A network security evaluation method, device, equipment and storage medium
A network security and evaluation method technology, which is applied in the network security evaluation method, equipment and storage media, and device fields, and can solve problems such as inability to adapt to network security requirements, network security assessment methods that cannot achieve accurate network security assessment, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
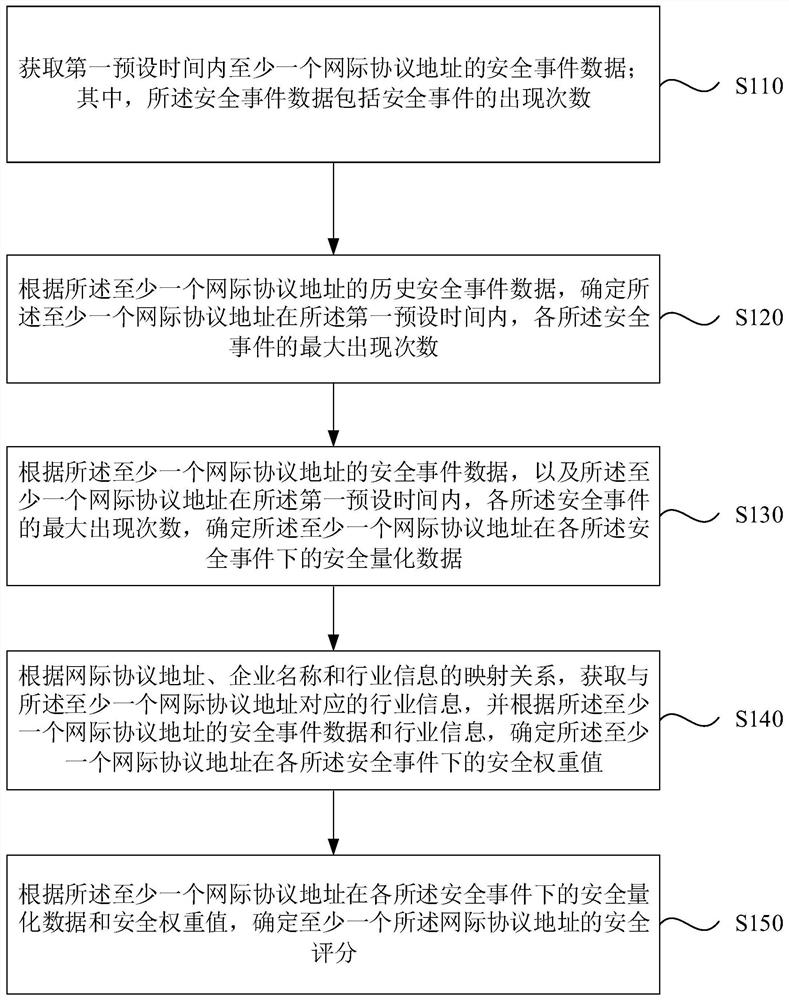
[0031] figure 1 This is a flowchart of a network security evaluation method provided in the first embodiment of the present invention. This embodiment can be applied to obtain the security score of the corresponding Internet Protocol address to realize the network security evaluation. This method can be implemented by the fifth embodiment of the present invention. The provided network security evaluation device is implemented, the device can be implemented by software and / or hardware, and integrated on the electronic device, and the method specifically includes the following steps:
[0032] S110. Acquire security event data of at least one Internet Protocol address within a first preset time; wherein, the security event data includes the number of occurrences of security events.
[0033] The first preset time is a set time period for obtaining the corresponding security event data for the Internet Protocol addresses that need to be evaluated for security, for example, one day,...
Embodiment 2
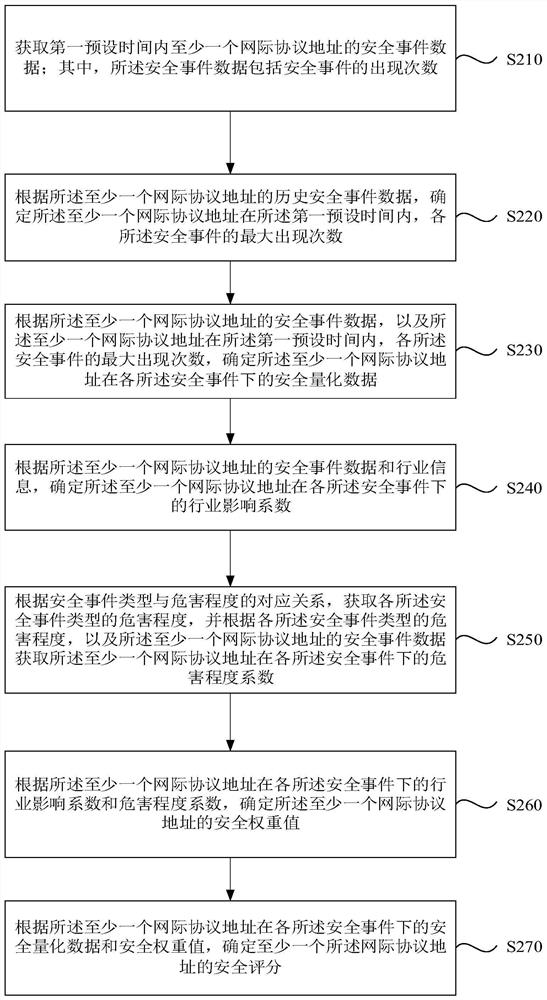
[0048] figure 2 It is a flowchart of another network security evaluation method provided by the second embodiment of the present invention. This embodiment is embodied on the basis of the above-mentioned embodiment. In this embodiment, according to the Internet protocol address under each security event The industry influence coefficient and the hazard degree coefficient are used to determine the security weight value of the Internet Protocol address. The method specifically includes:
[0049] S210. Acquire security event data of at least one Internet Protocol address within a first preset time; wherein, the security event data includes the number of occurrences of security events.
[0050] S220. Determine, according to the historical security event data of the at least one internet protocol address, the maximum number of occurrences of each security event of the at least one internet protocol address within the first preset time.
[0051] S230. Determine the at least one Inte...
Embodiment 3
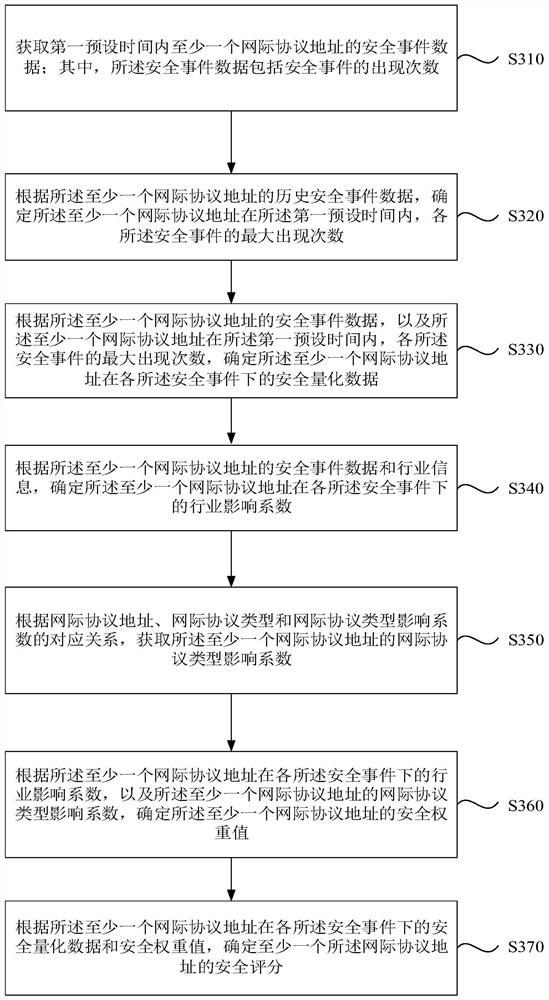
[0061] image 3 It is a flowchart of another network security evaluation method provided in Embodiment 3 of the present invention. This embodiment is embodied on the basis of Embodiment 1. In this embodiment, according to the Internet Protocol address under each security event The industry influence coefficient and the IP type influence coefficient of the IP address are used to determine the security weight value of the IP address, and the method specifically includes:
[0062] S310. Acquire security event data of at least one Internet Protocol address within a first preset time; wherein, the security event data includes the number of occurrences of security events.
[0063] S320. Determine, according to the historical security event data of the at least one internet protocol address, the maximum number of occurrences of each security event of the at least one internet protocol address within the first preset time.
[0064] S330. Determine the at least one Internet Protocol a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com