Data access method and device, electronic equipment and storage medium
A data access and data technology, applied in the Internet field, can solve problems such as high labor costs and high error rates, and achieve the effects of solving high labor costs, avoiding access conflicts, and solving high error rates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
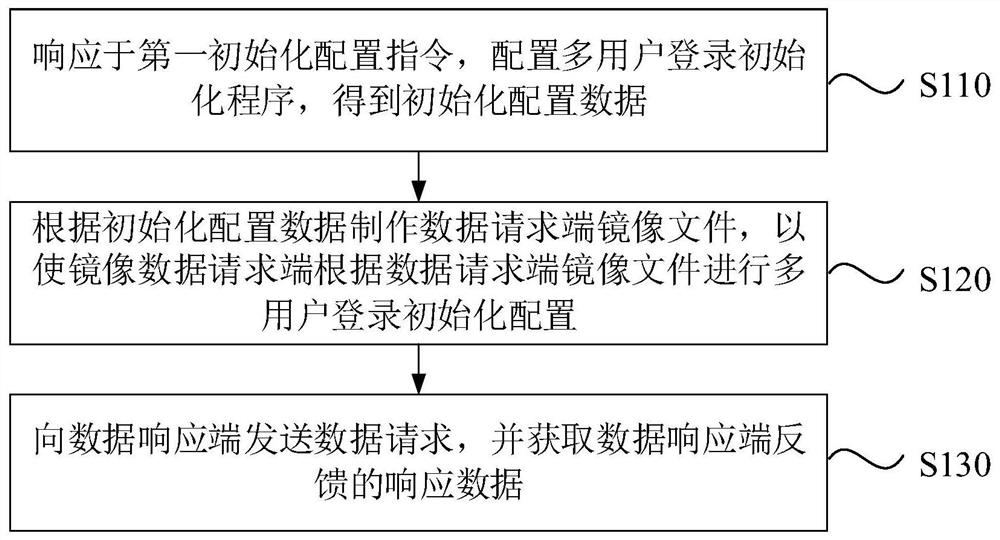
[0037] figure 1 It is a flow chart of a data access method provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation where multiple users efficiently access the same data. The method can be executed by a data access device, which can be implemented by software and / or It is realized by means of hardware, and generally can be integrated in electronic equipment. Correspondingly, such as figure 1 As shown, the method includes the following operations:
[0038] Usually, only one user is allowed to log in at the data requesting end, or at most two users are allowed to log in to the same data requesting end after user login settings are configured. However, in the actual business execution process, multiple users are often required to log in to the same data requesting end. At present, the multi-user login setting of the data requesting end is mainly set manually. When it is necessary to set the multi-user login setting of multiple data reque...
Embodiment 2
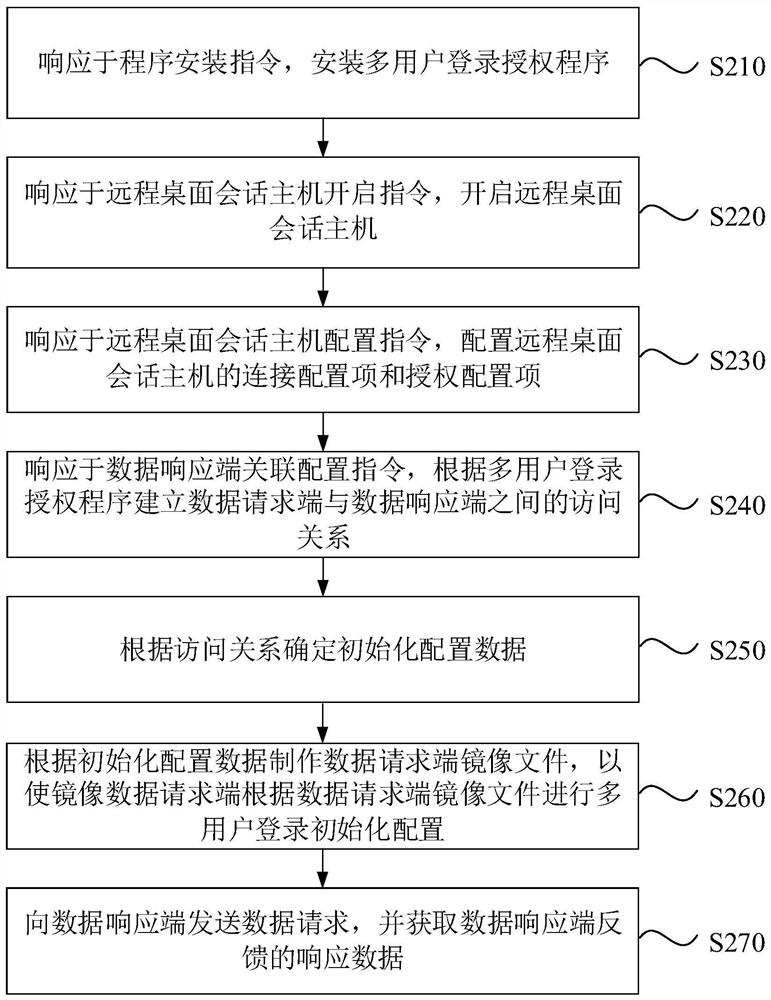
[0055] figure 2 It is a flowchart of a data access method provided by Embodiment 2 of the present invention. This embodiment is embodied on the basis of the above-mentioned embodiments. In this embodiment, it is limited that the first initialization configuration instruction may include program installation instructions and data Responder association configuration instructions, give specific optional implementation schemes for configuring multi-user login initialization program according to program installation instructions and data response end association configuration instructions, correspondingly, as figure 2 As shown, the method includes the following operations:
[0056] S210. Install the multi-user login authorization program in response to the program installation instruction.
[0057] Wherein, the program installation instruction may be used to install part of programs in the multi-user login initialization program. The multi-user login authorization program may b...
Embodiment 3
[0101] Figure 4It is a flow chart of a data access method provided by Embodiment 3 of the present invention. This embodiment is applicable to the situation where multiple users efficiently access the same data. The method can be executed by a data access device, which can be implemented by software and / or It is realized by means of hardware, and generally can be integrated in electronic equipment. Correspondingly, such as Figure 4 As shown, the method includes the following operations:
[0102] S310. Configure a multi-user login authorization program in response to the second initialization configuration instruction.
[0103] Wherein, the second initialization configuration instruction may be used to perform initial configuration of multi-user authorization on the data responder. The user login authorization program may be an application program corresponding to the initial configuration of multi-user authorization at the data response end, and is used to perform initial ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com