Recognition method for detecting software vulnerability with weight deviation based on graph neural network
A software vulnerability and neural network technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the technical solutions and advantages of the present invention more clear, the technical solutions in the embodiments of the present invention are clearly and completely described below in conjunction with the drawings in the embodiments of the present invention:
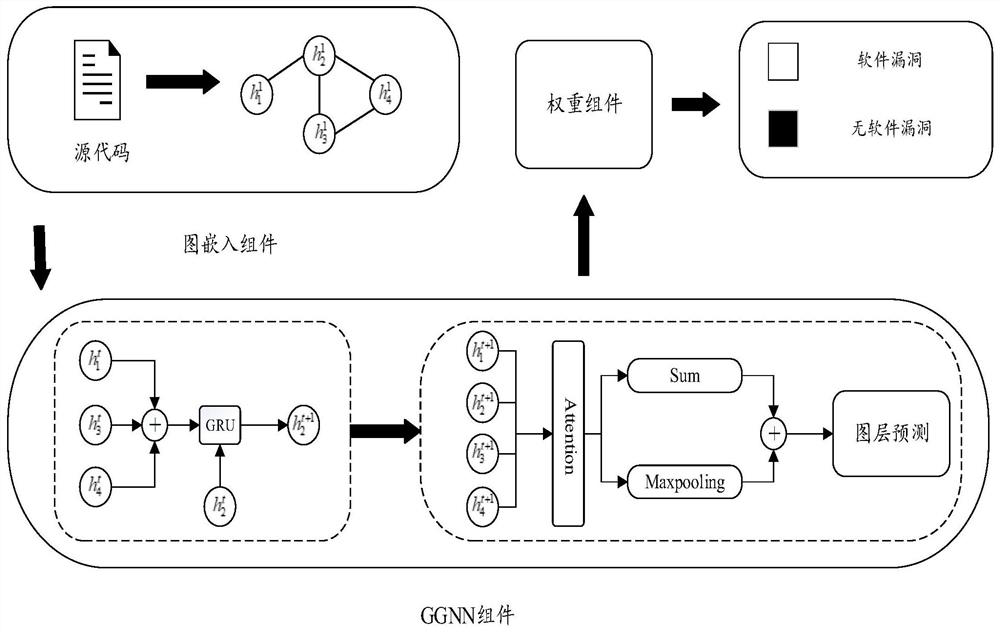
[0028] Such as figure 1 A method for identifying software vulnerabilities with weight bias based on a graph neural network is shown, which specifically includes the following steps:
[0029] Step 1: Graph Embedding Model
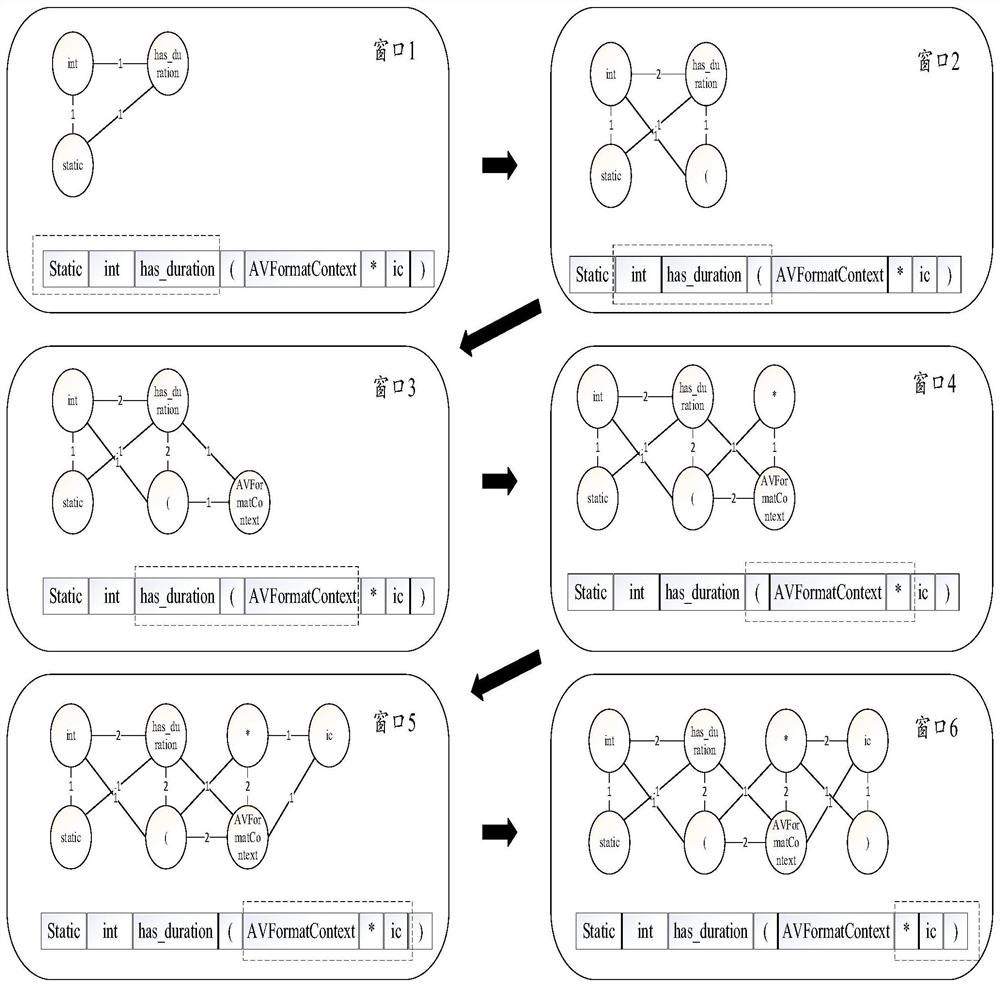
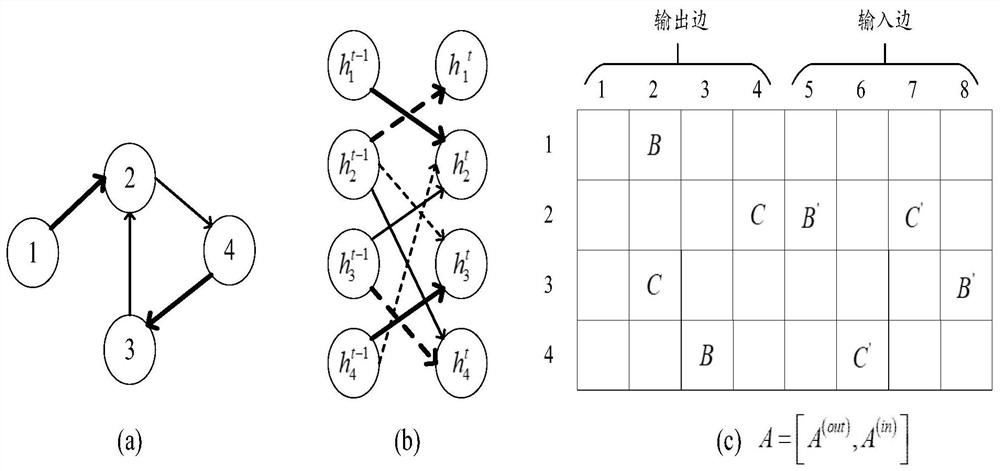
[0030] The words and symbols in the source code are regarded as a node, and the source code composition graph representation G={V,E} is used as the input of GGNN. V represents a point set, and E represents an edge set. First, you need to obtain the initial eigenvalues of each node, and you also need to obtain the initial characteristics of the connected edges of each graph. For the initial feature of the edge, the graph embedding model uses the NL Graph Embedding meth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com