Encryption and decryption method of deep learning model
A technology of deep learning and encryption methods, which is applied in the field of encryption and decryption of deep learning models, can solve problems such as lack of protection of assets, and achieve the effect of ensuring encryption security and preventing random theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
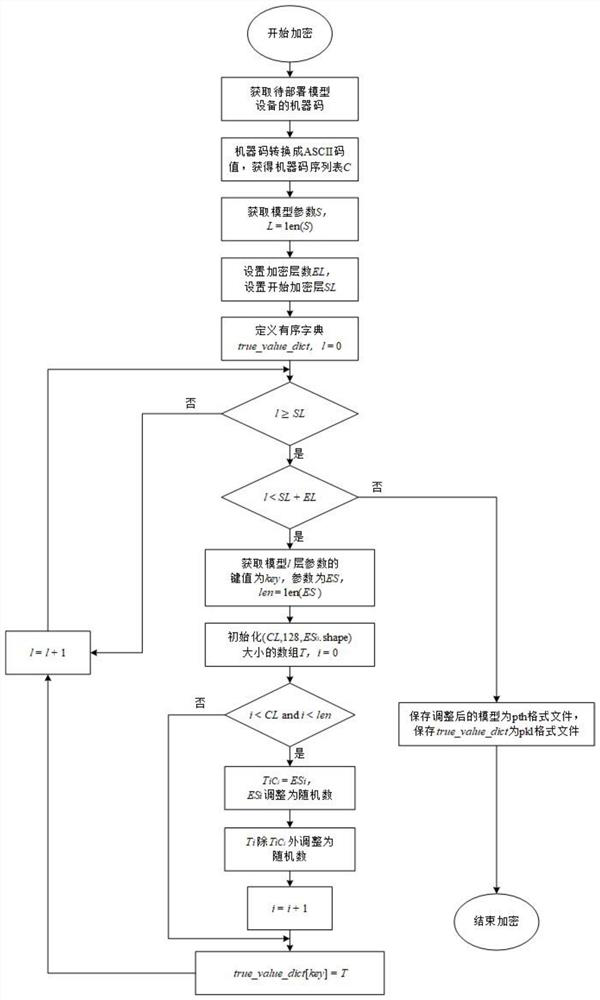
[0044] Embodiment 1: an encryption and decryption method for a deep learning model, the decryption module is divided into the following steps:
[0045] Step 1: Obtain the local machine code, and generate the corresponding ASCII code value sequence list;
[0046] Step 2: According to the number of encryption layers of the model, start the encryption layer, the ASCII code value and the pkl format file storing the real parameters of the model, and decrypt the pth format model file.
[0047] In the present invention, preferably, in step 1, the machine code is a unique identification code representing a computer device, which is composed of a series of letters, numbers and symbols. Therefore, first obtain the machine code of the model device to be deployed to facilitate subsequent encryption operations.
[0048] In the present invention, preferably, in step 2, the machine code is composed of letters, numbers and symbols. In order to facilitate the calculation, the corresponding ch...
Embodiment 2
[0056] Embodiment 2: a kind of encryption and decryption method of deep learning model, the decryption module is divided into the following steps:
[0057] Step 1: Obtain the local machine code, and generate the corresponding ASCII code value sequence list;
[0058] Step 2: According to the number of encryption layers of the model, start the encryption layer, the ASCII code value and the pkl format file storing the real parameters of the model, and decrypt the pth format model file.
[0059] In the present invention, preferably, in step 1, the machine code of the device is obtained, and each character of the machine code is converted into an ASCII code value, thereby obtaining a machine code sequence table.
[0060] In the present invention, preferably, in step 2, for the SL to SL+EL-piece layer parameters of the model file, cycle the machine code sequence table C, and according to the ASCII code value C in the list i Replace the encrypted value of the ith parameter of this l...
Embodiment 3
[0062] Embodiment 3: a kind of encryption and decryption method of deep learning model, the decryption module is divided into the following steps:
[0063] Step 1: Obtain the local machine code, and generate the corresponding ASCII code value sequence list;
[0064] Step 2: According to the number of encryption layers of the model, start the encryption layer, the ASCII code value and the pkl format file storing the real parameters of the model, and decrypt the pth format model file.
[0065] In the present invention, preferably, in step 1, the machine code is a unique identification code representing a computer device, which is composed of a series of letters, numbers and symbols. Therefore, first obtain the machine code of the model device to be deployed to facilitate subsequent encryption operations.
[0066] In the present invention, preferably, in step 2, the machine code is composed of letters, numbers and symbols. In order to facilitate the calculation, the correspondin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com