Public key parsing method, device, device and storage medium based on sm2 signature
An analysis method and public key technology, applied in the field of information security, can solve the problems of reducing the security of SM2 signature algorithm, reducing the security of SM2 algorithm signature, incompatibility with SM2 signature algorithm and signature verification algorithm, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0085] First, the symbols, abbreviations and symbols used in this embodiment will be described.
[0086] A and B: Two users of the SM2 public key cryptosystem, A is the signer and B is the signer verification.
[0087] q : finite field F q the number of elements in .
[0088] F q : a finite field containing q elements.
[0089] a, b: F q elements in , which define F q on an elliptic curve E.
[0090] E (F q ): F q The set of all rational points of the upper elliptic curve E.
[0091] O: The infinity point (or zero point) on the elliptic curve E, which is the identity element of the additive group of the elliptic curve.
[0092] G: A base point of an elliptic curve whose order n is a prime number.
[0093] #E (F q ): E (F q ), the number of points on the elliptic curve E (F q ) of the order.
[0094] n : The order of the base point G.
[0095] [k]P: point k times the point P on the elliptic curve.
[0096] d A , d B : are the private keys of user A and user B,...
Embodiment 2
[0121] The signs, abbreviations, and symbols used in this embodiment are the same as those in Embodiment 1, and will not be repeated here.
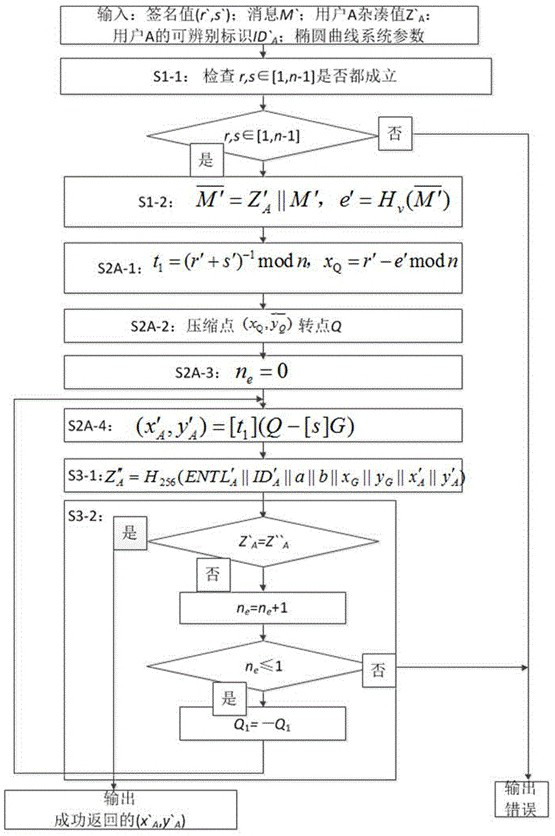
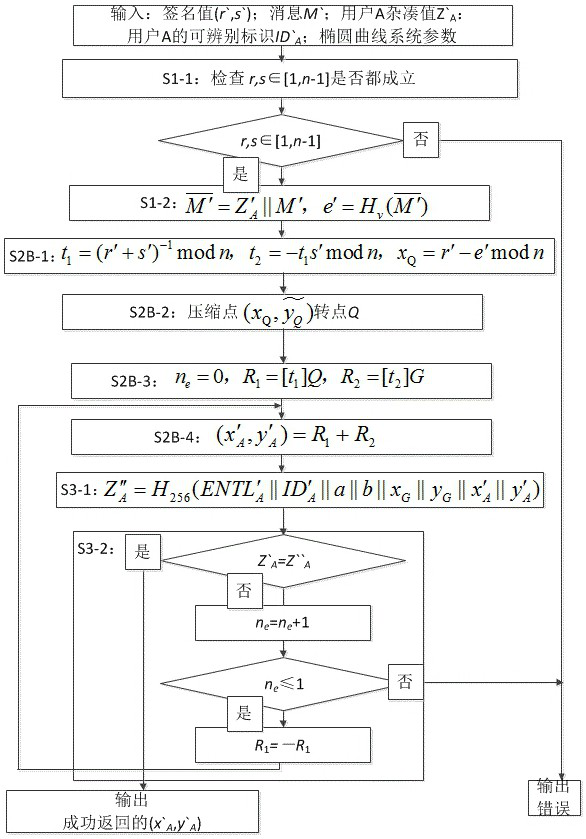
[0122] as attached figure 2 As shown, it is a flow chart of the public key parsing method based on SM2 signature provided by this embodiment, and the method specifically includes the following steps:
[0123] S1: Enter the standard SM2 signature value (r', s'), the digitally signed message M', the hash value of the signer , the identifiable identification of the signer and elliptic curve system parameters, elliptic curve system parameters include elliptic curve equation parameters a, b, base point G = (x G , y G ) and the base point of order n, check the input parameters and calculate the hash value calculation.
[0124] S1-1: Convert the data types of r' and s' to integers according to the stipulations of data type conversion in Section 4.2 of the SM2 standard GB / T 32918.1, and check and are all established. If one of them is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com