Internet-of-Things dynamic NTRU access authentication method based on time information
A technology of time information and access authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The present invention will be further described below in conjunction with the accompanying drawings. However, it should be noted that these implementations are not limitations to the present invention, and the functions, methods, or structural equivalent transformations or substitutions made by those skilled in the art based on these implementations are all included in the protection scope of the present invention. .
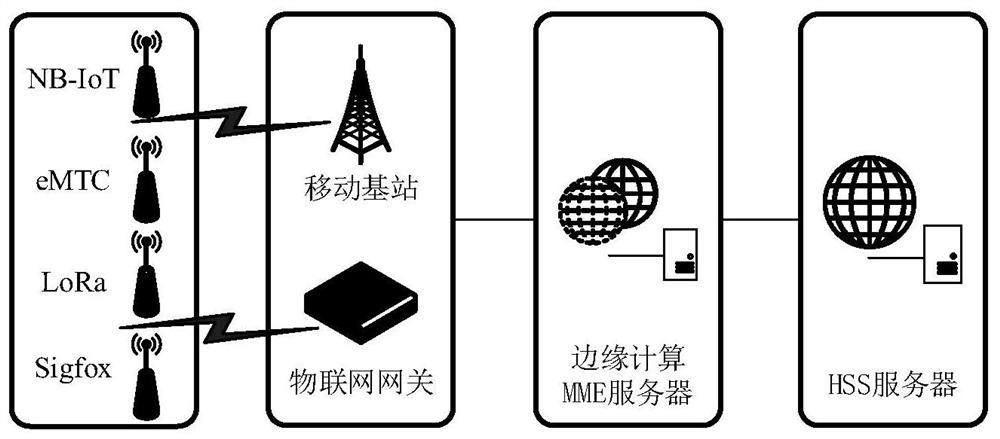
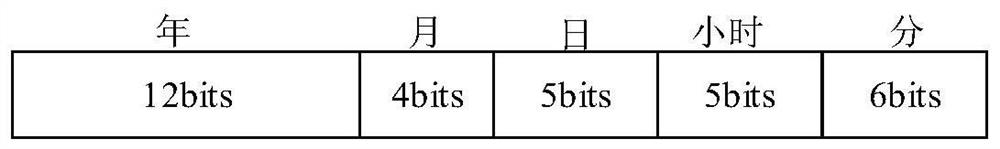
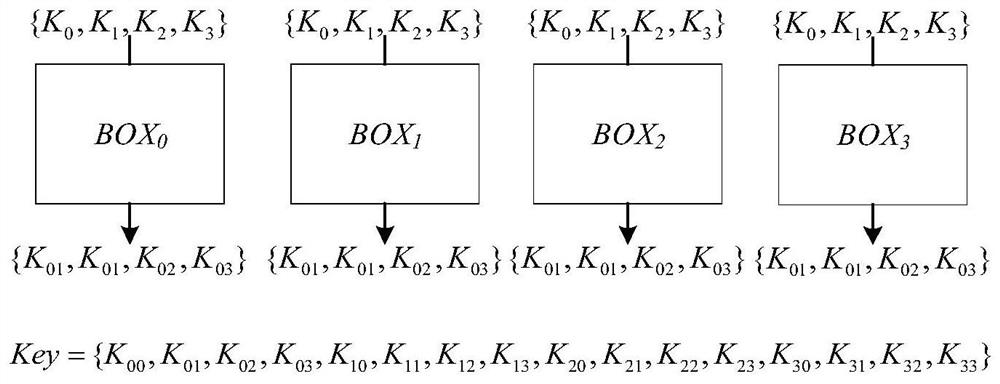
[0069] figure 1 It is the power Internet of things network terminal equipment D i The specific process of secure access. The power Internet of Things is a large-scale industrial Internet of Things, and its architecture includes three typical network structures: the Internet of Things perception extension layer, network transmission layer and platform application layer. NB-IoT and eMTC devices are connected to mobile base stations, and LoRa and Sigfox devices are connected to edge computing MME servers with edge computing functions through dedicated IoT...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com