Threat disposal method and safety monitoring probe for Android application
A disposal method and probe technology, which is applied in the field of security monitoring probes, can solve problems such as damage to user interests, weak certificate verification, and theft, and achieve the effects of effective progressive disposal methods, high security disposal capabilities, and reduced security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0026] In order to improve the security of Android applications, security monitoring and security reinforcement protection are usually required before Android applications go online to reduce the impact of application vulnerabilities and the risk of being reversed. However, when the application is running online, there are still security risks such as being attacked and cracked, unauthorized use, and sensitive data theft.
[0027] To solve this problem, the present invention provides a threat handling method for Android applications. The execution subject of the threat handling method for Android applications is a security monitoring probe provided to the Android application in the form of an SDK. When the Android application is running, the security monitoring probe It can monitor and listen to the threat behaviors that pose security risks to Android applications, such as abnormal running environment and sensitive behaviors in the application, and generate threat behavior sequ...
Embodiment 2
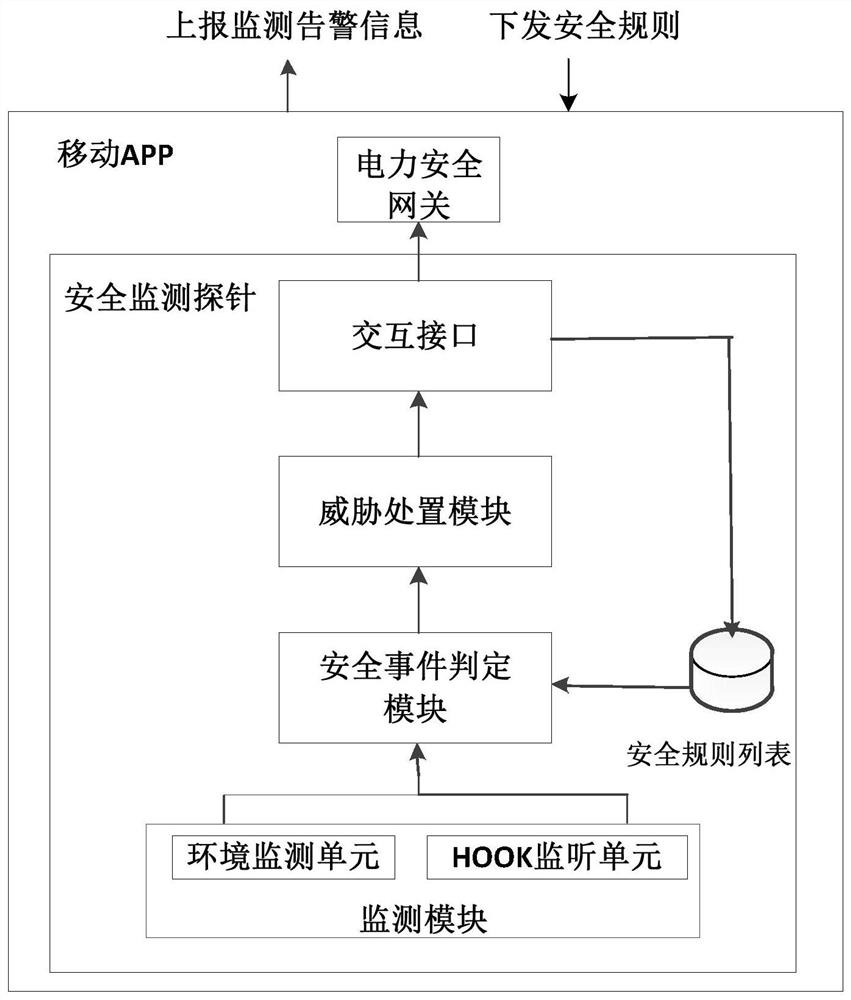
[0084] The present invention provides a security monitoring probe for Android applications, such as figure 2 As shown, the probes include:
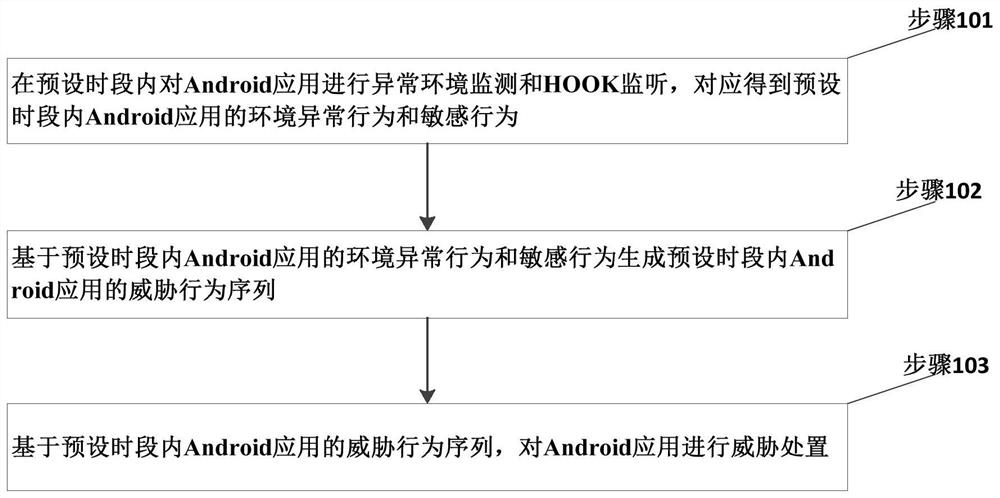
[0085] The monitoring module is used to monitor the abnormal environment and HOOK monitoring of the Android application within a preset period of time, and correspondingly obtain the abnormal environmental behavior and sensitive behavior of the Android application within the preset period of time;
[0086] A security event judgment module, configured to generate a threat behavior sequence of an Android application within a preset period based on the environmental abnormal behavior and sensitive behavior of the Android application within a preset period;
[0087] The threat handling module is configured to perform threat handling on the Android application based on the threat behavior sequence of the Android application within a preset period of time.
[0088] Preferably, the probe also includes:
[0089] The interactive interface is us...
Embodiment 3
[0126] In order to verify the effectiveness of the technical solution provided by the present invention, use the method provided by the present invention to perform threat treatment on an Android application and use the traditional method to perform threat treatment on an Android application, and obtain the threat treatment effects of the two;
[0127] The method provided by the present invention is used to deal with threats to an Android application, and its flow is as follows Figure 4 shown, including:
[0128] Initialize the start time of the life cycle, and make the number of triggers of various sensitive behaviors be 0;
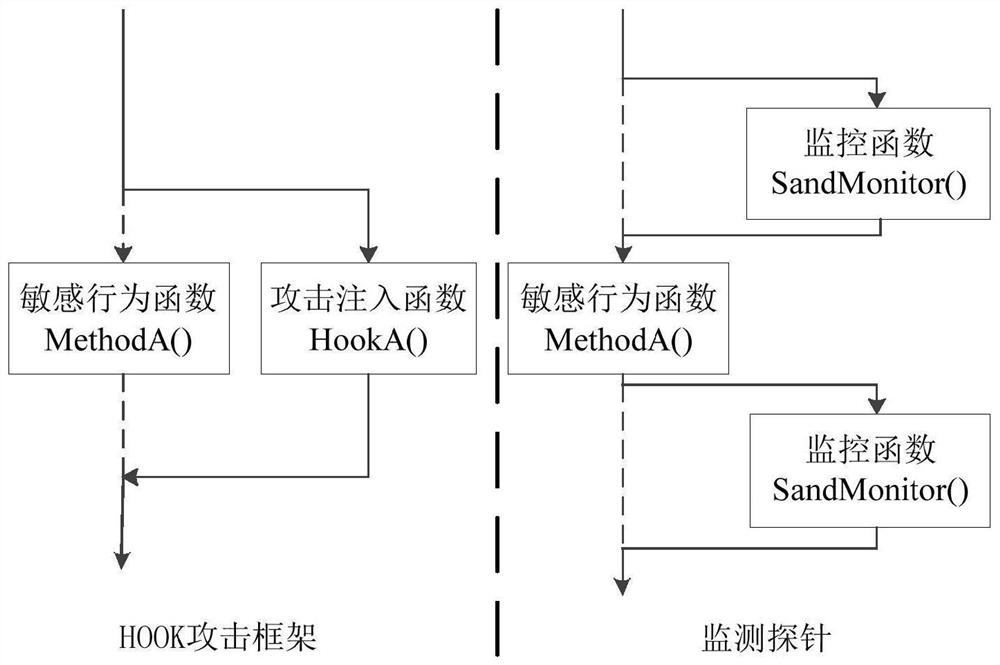
[0129] Step 1: The abnormal environment monitoring unit monitors the abnormal behavior of the environment, and if triggered, records the corresponding abnormal behavior of the environment;
[0130] Step 2: The HOOK monitoring unit monitors the sensitive behavior of the monitored application, if triggered, records the corresponding sensitive behavior an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com