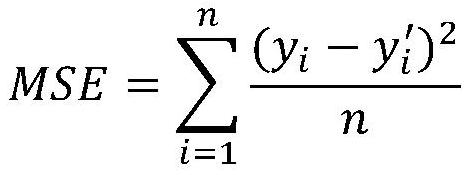Data security deduplication method based on auto-encoder
A self-encoder, data security technology, applied in the direction of digital data protection, electrical digital data processing, computer security devices, etc., can solve the problem of low efficiency, reduce the number of times, improve the efficiency of deduplication, and improve the efficiency of label comparison.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
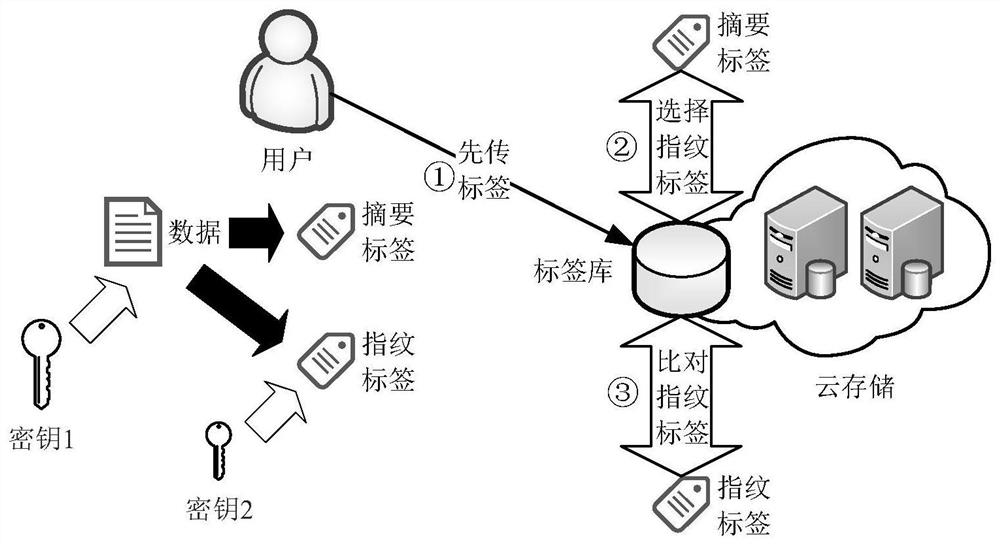
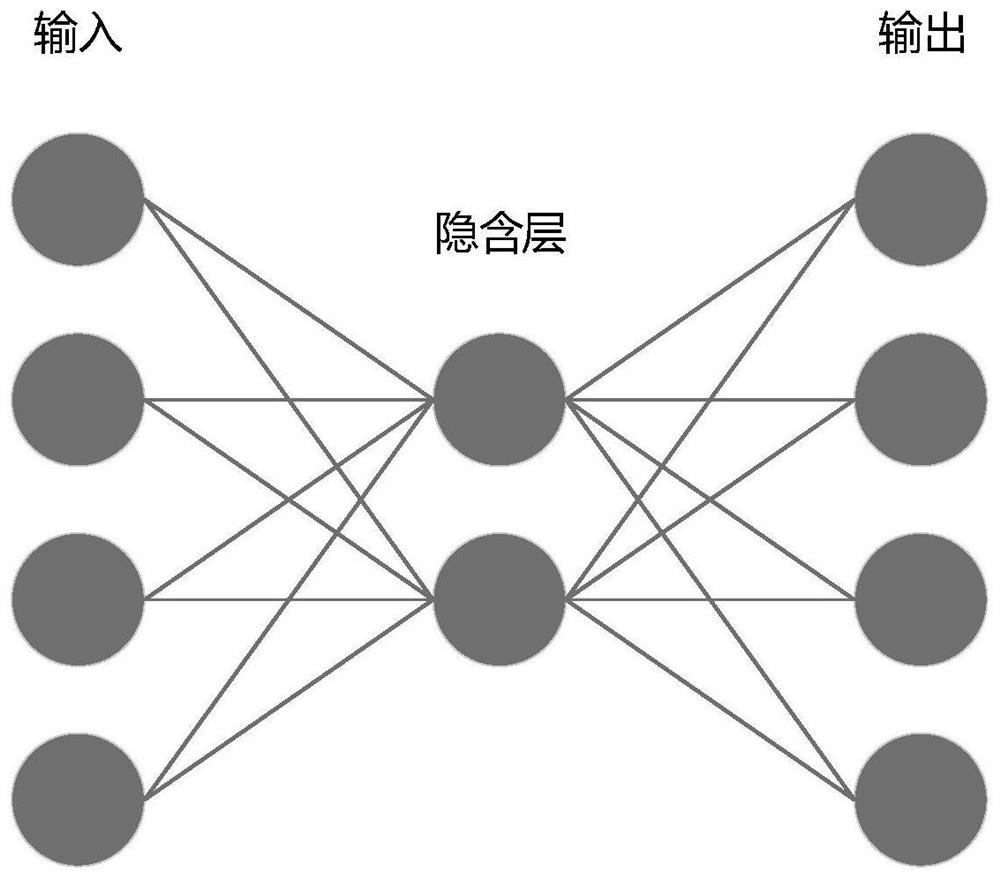
[0021]CombineFigure 1 to Figure 2In this embodiment, a method for data security deduplication based on a self-encoder is used to generate a summary label of the data through a self-encoding technology. The original label generated by random message lock encryption is still retained, which is called a fingerprint label. In order to ensure data confidentiality, one key is used to encrypt data, and another key is used to encrypt fingerprint tags. Among them, the same data must be encrypted with the same key to realize the sharing of data among different users; while the fingerprint tag of the same data does not need to be encrypted with the same key, because it is not necessary to compare the fingerprint tag. Decrypt. Since the autoencoder model is similar, that is, the feature distance between similar data is much smaller than that of different data, so the summary tags generated by this model can filter out a set of fingerprint tag sets similar to user data, thereby greatly reducing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com