Video tampering detection method and system, storage medium, computer program and terminal
A technology of tampering detection and video, which is applied in the field of information security, can solve the problems of inability to detect surveillance video forgery, difficulty in video processing, and low algorithm efficiency, and achieve the effect of solving the problem of video tampering detection and solving time and space tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
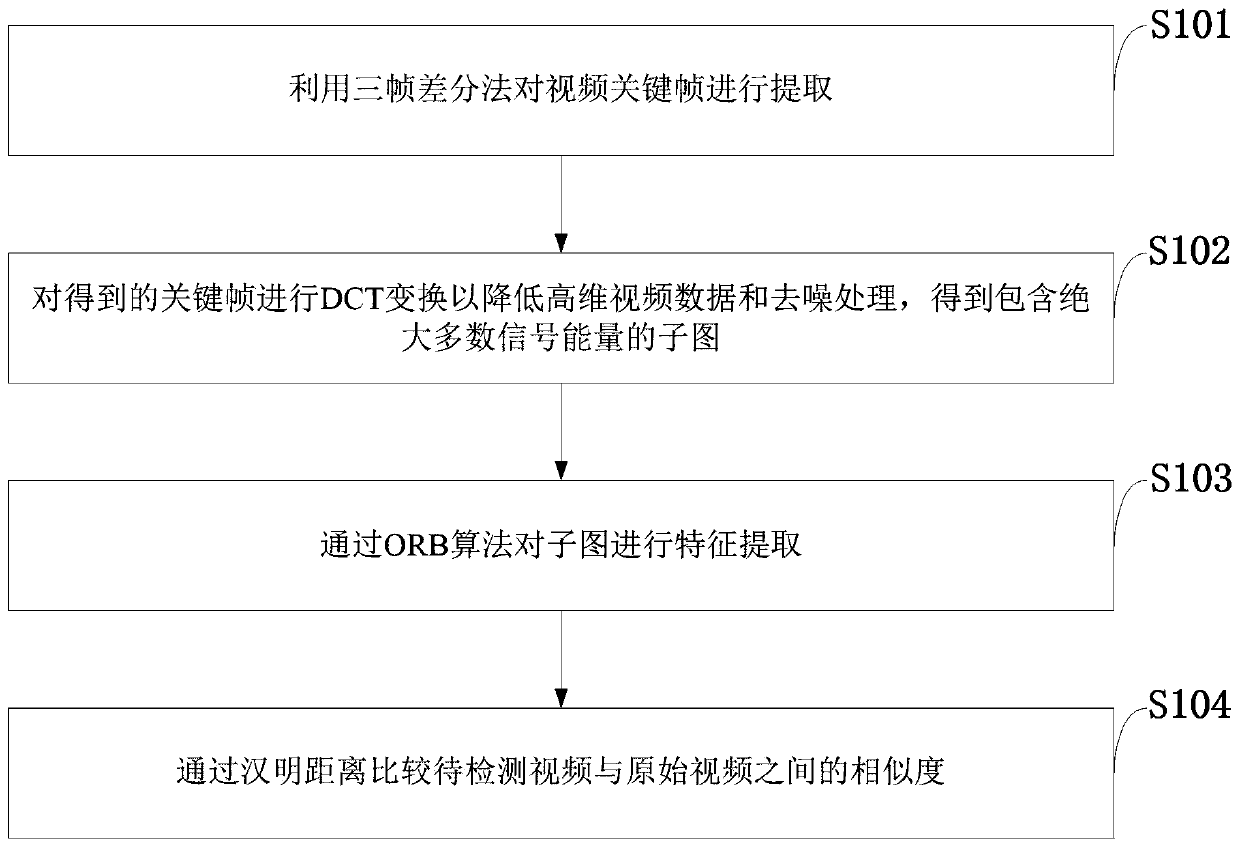
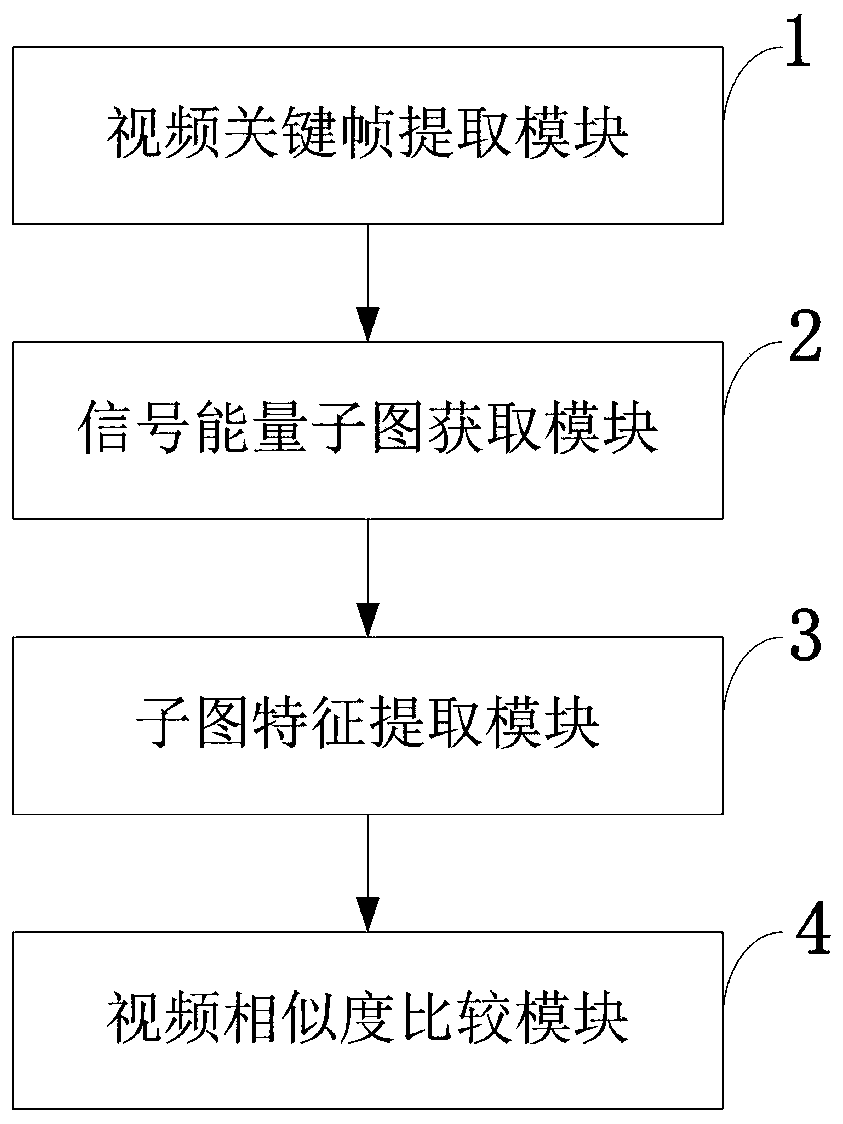
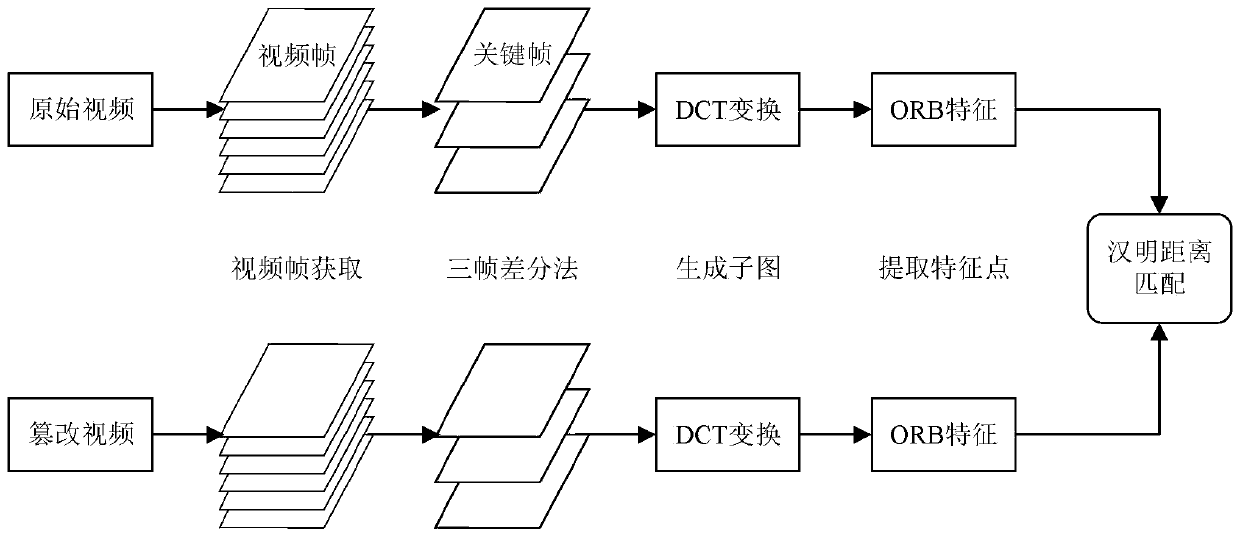
[0063] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
[0064] DCT: Discrete Cosine Transform.
[0065] SIFT: Scale Invariant Feature Transform (Scale Invariant Feature Transform,).
[0066] BRIEF: Binary Robust Independent ElementaryFeatures.
[0067] rBRIEF: Rotation-aware BRIEF algorithm (rotation-aware BRIEF).
[0068] FAST: Feature point algorithm for accelerated segment test (features from accelerated segment test).
[0069] oFAST: Fast Fast algorithm (Oriented FAST).
[0070] ORB (Oriented FAST and Rotation Brief).
[0071] DCT Discrete Cosine Transform discrete cosine transform.
[0072] kNN k-NearestNeighbor k nearest neighbor classification algorithm.
[0073] O...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com