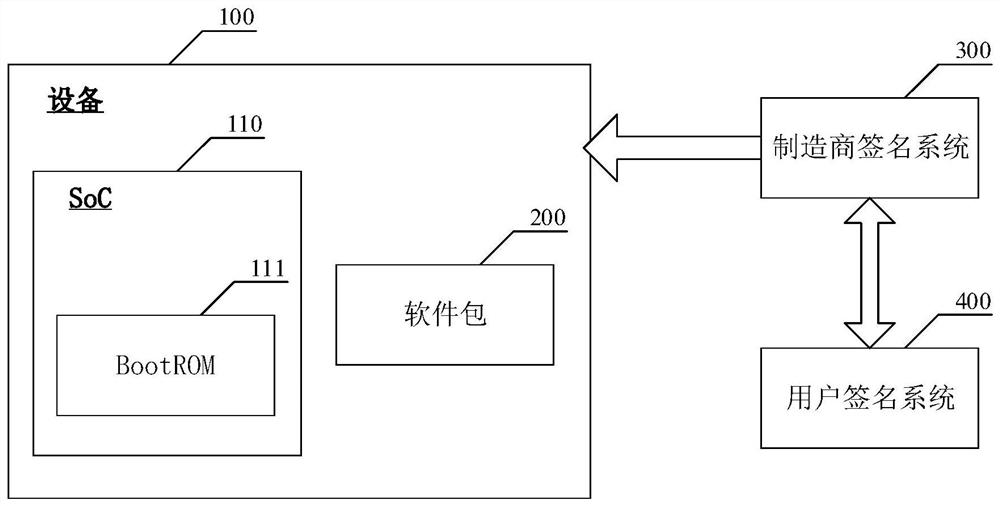
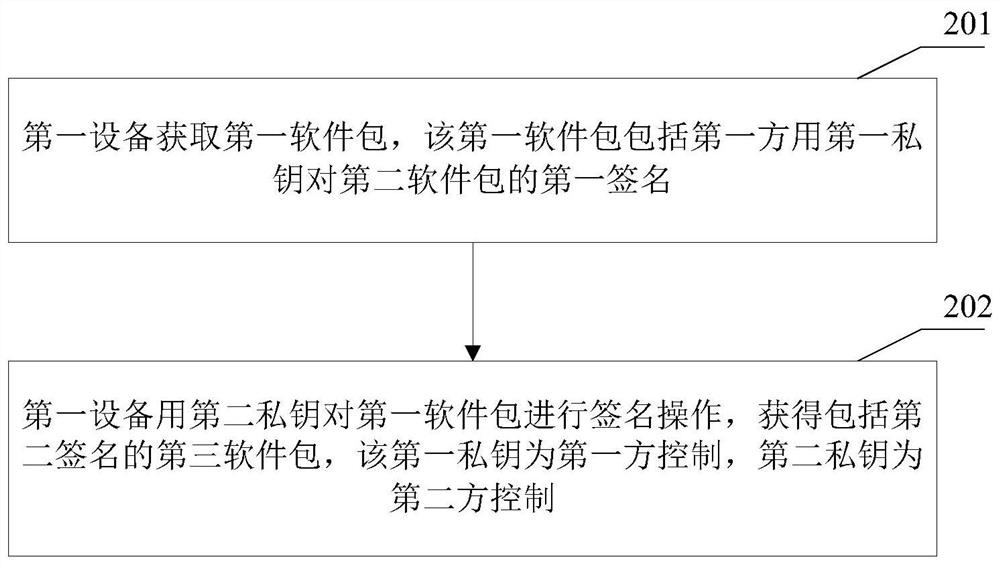
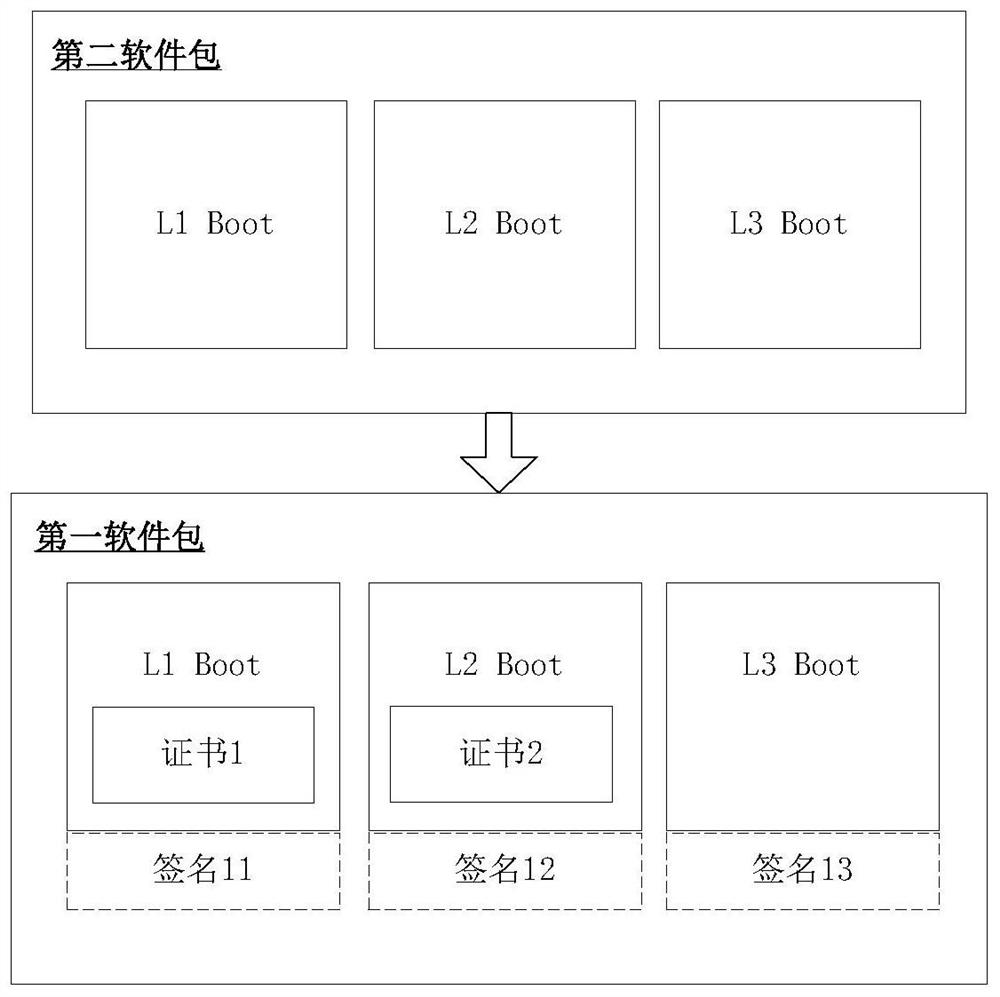
Software integrity protection and verification method and device
A technology for integrity protection and integrity verification, applied in platform integrity maintenance, software deployment, secure communication devices, etc., and can solve problems such as inability to solve user trust issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0116]Example 1: TakingFigure 7 The scene shown is an example, the second device 700 includes a SoC 710 and a startup package including: L1 Boot 720 and L2 Boot 730. Wherein, the SOC 710 has a BootROM 711, and there is a value of the manufacturer public key 1, the user public key 1, the device identification, the double enable bit, and the switching enable bit; L1Boot 720 includes code segments 1, Manufacturer Certificate 1, User Certificate 1, Manufacturer Signature 1 and User Signature 1; L2 Boot 730 includes code segment 2, manufacturer sign 2 and user signing 2.
[0117]As an example, supposeFigure 7 On the second device 700 shown, the value of the dual enable bit indicates that the double enable bit is valid. The value of the switching enable bit indicates that the switching enable bit is invalid, and the device identifier is included in the dual inspection device list. . If the certificate and code segment in each boot are signed, that is, the manufacturer signature 1 includes a ...
Embodiment 2
[0149]Example 2:Figure 10 The scene shown is an example, the second device 1000 includes SoC 1010 and a startup package including: L1 Boot 1020 and L2 Boot 1030. The SOC 1010 has bootrom1011, and there is a value of summary 1, device identification, dual enable bit, and a value of switching enable bits; L1Boot 1020 includes code segment 1, a manufacturer certificate 1, and user certificate 1; L2 Boot 1030 includes code segment 2, manufacturer sign 2 and user signature 2.
[0150]When implementing,Figure 10 On the second device 1000 shown, the value of the double enable bit indicates that the double enable bit is valid. The value of the switching enable bit indicates that the switching enable bit is invalid, and the device identity is included in the list of dual inspection devices. . If the certificate and code segment in each boot is a unified signature, that is, the verification result of the manufacturer sign 2 can be characterized by the legality of the Code Segment 2 and the Manuf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com