Method and system for improving security multi-party computing efficiency and storage medium
A secure multi-party computing and efficient technology, applied in the computer field, can solve problems such as large computing overhead and communication overhead, and achieve the effect of reducing computing overhead and communication overhead, improving computing efficiency, and ensuring that privacy is not leaked.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
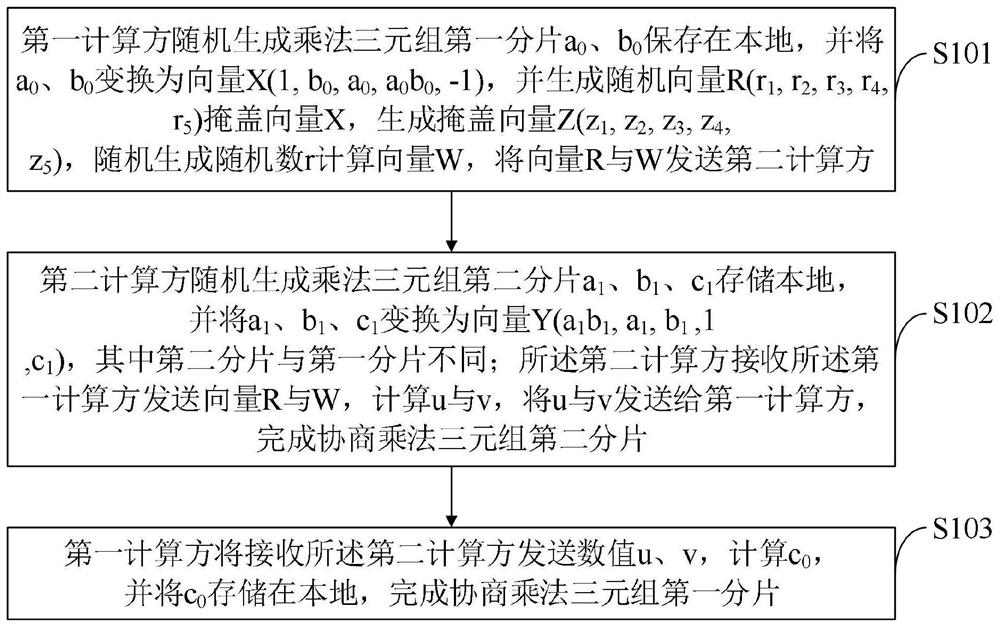
[0048] An aspect of the embodiments of this specification provides a method for improving the efficiency of secure multi-party computing, which is applied to the first computing party as follows: the first computing party randomly generates the first fragment a of the multiplication triplet 0 , b 0 Save it locally and convert it to a vector X=(1,b 0 ,a 0 ,a 0 b 0 ,-1), and generate a random vector R=(r 1 ,r 2 ,r 3 ,r 4 ,r 5 ) cover vector X, generate cover vector Z=X–R=(z 1 ,z 2 ,z 3 ,z 4 ,z 5 ), randomly generate a random number r to calculate the vector W=r*Z, and send the vector R and W to the second calculation party; the first calculation party receives the second calculation party to send its calculated data u, v; by calculating c 0 =u+v / r, put c 0 Stored locally; complete the first shard of the negotiated multiplication triplet.
[0049] One aspect of the embodiments of this specification provides a method for improving the efficiency of secure multi-part...
Embodiment 2
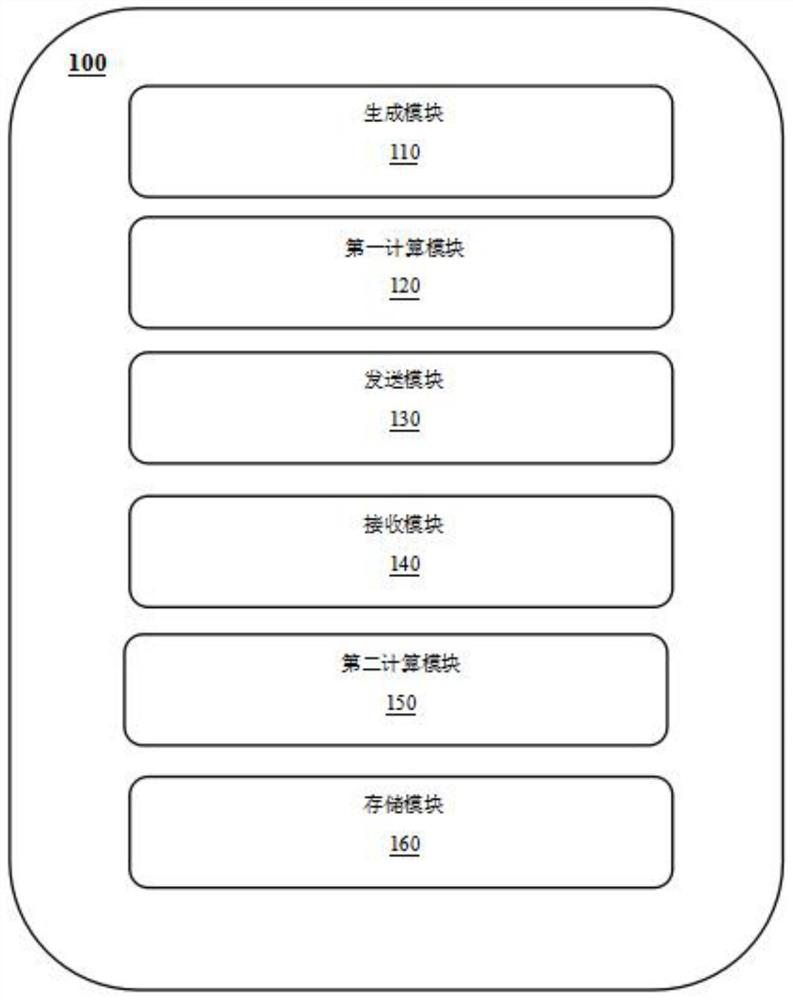
[0055] FIG. 2( a ) is a block diagram of a system 100 for improving the efficiency of secure multi-party computing.
[0056] As shown in FIG. 2( a ), the module includes a generating module 110 , a first computing module 120 , a sending module 130 , a receiving module 140 , a second computing module 150 and a storage module 160 . This module is mainly applied to the first computing party.
[0057] In some examples, the generating module 110 is configured to generate random numbers, generate a first slice a0, b0 of a multiplicative triple, and generate a random vector R and a value r.
[0058] In some examples, the first calculating module 120 is used to calculate the vector X and the vector W.
[0059] In some examples, the sending module 130 is used to send vectors R, W.
[0060] In some examples, the receiving module 140 is configured to receive the data u, v sent by the second computing party.
[0061] In some examples, the second calculation module 150 is used to calcul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com