Processor verification method and device, electronic equipment and storage medium
A processor and technology to be verified, applied in the computer field, can solve problems such as missing scenarios, low efficiency, and inability to verify, and achieve the effect of ensuring correctness and integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
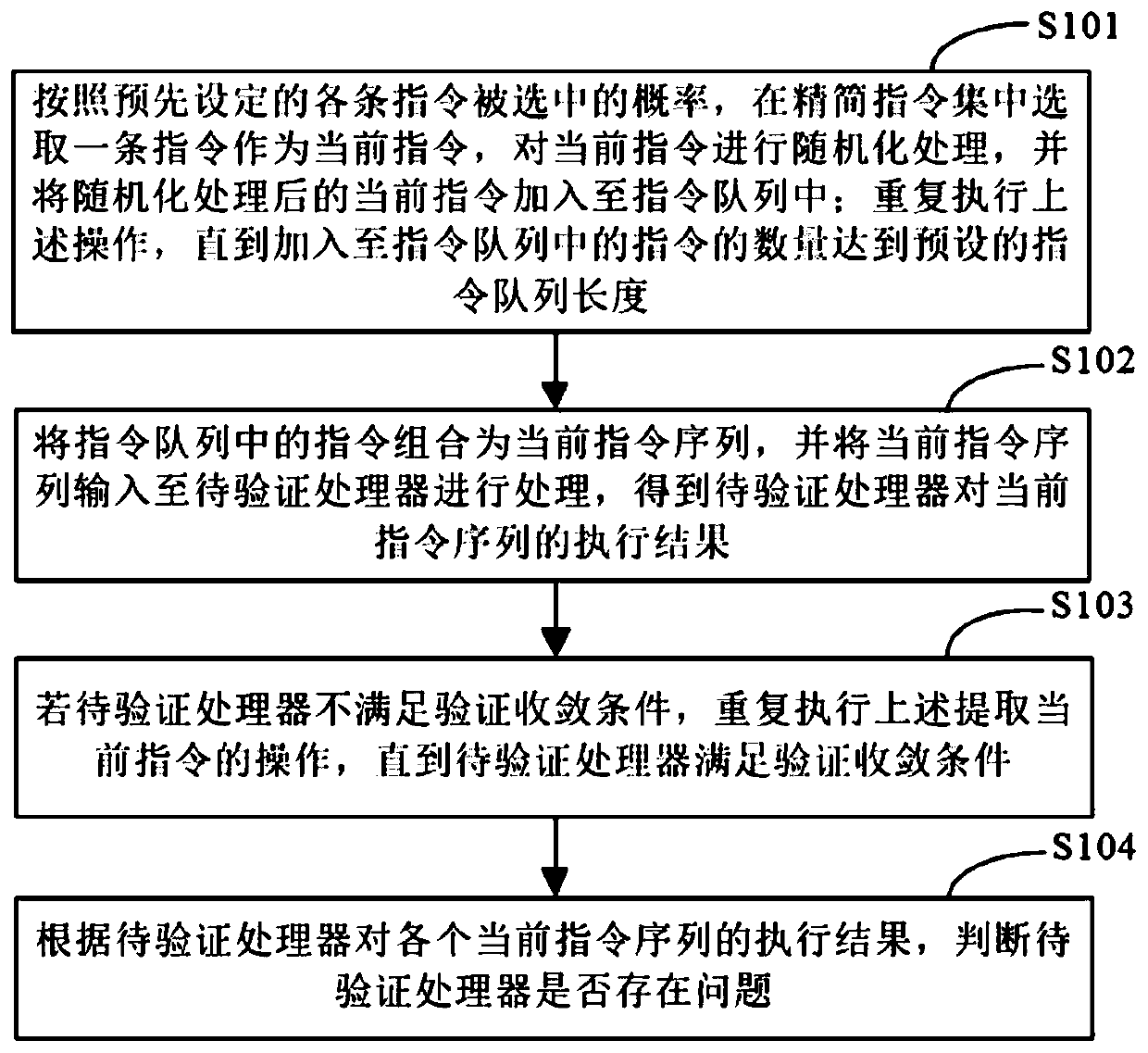
[0032] figure 1 It is a schematic flowchart of a method for verifying a processor provided in Embodiment 1 of the present application. The method can be executed by a device for verifying a processor, an electronic device, or a random instruction generation platform. The device, electronic device, or random instruction generation platform can be implemented by a software and / or hardware, the device or electronic device can be integrated into any smart device with network communication function. Such as figure 1 As shown, the method for authenticating a processor may include the following steps:
[0033] S101. According to the preset probability of each instruction being selected, select an instruction in the reduced instruction set as the current instruction, perform randomization processing on the current instruction, and add the randomized current instruction to the instruction queue; repeat The above operations are performed until the number of instructions added to the i...
Embodiment 2
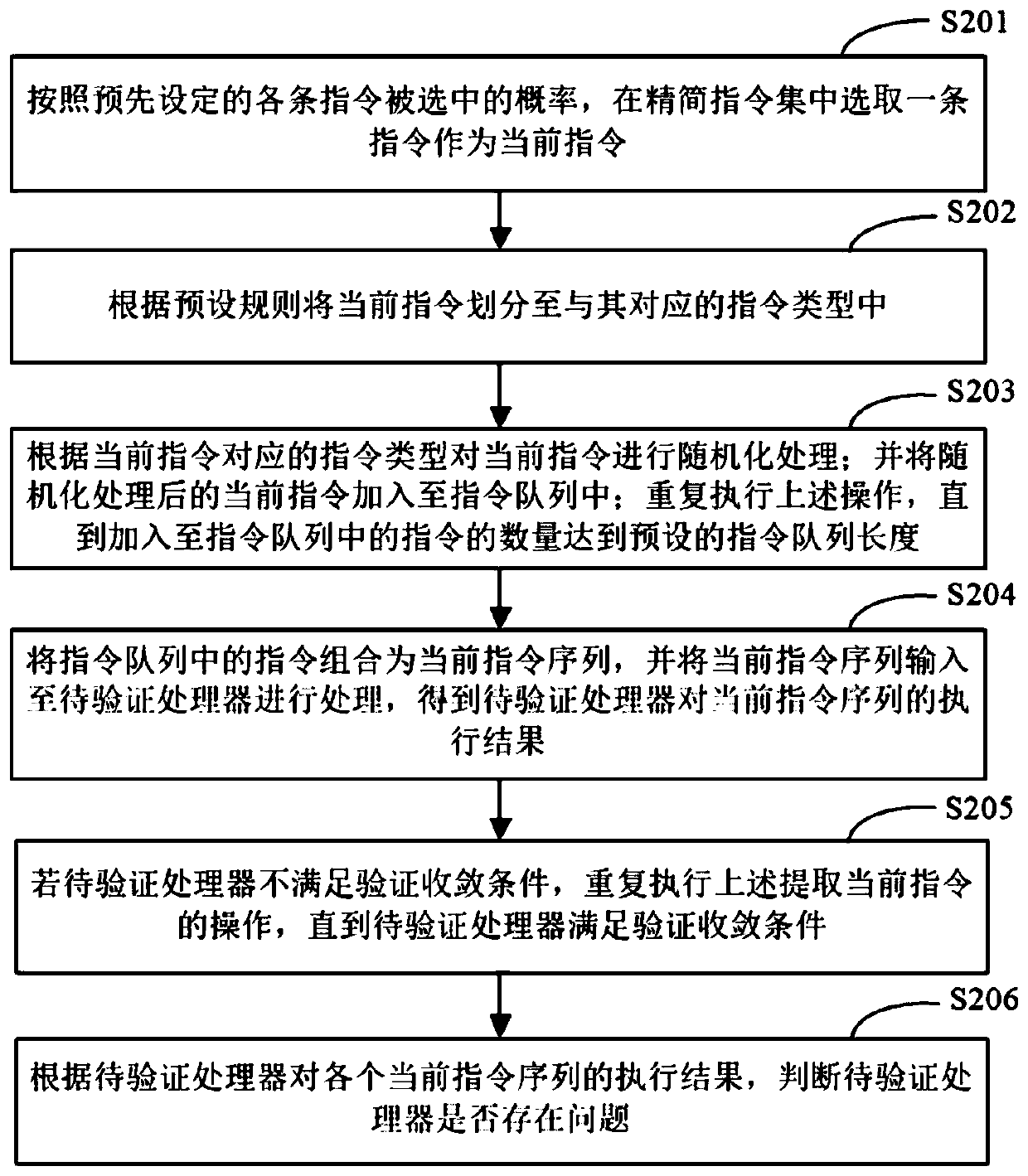
[0045] figure 2 It is a schematic flowchart of the method for verifying a processor provided in Embodiment 2 of the present application. Such as figure 2 As shown, the method for authenticating a processor may include the following steps:
[0046] S201. Select an instruction from the reduced instruction set as the current instruction according to the preset probability of each instruction being selected.
[0047] In a specific embodiment of the present application, the electronic device may select an instruction in the reduced instruction set as the current instruction according to a preset probability of each instruction being selected. Specifically, when selecting the current instruction for the first time, the electronic device can pre-set the probability of each instruction being selected as the same probability value. Therefore, when the electronic device selects the current instruction for the first time, it can follow the The probability of an instruction being sel...
Embodiment 3
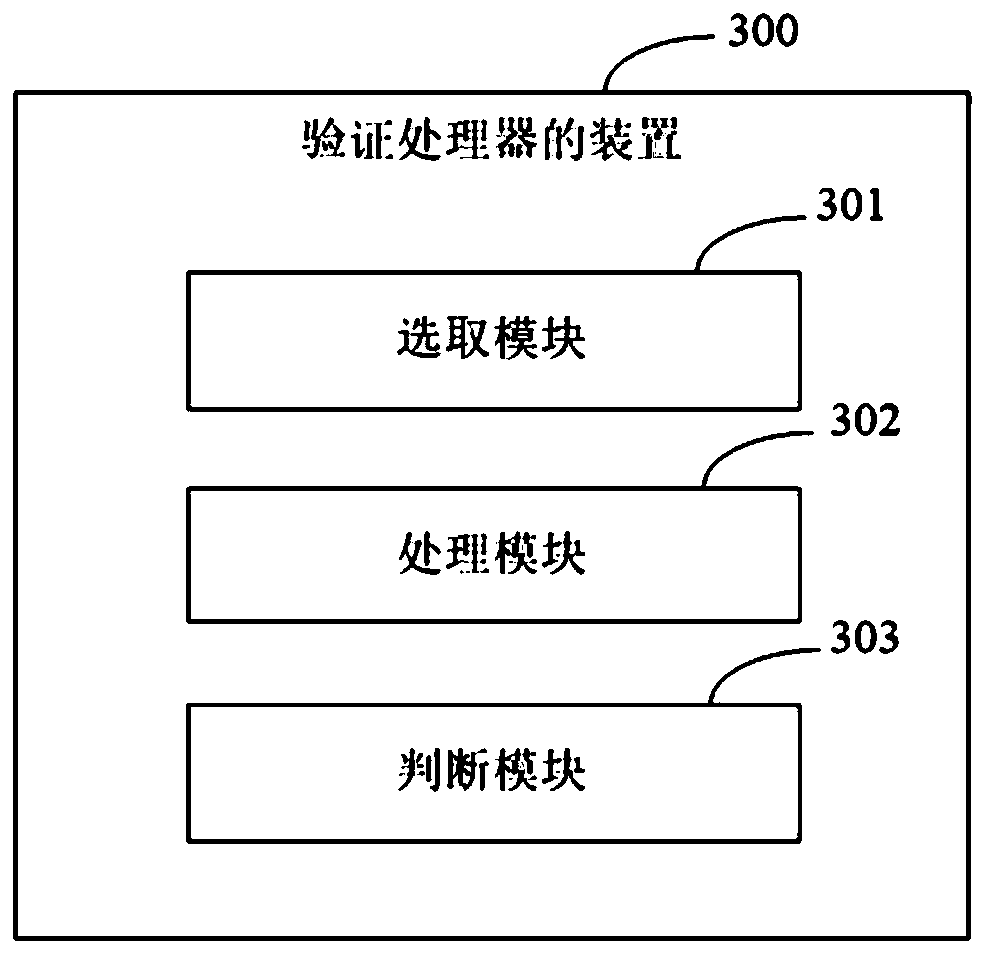
[0062] image 3 It is a schematic structural diagram of the verification processor device provided in Embodiment 3 of the present application. Such as image 3 As shown, the device 300 includes: a selection module 301, a processing module 302 and a judging module 303; wherein,
[0063] The selecting module 301 is configured to select an instruction in the reduced instruction set as the current instruction according to the preset probability of each instruction being selected, perform randomization processing on the current instruction, and add the randomized current instruction to into the instruction queue; repeat the above operations until the number of instructions added to the instruction queue reaches the preset length of the instruction queue;
[0064] The processing module 302 is configured to combine the instructions in the instruction queue into a current instruction sequence, and input the current instruction sequence to the processor to be verified for processing,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com