Multi-keyword searchable encryption method and system supporting Boolean access control strategy
An access control strategy and multi-keyword technology, applied in the fields of information retrieval and cryptography, can solve problems that cannot be solved at the same time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
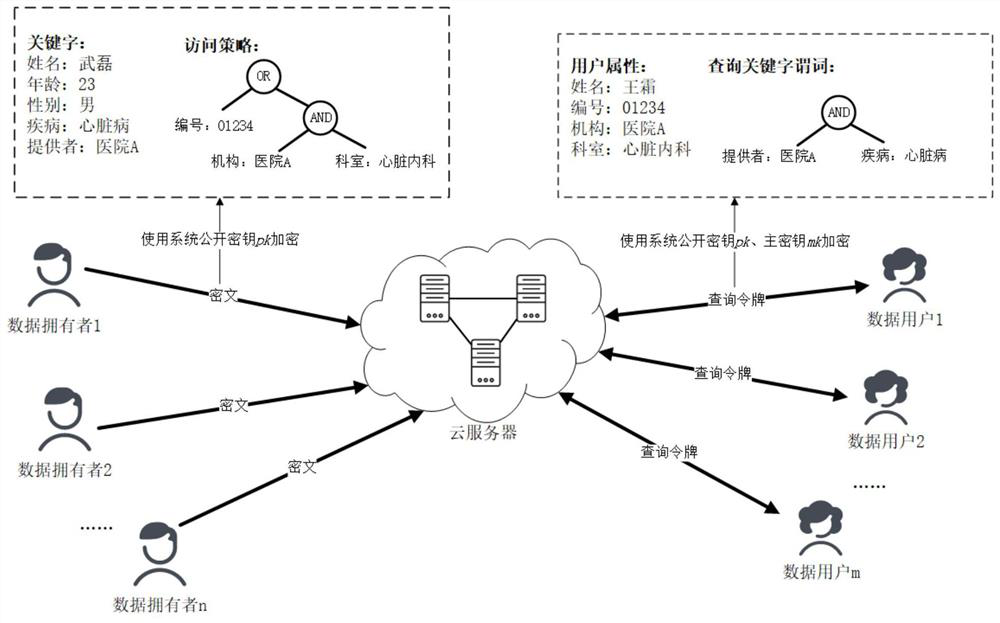
[0079] This embodiment discloses a multi-keyword searchable encryption method that supports Boolean access control policies. In the context of cloud storage, this embodiment is based on searchable encryption technology and attribute encryption technology, and uses LSSS to represent access policies and search policies. It can support Boolean keyword search, and can effectively locate the data that users are interested in; at the same time, it can realize the flexibility and concealment of access policies, support fine-grained Boolean access control; and support constant-level system key length. Such as figure 1 As shown, the method is applied to an application system including a trusted authority, a data client, a data owner, and a cloud server, such as a healthcare system and a school educational administration system. The method steps are as follows:
[0080] S1. The trusted authority TA generates the system public key pk, master key mk and ElGamal private key a′, and publish...
Embodiment 2
[0125] This embodiment discloses a multi-keyword searchable encryption system that supports Boolean access control policies, such as figure 2 As shown, it includes: the initialization and token generation subsystem running on the trusted authority TA, the encryption subsystem running on the data owner side, the cloud storage subsystem running on the cloud server, the user retrieval and token running on the data client side decryption subsystem.
[0126] The trusted authority TA is a fully trusted third-party security organization, and the data owner and data client are terminal devices with computing and processing capabilities, including smart phones, tablets, and computers. The system can implement the multi-keyword searchable encryption method described in Embodiment 1 that supports Boolean access control policies.
[0127] Among them, the initialization and token generation subsystem running on the trusted authority TA includes an initialization module, a master key stor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com