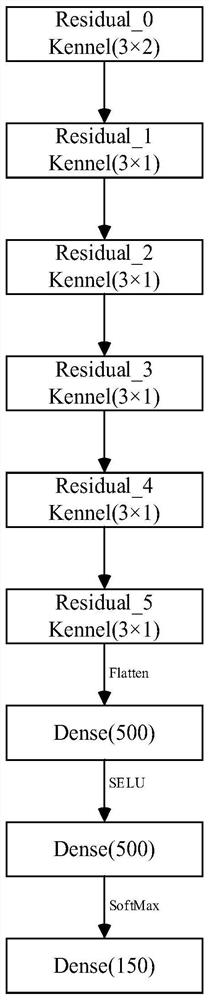
[0024] 2) Set up an electromagnetic signal classification model
[0025] Signal classification model used in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com