Software security detection method, client, system and storage medium
A software security and detection method technology, applied in the computer field, can solve problems such as difficult malicious behaviors, corporate information security threats, lack of protection methods, etc., and achieve the effect of preventing malicious manipulation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Hereinafter, the present application will be described in detail with reference to the drawings and embodiments. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
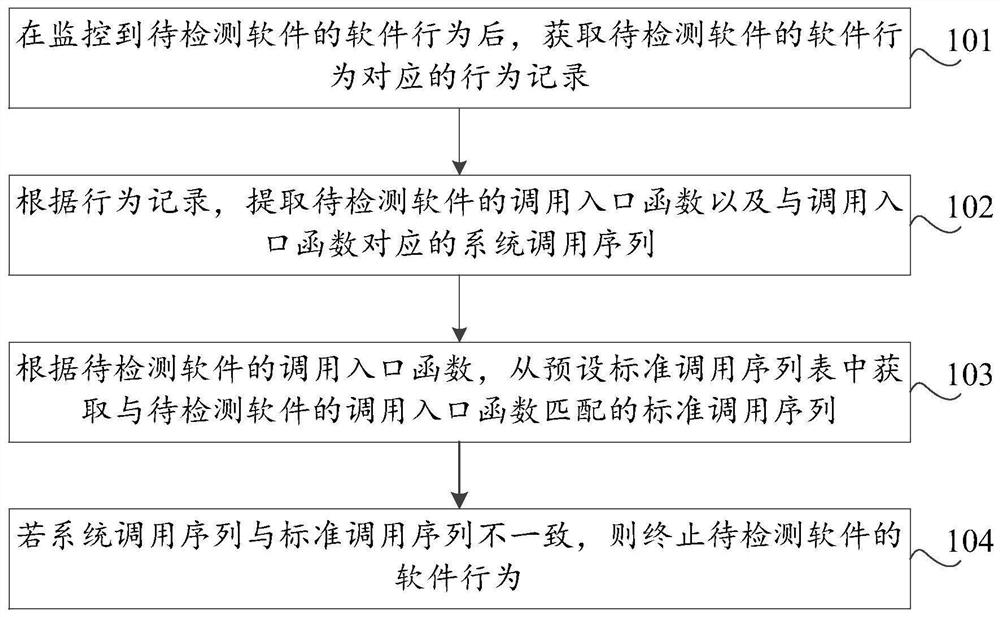
[0030] In this embodiment, a software security detection method is provided, such as figure 1 As shown, the method includes:
[0031] Step 101 , after monitoring the software behavior of the software to be detected, acquiring a behavior record corresponding to the software behavior of the software to be detected.
[0032] In the embodiment of this application, the operating system monitors the software behavior of the software in the system in real time. Specifically, a function call monitoring tool can be used to track and monitor the program of the software to be evaluated, and form a record of each time the program runs. The monitoring log of the behavior records under the monitoring log, s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com