User behavior sequence anomaly detection method, terminal and storage medium
An anomaly detection and user technology, applied in the field of data processing, can solve problems such as inability to identify abnormal behaviors, data and information security cannot be guaranteed, and achieve the effect of overcoming many pain points, clear steps, and high scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
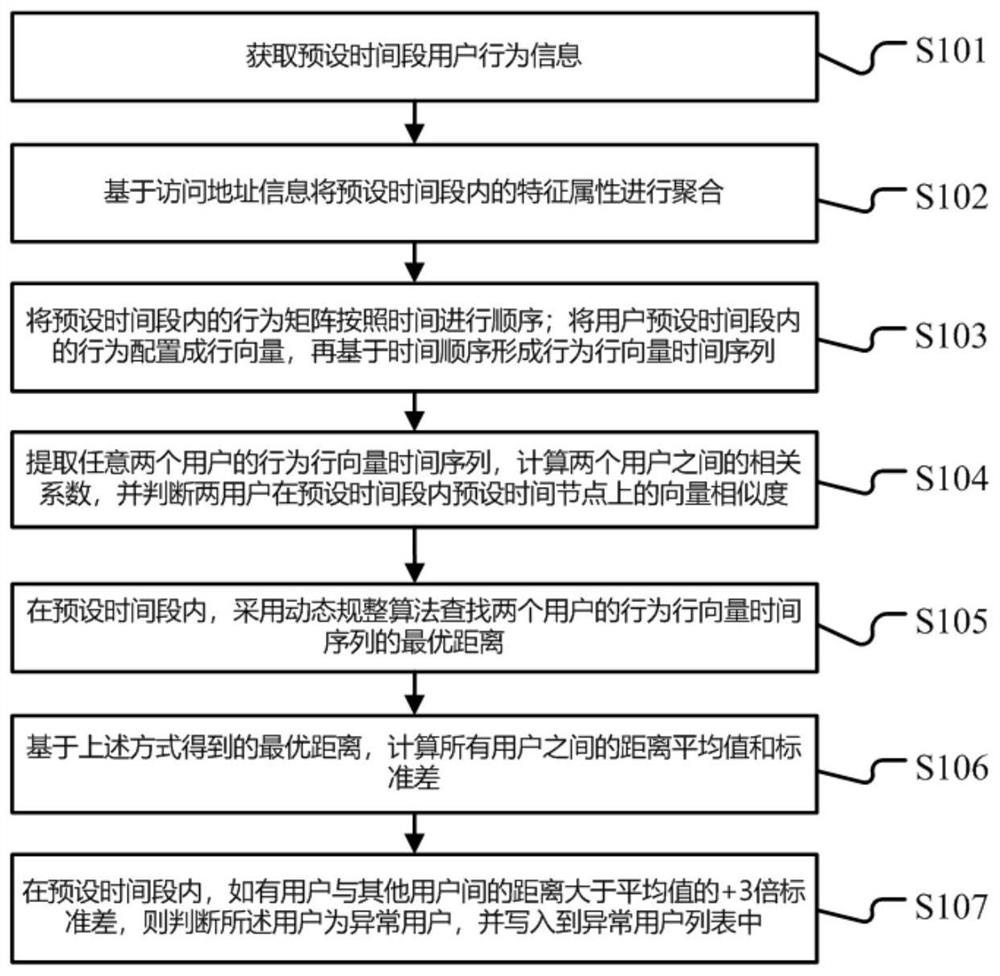
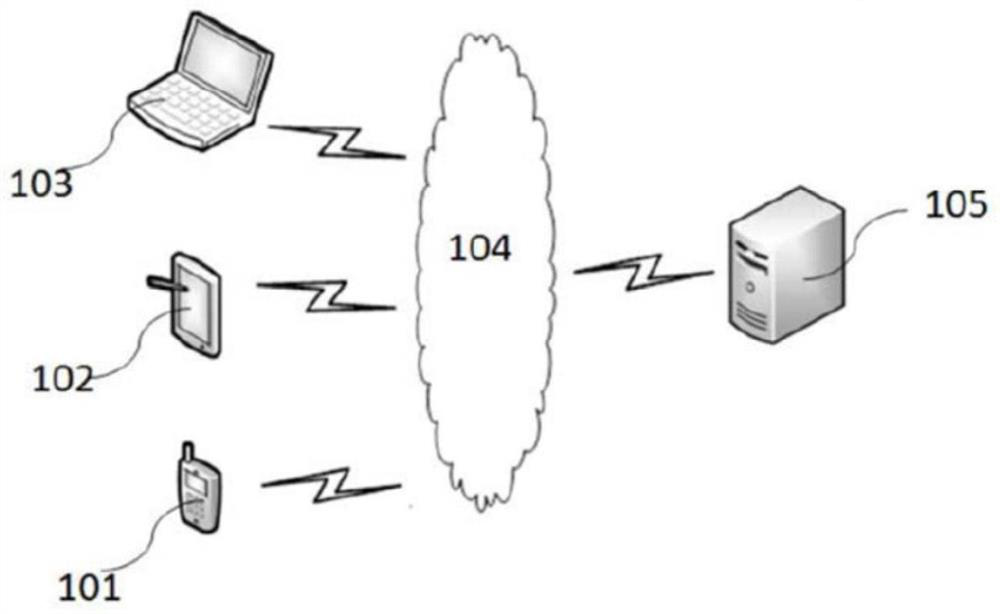
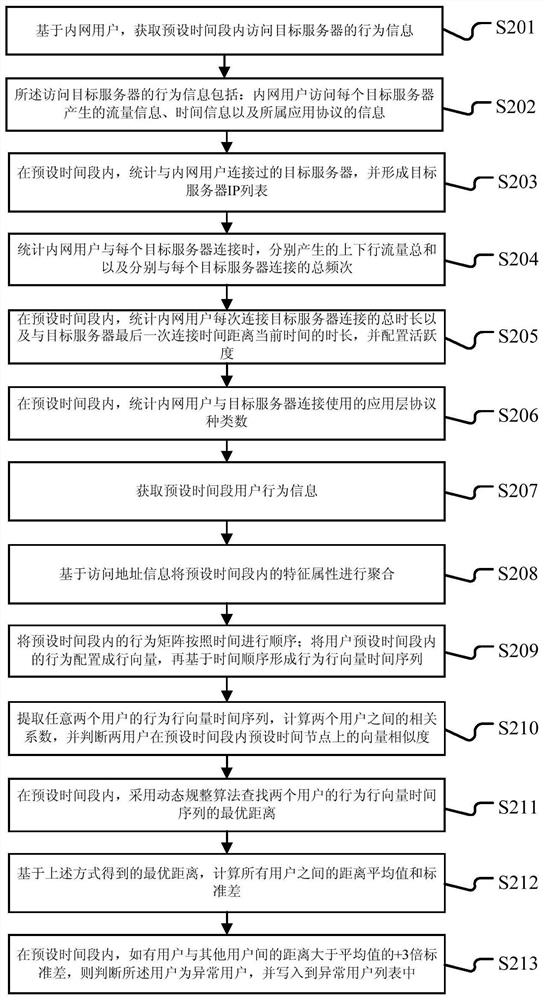
[0085] The present invention also provides an implementation mode. The method steps of the implementation mode can be executed by a terminal device, or by a server end, or by an interactive execution between a terminal device and a server end. For example, the above-mentioned figure 2 The server 105 in is executed, but the present disclosure is not limited thereto.
[0086] Get user behavior feature matrix
[0087] For the intranet user, obtain the behavior information of accessing the target server within a preset time period, the behavior information of accessing the target server includes the traffic information generated by the intranet user's access to each target server, time information, and the application protocol to which it belongs. information.
[0088] Based on the behavior information of the access target server, count the IP list of the target server that the intranet user has connected to within the preset time period, the sum of the uplink and downlink traff...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com