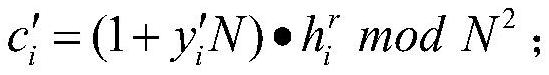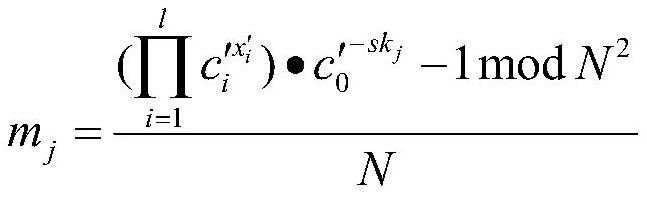File encryption method
A file encryption and file technology, applied in the field of information security, can solve the problems of low efficiency of key selection and file encryption, and achieve the effect of ensuring file encryption security, improving file encryption efficiency, and high security requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
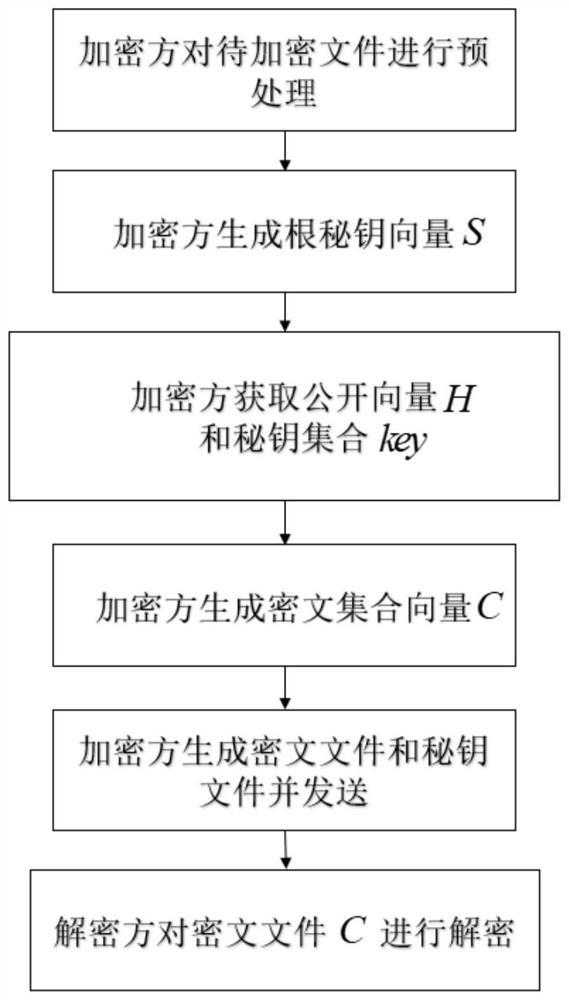
[0031]The present invention will be further described below with reference to the accompanying drawings and specific embodiments:
[0032]Referfigure 1The present invention includes the following steps:
[0033]Step 1) The encryption party is pre-processed to the encrypted file F:
[0034]The encryption party will be evenly divided into J file fragments to be encrypted files to be encrypted. The length of each file fragment is 8 bytes in this instance, and the file segment collection f '= {f1, f2, ..., fj, ..., fJ} And Fragment f for each filejThe character transcoding, the common encoding method has Unicode encoding, UTF-8 encoding, base64 encoding, since Base64 encoding is simple to encrypt data compared to the first two way, this embodiment is encoded in this embodiment, obtained Place set m = {m1, M2, ..., Mj, ..., MJ}, Where fjRepresents the jth file fragment, MjFlyjCorresponding places.
[0035]For file encryption, in order to ensure security, it is usually necessary to segment the file f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com