Private transaction processing method and device, electronic equipment and medium
A transaction processing and privacy technology, applied in the computer field, can solve problems such as protecting data privacy, achieve the effect of expanding application scenarios, increasing flexibility, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0065] figure 1 It is a flow chart of a privacy transaction processing method provided according to the first embodiment of the application. This embodiment is applicable to the situation of how to realize privacy transaction processing based on the blockchain, especially applicable to the scenario where the blockchain network is an alliance chain Next, how to meet the needs of protecting node data privacy. The privacy transaction processing method in this embodiment can be executed by a blockchain node. The method can be executed by a privacy transaction processing device, which can be implemented in the form of software and / or hardware, and can be integrated into a computing device carrying a block chain node. Such as figure 1 As shown, the privacy transaction processing method provided in this embodiment may include:
[0066] S110. Obtain a business transaction request to be executed.
[0067] In this embodiment, the business transaction request may be an unprocessed sm...
no. 2 example
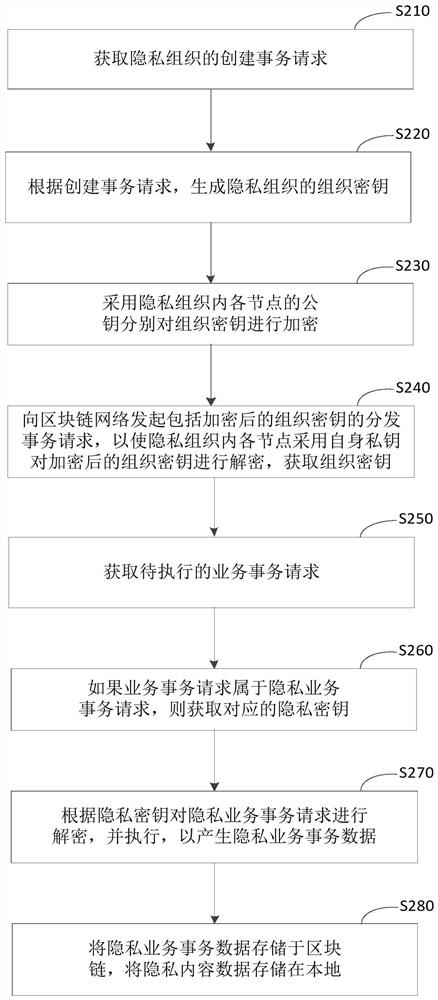
[0087] figure 2 It is a flow chart of a privacy transaction processing method provided according to the second embodiment of the present application. On the basis of the above embodiments, this embodiment adds a process of creating and producing an organization key by a privacy organization. like figure 2 As shown, the privacy transaction processing method provided in this embodiment may include:
[0088] S210. Obtain a transaction creation request of the privacy organization.
[0089] In this embodiment, the local node can receive the transaction creation request of the privacy organization initiated by any node in the blockchain network, and can also initiate the transaction creation request of the privacy organization locally. Exemplarily, the local node can obtain the transaction creation request of the privacy organization through at least one of the following methods: 1) If a privacy transaction requirement is generated, initiate a transaction creation request of the...
no. 3 example
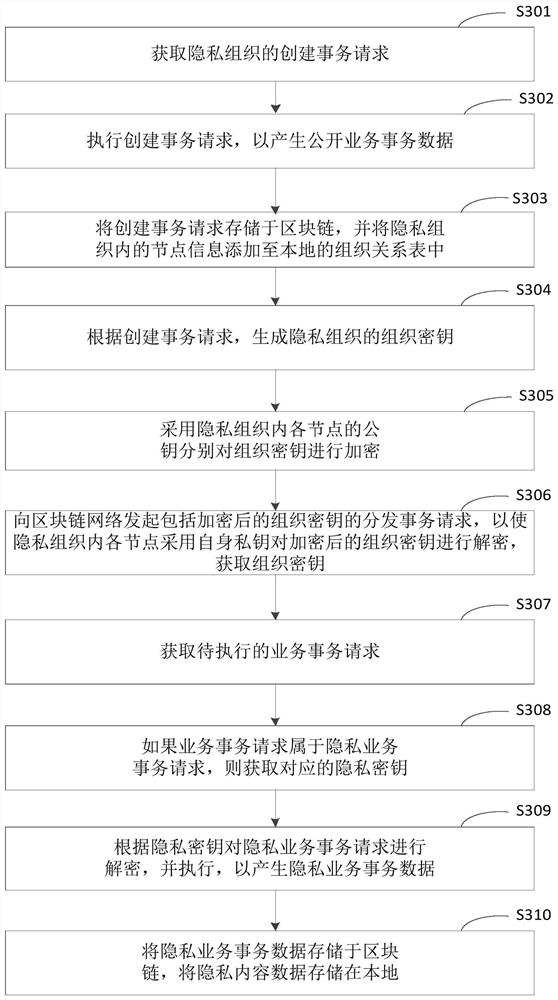
[0117] image 3It is a flow chart of a privacy transaction processing method provided according to the third embodiment of the present application. This embodiment adds a privacy organization management process on the basis of the foregoing embodiments. like image 3 As shown, the privacy transaction processing method provided in this embodiment may include:
[0118] S301. Obtain a transaction creation request of a privacy organization.
[0119] S302. Execute the transaction creation request to generate public business transaction data.
[0120] Optionally, regardless of whether the local node is a node in the privacy organization, after obtaining the transaction creation request from the privacy organization, the transaction creation request can be executed to generate public business transaction data. Wherein, the public business transaction data includes at least creating a transaction request and public content data, and the public content data includes node information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com