Method for triggering automatic alarm of equipment and equipment thereof
A technology of automatic alarm and equipment, which is applied in the information field to prevent further deterioration of the situation, save the alarm time, and conceal the alarm method.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 Embodiment
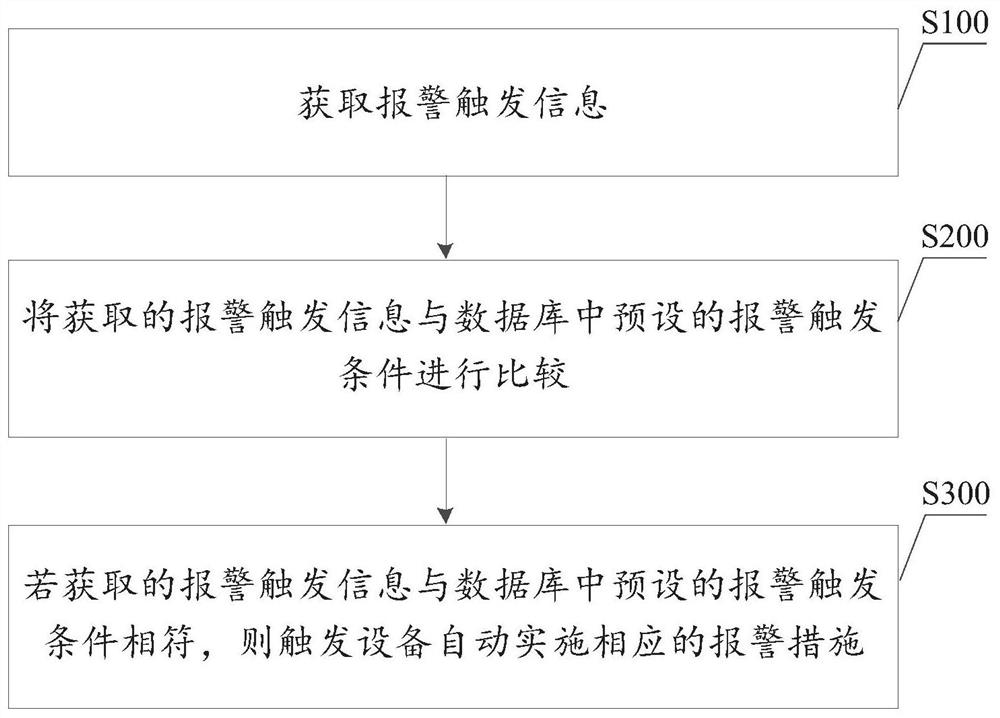
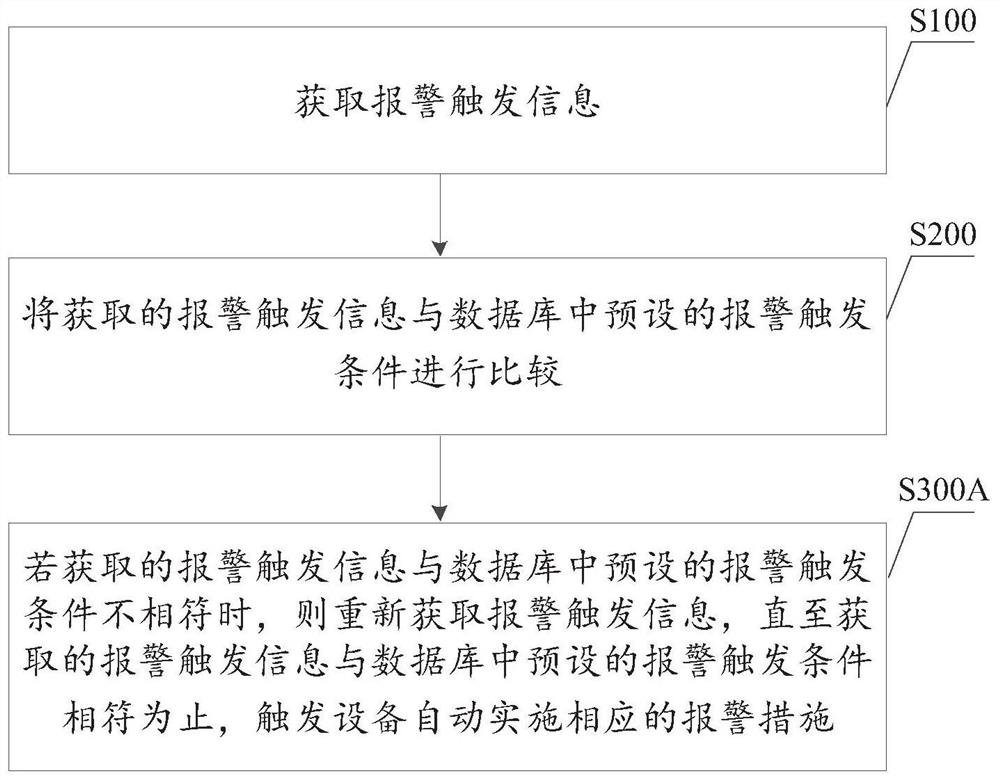
[0058] In this embodiment, the device is a smart mobile terminal, and a database is preset in the smart mobile terminal for storing alarm trigger conditions. A preset voice can be used to trigger an automatic alarm, or a fingerprint can be used to trigger an automatic alarm. For example, the alarm trigger condition is preset as: two fingerprints alternate three times, that is, for the preset fingerprint A and fingerprint B, as long as the mobile smart terminal scans the fingerprint trigger mode as: ABABAB or BABABA, the automatic alarm condition is triggered, and the mobile smart terminal Start to implement relevant measures of automatic alarm.
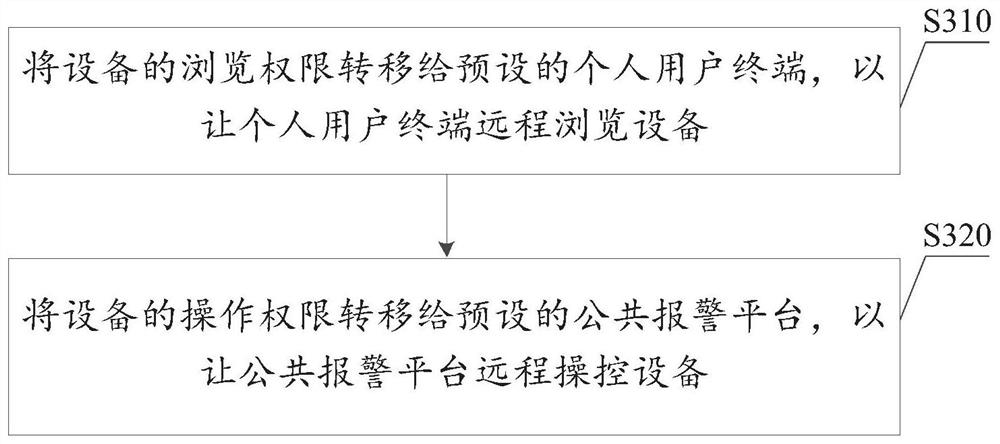
[0059] Collect alarm-related information: In this embodiment, the alarm-related information collected by the mobile smart terminal includes the identity information (name, gender, ID card number or ID card picture or electronic ID card) of the individual user terminal, the mobile smart terminal number, the nearest 5 phone contacts, t...
no. 2 Embodiment
[0064] In this embodiment, the device shown is a smart watch. A database is preset in the smart watch to store alarm trigger conditions. In this embodiment, the time information, location information and moving speed information of the smart watch are used as the basis for triggering the alarm. As shown in Table 1, the corresponding relationship between the time information and the location information is preset in the database, and the maximum moving speed is set at the same time. When the time information, location information and moving speed information scanned by the smart watch meet the preset rules, an automatic alarm is triggered.
[0065] For example, the following rules can be preset: when the time information and location information do not match, and the actual speed scanned exceeds the maximum speed, and the duration exceeds 3 minutes, it is defined as a suspicious state; when the suspicious state lasts for more than 10 minutes, defined as dangerous.
[0066] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com