Manual transformation-free business application file management system and read-write and opening method
A file management system and business application technology, applied in the field of business application file management system, can solve problems such as business application file leakage, achieve the effect of improving integration efficiency and overcoming business application file leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
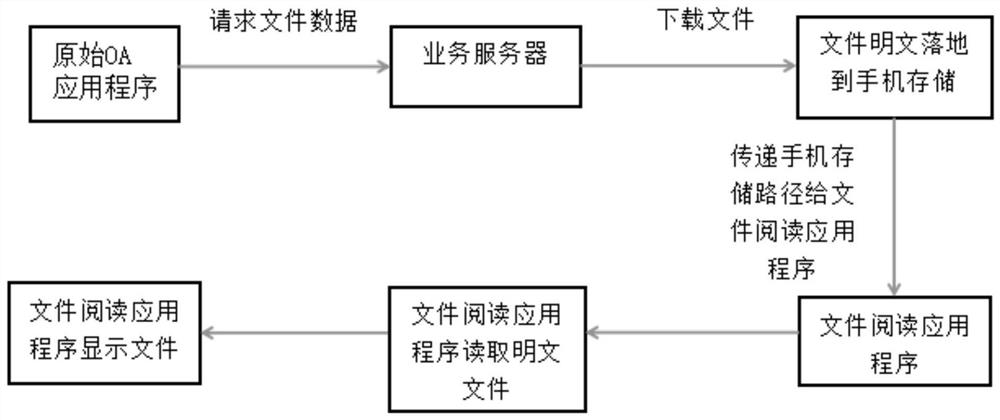
[0052] A business application file management system free of artificial modification, see figure 2 , the business application file management system is obtained by adding interception SDK to the original OA application;
[0053] The business application file management system adopts the method of intercepting the system file interface to automatically encrypt and decrypt the read and write operations of the business application file; adopts the method of intercepting the system response action to automatically encapsulate the original OA application program to realize the original OA application program. View preview of business application files.
[0054] The business application file management system free from artificial modification overcomes the problem of business application file leakage in the prior art, and greatly improves the SDK integration efficiency and the security of file reading through the modification-free program.
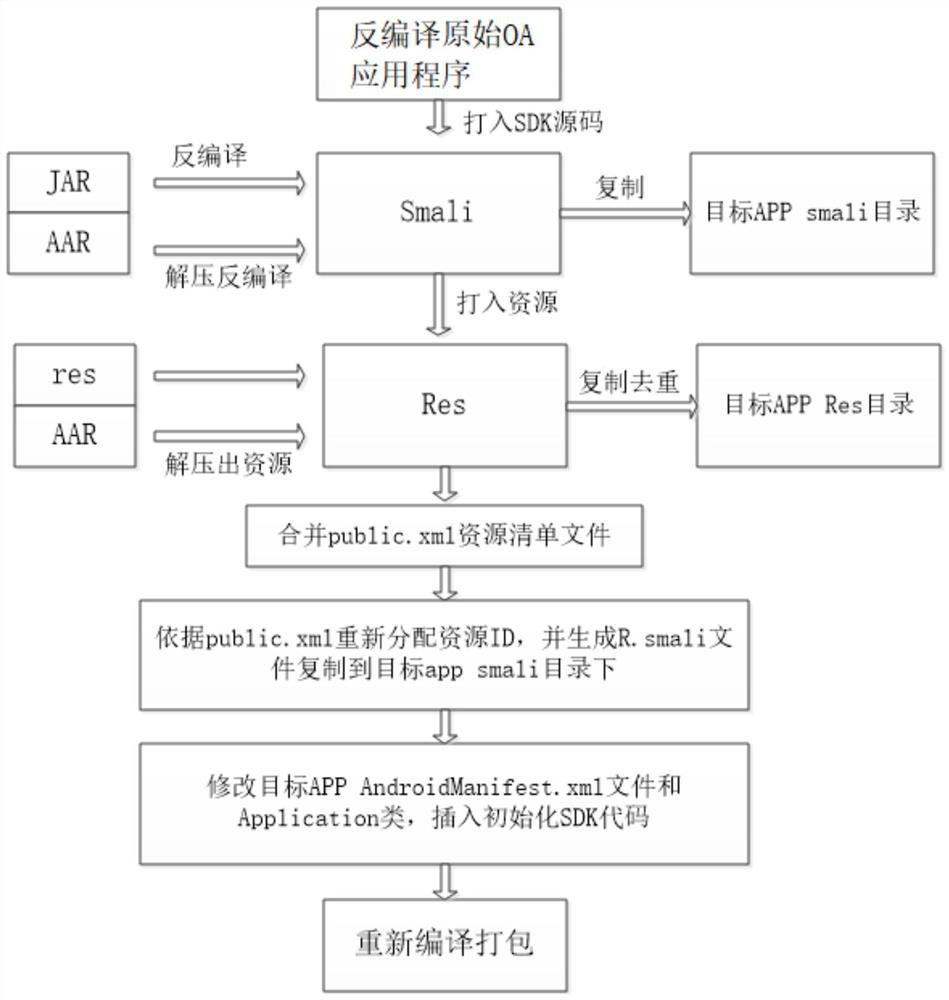
[0055] see image 3 , the business app...
Embodiment 2
[0081] A method of reading and writing based on the above-mentioned business application file management system, see Figure 4 , including the following steps:
[0082] After the business application file management system is started, add the SDK to intercept the initialization logic, and dynamically proxy the function;
[0083] Monitor the business application file management system to call the file IO read and write interface;
[0084] File stream encryption is performed on file IO write operations through the proxy interface class, and redirected to the sandbox file system;
[0085] The file IO read operation is redirected to the specified location of the sandbox file system through the proxy interface class and decrypted.
[0086] Specifically, the reading and writing method realizes interface function interception in the system through dynamic proxy technology, and performs file flow interception, encryption, decryption and redirection for operations involving file IO r...
Embodiment 3
[0089] A method for opening based on the above-mentioned business application file management system, see Figure 5 , 6 , including the following steps:
[0090] After the business application file management system is started, add the SDK to intercept the initialization logic, and dynamically proxy the function;
[0091] Monitor the business application file management system to call the system to open the file viewing interface action, and analyze to obtain the file type to be viewed;
[0092] Redirect to the interception SDK according to different file types through the proxy interface class to call different file reading components for parsing and display;
[0093] Check completion to monitor the closing action of the current page, close the display of the current file, and destroy the cached data.
[0094] Specifically, the opening implements the interface function interception through the dynamic proxy technology, and redirects the viewing response action of the busin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com