Terminal data isolation method and device for one-end multi-network environment
A technology of data isolation and environment, applied in program control devices, electrical digital data processing, instruments, etc., can solve the problems of waste of resources and low user convenience, and achieve the effect of ensuring safety, saving costs and office space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
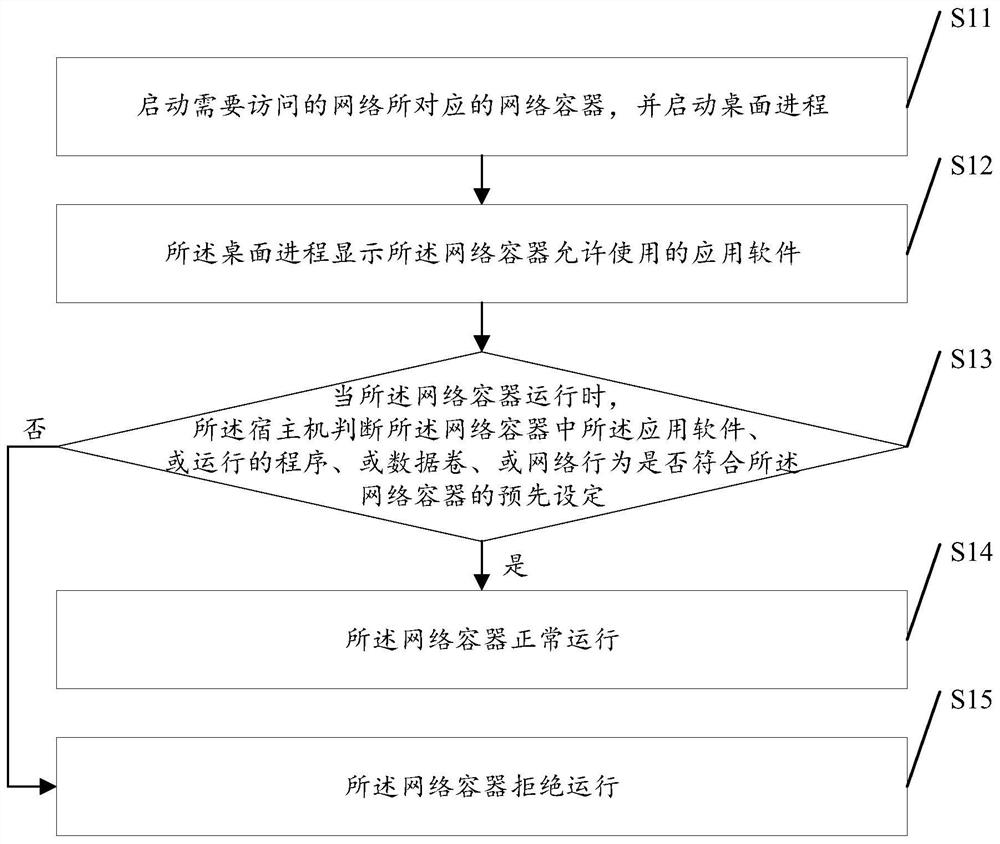
[0030] see figure 1 , figure 1 It is a schematic flowchart of a method for isolating terminal data in a one-end multi-network environment in an embodiment of the present invention.
[0031] Such as figure 1 As shown, a terminal data isolation method in a multi-network environment at one end, log in to the host machine with administrator privileges to operate, make an application image according to the office needs of the unit, and push it to the application store, and set the image to allow the network container Running in, wherein, said method comprises:
[0032] S11: Start the network container corresponding to the network to be accessed, and start the desktop process;
[0033] In the specific implementation process of the present invention, the starting of the network container corresponding to the network to be accessed includes: initializing the LXC environment, building an isolated runtime environment, and loading the data volume corresponding to the network container...
Embodiment 2
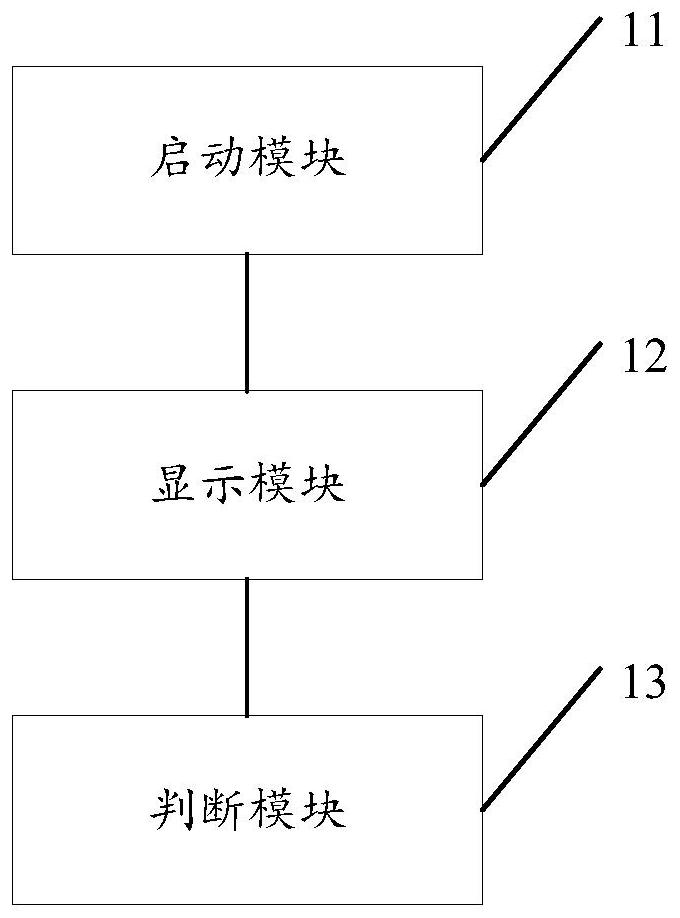
[0056] see figure 2 , figure 2 It is a schematic diagram of the structure and composition of a terminal data isolation device in a one-end multi-network environment in an embodiment of the present invention.
[0057] Such as figure 2 As shown, a terminal data isolation device in a one-end multi-network environment, the device includes:
[0058] Startup module 11: used to start the network container corresponding to the network that needs to be accessed, and start the desktop process;
[0059] Display module 12: used for the desktop process to display the application software allowed to be used by the network container;
[0060] Judgment module 13: for when the network container is running, the host computer judges whether the application software, or running program, or data volume, or network behavior in the network container conforms to the preset configuration of the network container Certainly.
[0061] Specifically, for the working principle of the device-related ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com