A Dynamic Password Realization Method Under Unstable Wireless Signal
A dynamic password and wireless signal technology, applied in wireless communication, electrical components, security devices, etc., can solve problems such as interference, weak base station signal, unstable wireless signal, etc., to achieve effectiveness, prevent malicious manipulation, and improve equipment operation quality effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
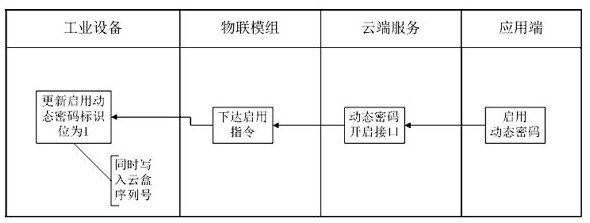
[0055] When the signal is unstable, the cloud will randomize 4 digits and try to download it several times without success; then the password will be generated according to the serial number of the IoT module + a specific algorithm. Here is an example:
[0056] (1) Cloud:
[0057] Step 1: The cloud obtains the serial number from the device controller through the IoT module, such as: 2010010001; (the serial number of the module is a ten-digit ID, and the serial number of each module will be different);
[0058] Step 2: Add the obtained serial number to a fixed 9-digit number, assuming that the fixed 9-digit number is: 123456789; then the serial number 2010010001+123456789= 2133466790; where 123456789 is the agreed value between the cloud and the controller, and this value can be passed through artificial modification;
[0059] Step 3: Take the 5th, 6th, 9th, and 10th digits and spell them into four digits; for example, the 5th digit of 2133466790 is 4, the 6th digit is 6, the ...
Embodiment 2
[0069] When the signal is unstable, the cloud will randomize 4 digits and try to download it several times without success; then the password will be generated according to the serial number of the IoT module + a specific algorithm. Here is an example:
[0070] (1) Cloud:
[0071] Step 1: The cloud obtains the serial number from the device controller through the IoT module, such as: 2010010001; (the serial number of the module is a ten-digit ID, and the serial number of each module will be different);
[0072] Step 2: Add a random 9-digit number to the obtained serial number, assuming that the 9-digit random password is: 123456789, 787645321; then select a set of data from the data each time, such as 123456789; then the password generation method is:
[0073] Serial number 2010010001+123456789= 2133466790;
[0074] Step 3: Take the 5th, 6th, 9th, and 10th digits and spell them into four digits; for example, the 5th digit of 2133466790 is 4, the 6th digit is 6, the 9th digit i...
Embodiment 3
[0084] When the signal is stable, the cloud generation method is as follows:
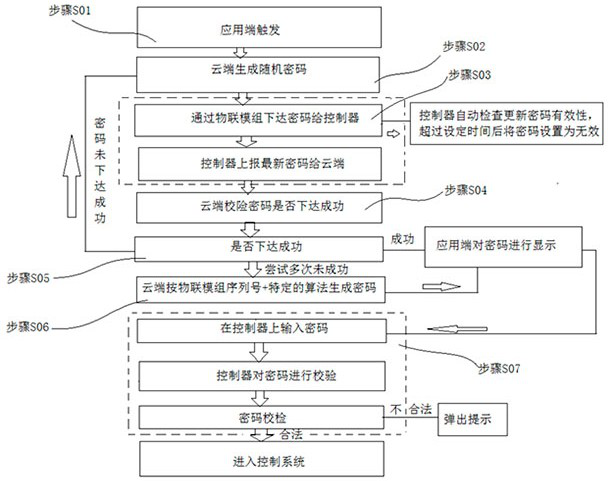
[0085] Step S01, triggering on the application side: when an electromechanical device needs to be operated, the user clicks on the application side to generate a dynamic password, and then calls the cloud data;
[0086] Step S02, the cloud generates a random dynamic password: the cloud generates a random 4-digit password through a password generation algorithm; wherein the dynamic code is a four-digit random number generated by the random method in the Math class of Java;
[0087] Step S03, the cloud issues the password to the IoT module: the cloud issues a 4-digit password to the IoT module through MQTT or HTTP, and the IoT module receives it through a wireless signal; after receiving it, the IoT module then passes the industrial communication Write to the device controller, when the signal is written successfully, the device can be turned on and working;
[0088] From the above, when the signal i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com